White House Launches US Cyber Trust Mark for IoT Devices
Japan links 200+ cyberattacks to Chinese group MirrorFace, Prolific voice phishing gang engages in ultra-persuasive scams, License plate recognition system exposes feeds and leaks data, Smartphone location data firm hacked, Data on 8,500 exposed in Casio hack, PowerSchool breached, much more


Please consider supporting Metacurity with an upgraded subscription so that you can continue to receive our daily missives packed with the top infosec developments you should know.
If you can't commit to a subscription today, consider tipping or donating to help keep Metacurity going.
The White House launched the US Cyber Trust Mark, a new cybersecurity safety label for internet-connected consumer devices.
The Cyber Trust Mark label, which will appear on smart products sold in the United States later this year, will help American consumers determine whether the devices they want to buy are safe to install in their homes.
It's designed for consumer smart devices, such as home security cameras, TVs, internet-connected appliances, fitness trackers, climate control systems, and baby monitors, and it signals that the internet-connected device comes with a set of security features approved by the National Institute of Standards and Technology (NIST).
Vendors will label their products with the Cyber Trust Mark logo if they meet the cybersecurity criteria. These criteria include using unique and strong default passwords, software updates, data protection, and incident detection capabilities.
Consumers can scan the QR code included next to the Cyber Trust Mark labels for additional security information, such as instructions on changing the default password, steps for securely configuring the device, details on automatic updates (including how to access them if they are not automatic), the product's minimum support period, and a notification if the manufacturer does not offer updates for the device.
The program was unveiled in July 2023, when major electronics, appliance, and consumer product makers like Amazon, Google, Best Buy, LG Electronics U.S.A., Logitech, and Samsung Electronics announced their participation.
Over the last 18 months, FCC Commissioners unanimously authorized the program. They also adopted final rules and the trademarked, distinct shield logo for Cyber Trust Mark-certified products.
In December 2024, the FCC announced the approval of 11 companies as Cybersecurity Label Administrators, responsible for the program's day-to-day management and certifying the use of the US Cyber Trust Mark label. (Sergiu Gatlan / Bleeping Computer)
Related: FCC.gov, TechCrunch, PYMNTS.com, The White House, NBC News, The Record, CyberScoop, The Verge, Nextgov/FCW, ZDNET, Cyber Daily, Tech Monitor
Japan's National Police Agency (NPA) linked more than 200 cyberattacks targeting the country’s national security and high technology data over the past five years to a Chinese hacking group, MirrorFace, detailing their tactics and calling on government agencies and businesses to reinforce preventive measures.
The agency said its analysis of MirrorFace's cyberattacks from 2019 to 2024, including their targets, methods, and infrastructure, concluded that they were systematic attacks linked to China, which aimed to steal data on Japanese national security and advanced technology.
The NPA said the Chinese government-led cyberattacks targeted Japan’s Foreign and Defense ministries, the country’s space agency, and individuals, including politicians, journalists, private companies, and think tanks related to advanced technology.
MirrorFace sent emails with attachments containing malware to targeted organizations and individuals to view data saved on computers mainly from December 2019 to July 2023, often from Gmail and Microsoft Outlook addresses using stolen identities, the NPA investigation found.
The emails typically used as subjects keywords such as “Japan-US alliance,” “Taiwan Strait,” “Russia-Ukraine war,” and “free and open Indo-Pacific,” and included an invitation for a study panel, references, and a list of panelists, the NPA said.
In another tactic, the hackers targeted Japanese organizations in the aerospace, semiconductors, information, and communications sectors from February to October 2023, exploiting vulnerabilities in virtual private networks to gain unauthorized access to information.
The attacks included one on the Japan Aerospace and Exploration Agency, or JAXA, which acknowledged in June it had suffered a series of cyberattacks since 2023, though sensitive information related to rockets, satellites, and defense was not affected. (Mari Yamaguchi / Associated Press)
Related: The Japan Times, Asahi Shibum, Kyodo News
New details about the internal operations of a prolific voice phishing gang show that the group routinely abuses legitimate services at Apple and Google to force outbound communications to their users, including emails, automated phone calls, and system-level messages sent to all signed-in devices.
A cybercriminal known as “Perm,” a.k.a. “Annie,” rents out the phishing kit. Perm is the current administrator of Star Fraud, one of Telegram's more consequential cybercrime communities and one that has emerged as a foundry of innovation in voice phishing attacks.
Perm posted messages to Star Fraud and other Telegram channels that showed they worked closely with another cybercriminal who went by the handles “Aristotle” and just “Stotle.”
It is unclear what caused the rift, but Stotle turned on his erstwhile business partner, Perm, last year by sharing highly detailed videos, tutorials, and secrets that shed new light on how these phishing panels operate.
When the phishing group settles on a target of interest, the scammers create and join a new Discord channel. This allows each logged-on member to share what is currently on their screen, which is tiled in a series of boxes so that everyone can simultaneously see all other call participant screens.
The spoofed Apple phone number tells the victim they were with Apple’s account recovery team. From there, they engage in a convincing scam, stealing the victim's credentials.
The target lists used by the phishing callers originate mainly from a few crypto-related data breaches, including the 2022 and 2024 breaches involving user account data stolen from cryptocurrency hardware wallet vendor Trezor. (Brian Krebs / Krebs on Security)
Related: Hacker News (ycombinator)
Security researcher Matt Brown discovered a flaw in the automated license-plate-recognition (ALPR) system that collects real-time vehicle data meant to be accessible by law enforcement.
Because of this flaw, more than 150 Motorola ALPR cameras have exposed their video feeds and leaked data in recent months.
As well as broadcasting live footage accessible to anyone on the internet, the misconfigured cameras also exposed data they have collected, including photos of cars and logs of license plates. The real-time video and data feeds don’t require any usernames or passwords to access.
Motorola confirmed the exposures, saying it was working with its customers to close the access. (Matt Burgess and Dhruv Mehrotra / Wired)
Related: alpr leaks on GitHub, 404 Media
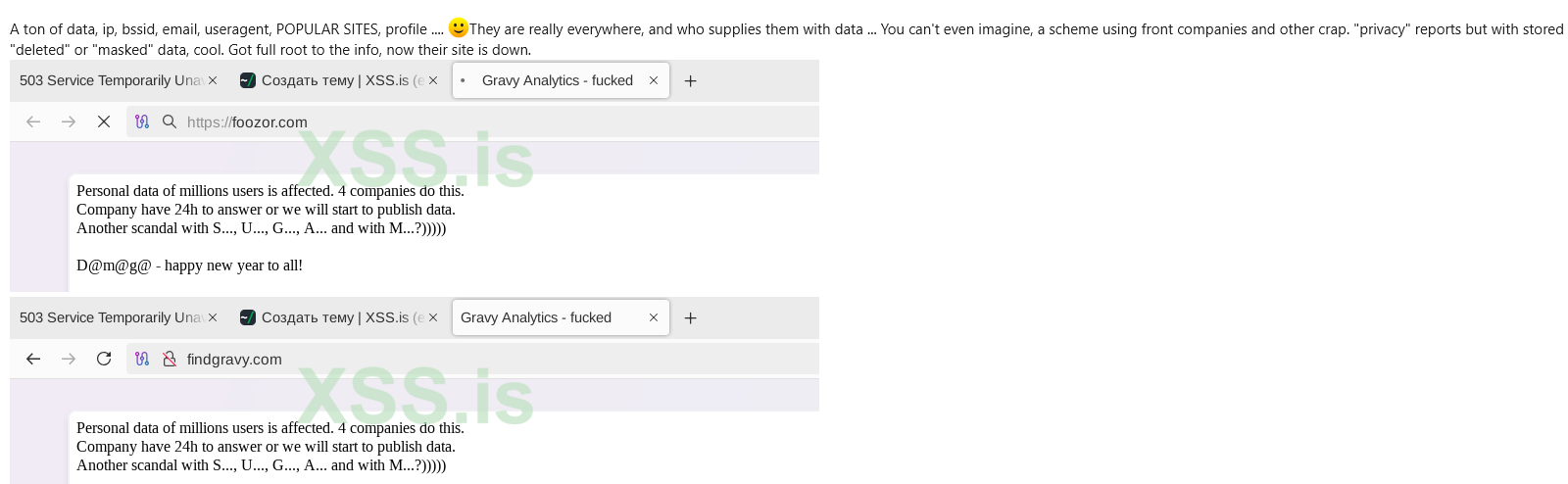
Hackers claim to have compromised Gravy Analytics, the parent company of Venntel, which has sold the US government massive amounts of smartphone location data.
The hackers said they had stolen a massive amount of data, including customer lists, information on the broader industry, and even location data harvested from smartphones, which shows people’s precise movements. They are threatening to publish the data publicly.
In a message posted to two Gravy websites, the hackers wrote, "Personal data of millions of users is affected,” according to screenshots posted on the Russian cybercrime forum XSS. “Company have 24h to answer or we will start to publish data,” the message continues.
The samples of data posted by the hackers include the apparent historical location of smartphones. The files contain precise latitude and longitude coordinates of the phone and the time at which the phone was there. Some screenshots indicate what country the data has been collected from.
A file called “users” in a sample of data the hackers posted includes well-known companies such as Gannett, Uber, Comcast, Apple, LexisNexis, Equifax, and many more. It also specifically mentions Babel Street, which is another US government contractor. (Joseph Cox / 404 Media)
Related: SOCRadar
Japanese electronics manufacturer Casio says that the October 2024 ransomware incident exposed the personal data of approximately 8,500 people.
The affected individuals are primarily Casio employees and business partners, but the exposed data contained a small amount of customer personal information.
The Underground ransomware gang claimed the attack on October 10. They threatened to disclose confidential documents, financial files, project information, and employee data unless a ransom was paid.
Soon after, Casio confirmed that Underground had stolen the personal data of employees, partners, and customers. However, the company did not provide the number of affected people.
The Japanese firm also clarified that they did not negotiate with the cybercriminals. It also said most impacted services have returned to normal operational status, though some services have not yet been recovered. (Bill Toulas / Bleeping Computer)
Related: Casio, TechCrunch, TechRadar, Infosecurity Magazine
Education software giant PowerSchool confirmed it suffered a cybersecurity incident that allowed a threat actor to steal the personal information of students and teachers from school districts using its PowerSchool SIS platform.
In an unusual twist, PowerSchool confirmed that this was not a ransomware attack but that they did pay a ransom to prevent the data from being released.
While the company's products are known mainly by school districts and their staff, PowerSchool also operates Naviance, a platform used by many K-12 districts in the US to offer personalized college, career, and life readiness planning tools to students.
In a notification sent to customers, PowerSchool says they first became aware of the breach on December 28, 2024, after PowerSchool SIS customer information was stolen through its PowerSource customer support platform, which is a student information system (SIS) used to manage student records, grades, attendance, enrollment, and more.
After investigating the incident, it was determined that the threat actor accessed the portal using compromised credentials and stole data using an "export data manager" customer support tool.
Using this tool, the attacker exported the PowerSchool SIS 'Students' and 'Teachers' database tables to a CSV file, which was then stolen.
For those impacted, PowerSchool is offering credit monitoring services to impacted adults and identity protection services for impacted minors.
PowerSchool says its operations remain unaffected, and services continue as usual despite the breach. (Lawrence Abrams / Bleeping Computer)
Related: Local3News
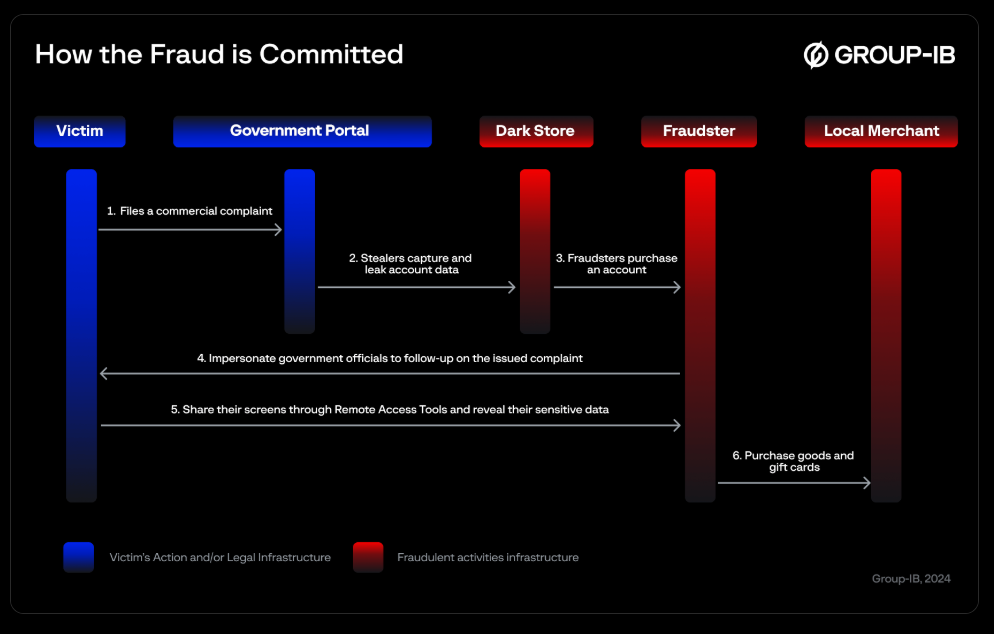
Researchers at Group-IB uncovered a sophisticated, multi-stage fraud campaign designed to trick consumers who have submitted customer complaints about goods or services to an official government portal into sharing their card details.
The fraudsters purchased on the dark web logins to government accounts originally obtained via infostealers.
Impersonating government officials, they claim to be able to help the victim process a refund, persuading them to download remote access software to their mobile device to streamline the process.
The scheme, which Group-IB said targets consumers in the Middle East, is highly effective because it uses real customer information to engineer the victim socially.
Victims are usually female consumers with limited technology expertise. Group-IB says that scammers typically cash out their proceeds by making 3D-secure purchases of products or gift vouchers from e-tailers or recharging e-wallets.
Given the sophistication of the campaign, organized crime groups are the likely perpetrators. (Phil Muncaster / Infosecurity Magazine)
Related: Group-IB
watchTowr researchers report that more than 4,000 unique backdoors are using expired domains or abandoned infrastructure, and many of these expose government and academia-owned hosts, setting these hosts up for hijacking by criminals.
The new findings follow the watchTowr crew's earlier research, delving into abandoned and expired infrastructure. But in this case, the team also examined how the "bad guys" throw away internet domains.
They also highlight how attackers have historically backdoored the web shells they provide to other miscreants, thus giving the original author of the web shell access to everything that the current user touches.
These backdoored backdoors run the gamut from basic web shells to c99shell, r57shell, and China Chopper, to name a few of the "web shells that include functions to allow hackers to hack hackers.
The researchers registered over 40 domains (a list of several of these web shells and associated domains is listed in the report), spun up new infrastructure, and then logged incoming requests before responding with a 404 error message.
The team logged "thousands" of requests, primarily across a handful of the domains the researchers identified and re-registered.
After slogging through logs of incoming requests to watchTowr's newly accrued domains, the researchers found "multiple" compromised government-owned hosts from Bangladesh, China, Nigeria, and other countries, as well as higher-education entities across Thailand, China, and South Korea. (Jessica Lyons / The Register)
Related: watchTowr
Federal Communications Commission Chairwoman Jessica Rosenworcel called on her colleagues to "quickly" adopt rules allowing the US regulator to stage a radio spectrum auction, the proceeds of which would fund the removal from American networks of equipment made by Chinese vendors Huawei and ZTE.
Work to remove and replace the kit with less risky equipment has been underway since 2021, when $1.9 billion was allocated to a “Rip and Replace” program that Congress authorized because Chinese-made devices posed a national security risk.
In 2024, it emerged that the program saw just 12 percent of telcos and ISPs remove Chinese gear from their networks and that at least another $3 billion is needed to finish the job.
To address this shortfall, the Spectrum and Secure Technology and
Innovation Act, signed into law as part of the NDAA on December 23, 2024, expressly allowed the FCC to borrow up to $3.08 billion from the Treasury Department to fund the Rip and Replace Program fully.
This loan will then be repaid with the proceeds of the AWS-3 auction, for which the FCC is now considering proposed rules. (Jessica Lyons / The Register)
Related: FCC, Telecoms.com, Capacity Media, Data Center Dynamics
On December 30, 2024, Rivers Casino Philadelphia filed a notice of data breach with the Attorney General of Massachusetts after discovering that an unauthorized party accessed confidential information in the company’s possession.
Rivers Casino explains that the incident resulted in an unauthorized party accessing consumers’ sensitive information, including their names, Social Security numbers, and bank account information.
Upon completing its investigation, Rivers Casino began sending out data breach notification letters to all individuals whose information was affected by the recent data security incident. (JD Supra)
Related: CDC Gaming, 6ActionNews, CBS News, Philadelphia Inquirer, Play Pennsylvania
On January 8, 2025, PeckShieldAlert reported a significant security breach at 0xOrangeFinance, where approximately $787,000 worth of cryptocurrencies were drained from its smart contracts.
The breach was detected early in the morning, and users were immediately warned to avoid interacting with any of Orange Finance's compromised protocols. The security firm emphasized the urgency of revoking all contract approvals linked to Orange Finance to prevent further unauthorized access and potential losses.
The drained amount represents a significant portion of the platform's liquidity, which could lead to decreased trading volumes and affect the market's overall liquidity depth. The immediate impact on trading pairs associated with Orange Finance is expected to be severe, with potential price volatility as investors react to the news. (Blockchain News)
Related: crypto.news, Chain Catcher
More than 800 “potential vulnerabilities and biases” were uncovered by a Pentagon effort to spot problems with using large language models in military medical services.
The Chief Digital and Artificial Intelligence Office, or CDAO, said the initiative was conducted through its Crowdsourced AI Red-Teaming Assurance Program, with help from the Program Executive Office, Defense Healthcare Management Systems, and the Defense Health Agency.
It was conducted by the technology nonprofit Humane Intelligence.
CDAO’s LLM pilot focused on identifying potential system weaknesses and flaws when using emerging tools for clinical note summarization and a medical advisory chatbot. DOD said more than 200 people, including clinical providers and healthcare analysts within the department, participated in the red teaming effort, which “compared three popular LLMs.” (Edward Graham / DefenseOne)
Related: Defense.gov
The hacker group Silent Crow claims to have breached Russia’s Federal Service for State Registration, Cadastre, and Cartography (Rosreestr) and published what it says is a fragment of the agency’s database.
The Telegram channel Information Leaks, one of the first to report the hack, stated that the leaked portion contains nearly 82,000 records with personal details, including names, birth dates, addresses, phone numbers, emails, SNILS numbers (similar to Social Security numbers), and Rosreestr IDs of Russian citizens.
An anonymous Telegram channel called Silent Crow, created in late December posted about the breach on January 6. The group claims the published fragment includes around 90,000 entries from Russia’s Unified State Register of Real Estate.
“Rosreestr has become a vivid example of how large state structures can fall in just a few days. As a result, their data, supposedly well-protected, has joined our collection,” the post said. (Meduza)
Related: UNN
Best Thing of the Day: Not Quite a Sanction But Enough to Give Banks Pause
Wall Street banks hoping to participate in Chinese battery maker CATL's secondary market listing in Hong Kong are recalculating their risk-to-reward ratios now that the Pentagon has officially banned the company's products.
Worst Thing of the Day: The Guy Who Fact-Checked Mr. Robot Needs Your Help
Marc Rogers, DEF CON's head of security, faces tens of thousands of dollars in medical bills following an accident that left him with a broken neck and temporary quadriplegia. His friends have established a GoFundMe page to help Rogers cope with the unfair and massively cruel US healthcare system.
Closing Thought
Bonus Closing Thought