US Sanctions Chinese Cybersecurity Company, Employee for Ragnarok Ransomware Attacks
Europol takes down 27 booters, Microsoft issues patches for at least 70 flaws, AI-generated videos were used to target European audiences, BadRAM undercuts AMD's security promises, The average container has 604 vulnerabilities, Cyberattack disrupts Krispy Kreme's online operations, much more


In a first, CSO Online published two of my pieces on the same day.
The first examines how Salt Typhoon poses a serious supply chain risk to most organizations, with China exfiltrating massive amounts of data, especially voice calls that can be stored for later use in deepfake campaigns.
The second piece delves into bug bounty programs and explains how they can deliver significant benefits, but only for organizations that are ready for them.
Check out both articles!
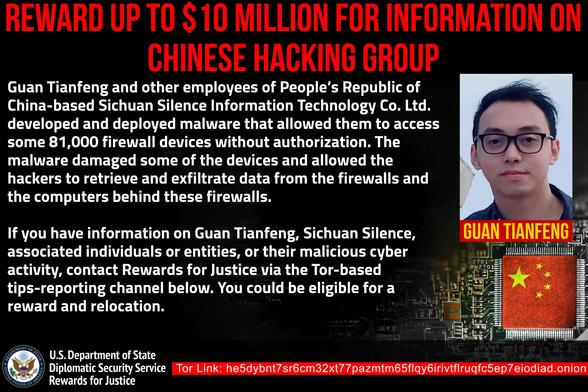
The US Treasury Department sanctioned Chinese cybersecurity company Sichuan Silence and one of its employees, Guan Tianfeng, for their involvement in a series of Ragnarok ransomware attacks targeting US critical infrastructure companies and many other victims worldwide in April 2020.
According to the Department's Office of Foreign Assets Control (OFAC), Sichuan Silence is a Chengdu-based cybersecurity government contractor that provides products and services to core clients, such as China's intelligence services.
OFAC says the zero-day used in the April 2020 campaign was discovered by security researcher and Sichuan Silence employee Guan Tianfeng (also known as GbigMao) in an unnamed firewall product.
According to the Department's Office of Foreign Assets Control (OFAC), Sichuan Silence is a Chengdu-based cybersecurity government contractor (recently profiled by the Natto Thoughts team) that provides products and services to core clients, such as China's intelligence services.
The US Department of Justice (DOJ) also unsealed an indictment on Guan, and the US State Department announced a reward offer of up to $10 million for information about Sichuan Silence or Guan through its Rewards for Justice program.
The Department of State and the DOJ confirmed that the April 2020 Ragnarok ransomware campaign exploited a zero-day SQL injection vulnerability (CVE-2020-12271) in Sophos XG firewalls.
The attackers initially used zero-day exploits to obtain remote code execution on Sophos XG firewalls and installed ELF binaries and scripts as part of a malicious toolkit known as Asnarök Trojan.
After Sophos detected the attacks, it patched the devices and removed the malicious scripts using a hotfix. However, the threat actors activated a 'dead man switch' that would have triggered a Ragnarok ransomware attack on Windows machines on the victims' networks.
As a result of the sanctions, US organizations and citizens are prohibited from engaging in transactions with Guan and Sichuan Silence. Also, any U.S.-based assets tied to them will be frozen, and U.S. financial institutions or foreign entities transacting with them will also expose themselves to penalties. (Sergiu Gatlan / Bleeping Computer)
Related: OFAC, Treasury Department, Justice Department, State Department, PCMag, TechCrunch, The Record, CyberScoop, Reuters, Al Jazeera, Bloomberg, BankInfoSecurity.com, UPI, AFP, Help Net Security, The Register, IT News, Security Week, Infosecurity Magazine, TechRadar, Natto Thoughts, PYMNTS
Europol and various other law enforcement agencies announced they have successfully conducted Operation PowerOFF, which took 27 DDoS "booter" or "stressor" platforms offline.
Some websites that were taken down include zdstresser.net, orbitalstress.net, and starkstresser.net.
Alongside the takedown of 27 platforms, three administrators in France and Germany were arrested, actions were taken against several users, and a further 300 users were identified.
Europol is also taking proactive measures, such as Google search ads and YouTube ads targeted at those looking for DDoS-for-hire tools or tutorials on conducting a DDoS attack.
In addition to these measures, more than 250 warning letters, over 2,000 emails, and knock-and-talks will be used to deter users of illegal online services.
This operation coordinated by Europol involved 15 separate countries, including Australia, Brazil, Canada, Finland, France, Germany, Japan, Latvia, The Netherlands, Poland, Portugal, Sweden, Romania, the UK, and the US. (Niamh Ancell / Cybernews)
Related: Europol
On this month's Patch Tuesday, Microsoft released updates to plug at least 70 security holes in Windows and Windows software, including one vulnerability already exploited in active attacks.
The zero-day seeing exploitation involves CVE-2024-49138, a security weakness in the Windows Common Log File System (CLFS) driver, which applications use to write transaction logs — that could let an authenticated attacker gain “system”-level.
Elevation of privilege vulnerabilities accounted for 29% of the 1,009 security bugs Microsoft has patched so far in 2024, according to a year-end tally by Tenable; nearly 40 percent of those bugs were weaknesses that could let attackers run malicious code on the vulnerable device.
Tyler Reguly at the security firm Fortra had a slightly different 2024 patch tally for Microsoft, at 1,088 vulnerabilities, which he said was surprisingly similar to the 1,063 vulnerabilities resolved in 2023 and the 1,119 vulnerabilities resolved in 2022. (Brian Krebs / Krebs on Security)
Related: Bleeping Computer, Petri, Neowin, The Register, Dark Reading, Security Week, Help Net Security, Cyberscoop, r/sysadmin, Tenable, Ask Woody, SANS Internet Storm Center, Rapid7, The Stack, Infosecurity Magazine

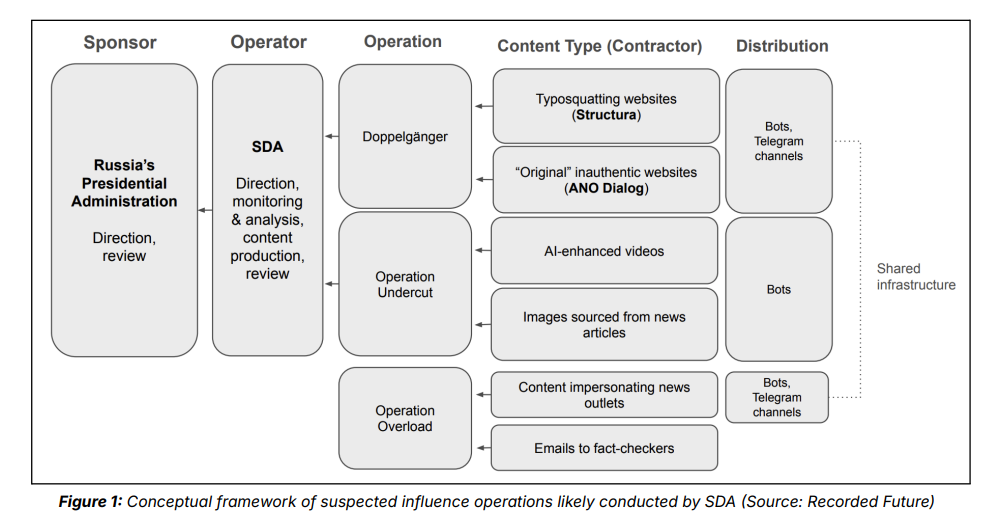
Researchers at Recorded Future documented a Russian-tied campaign designed to undermine Europe’s support for Ukraine, dubbed “Operation Undercut,” that prominently used AI-generated voiceovers on fake or misleading “news” videos.
The videos, produced by Russia's Social Design Agency (SDA), which targeted European audiences, attacked Ukrainian politicians as corrupt or questioned the usefulness of military aid to Ukraine, among other themes. For example, one video touted that “even jammers can’t save American Abrams tanks,” referring to devices used by US tanks to deflect incoming missiles, reinforcing the point that sending high-tech armor to Ukraine is pointless.
The report states that the video creators “very likely” used voice-generated AI, including ElevenLabs tech, to make their content appear more legitimate. To verify this, Recorded Future’s researchers submitted the clips to ElevenLabs’ AI Speech Classifier, which allows anyone to “detect whether an audio clip was created using ElevenLabs” and got a match. (Charles Rollet / TechCrunch)
Related: Recorded Future
Sponsor Message

In today's digital landscape, protecting your software supply chain from rising threats is essential. This free whitepaper offers five key strategies for enhancing container security, one of the main attack surfaces in dynamic software development practices. Learn about using SBOMs for transparency, shifting vulnerability detection left, and automating policy enforcement, all for a superior developer experience and securing third-party code.
Interested in reaching the elite audience of cybersecurity decision-makers, public policy professionals, and journalists who read Metacurity? Send an email to info [at] Metacurity.com with the subject line "Sponsorship."
An international team of researchers from KU Leuven, the University of Lübeck, and the University of Birmingham unveiled BadRAM, a proof-of-concept attack that completely undermines security assurances that chipmaker AMD makes to users of one of its most expensive and well-fortified microprocessor product lines.
Starting with the AMD Epyc 7003 processor, a feature known as SEV-SNP, short for Secure Encrypted Virtualization and Secure Nested Paging, has provided the cryptographic means for certifying that a VM hasn’t been compromised by any backdoor installed by someone with access to the physical machine running it.
If a VM has been backdoored, the cryptographic attestation will fail, and the VM admin will be immediately alerted of the compromise. Or at least that’s how SEV-SNP is designed to work.
BadRAM is an attack that a server admin can carry out in minutes, using either about $10 of hardware or, in some cases, software only, to cause DDR4 or DDR5 memory modules to misreport the memory capacity they have during bootup. From then on, SEV-SNP will be permanently made to suppress the cryptographic hash, attesting to its integrity even when the VM has been badly compromised. (Dan Goodin / Ars Technica)
Related: BadRAM, The Register, Help Net Security, The Record, Fudzilla, PC Perspective, Heise Online
According to researchers at NetRise, the average software container has 604 known vulnerabilities in its underlying software components, with over 45% being 2 to 10-plus years old.
NetRise says 7.9% of vulnerabilities encountered by the cybersecurity firm were over five years old, while 4.2% of vulnerabilities deemed ‘Critical’ or ‘High’ were additionally classified as ‘weaponized’ and actively exploited in real-world attacks.
NetRise utilized an advanced Software Bill of Materials (SBOM) approach, generating detailed SBOMs for 70 randomly selected container images from Docker Hub’s most downloaded repositories. This method enabled the firm to identify all software components within each container, including third-party libraries and dependencies.
The study’s risk assessment evaluated known vulnerabilities (CVEs) and non-CVE risks, such as outdated components and misconfigurations. Vulnerability prioritization was carried out using Common Vulnerability Scoring System (CVSS) rankings, focusing on weaponized vulnerabilities that are actively exploited in the wild. (Swagath Bandhakavi / TechMonitor)
Related: NetRise, Industrial Cyber, Help Net Security
In an SEC filing, doughnut chain Krispy Kreme said that unauthorized activity on a portion of its information technology systems has disrupted certain operations, including online ordering in the United States.
After being notified of the incident on Nov. 29, the company has initiated an investigation and is working with external cybersecurity experts to mitigate the impact. (Denny Jacob / Marketwatch)
Related: Krispy Kreme, Financial Times, CNN, Marketwatch
Cybersecurity startup Astrix Security raised $45 million in a Series B venture funding round.
Menlo Ventures led the round through the Anthology Fund, a strategic partnership between Menlo and Anthropic, the AI company behind Claude. Other participants included Workday Ventures, the global HR software leader, and existing investors such as Bessemer Venture Partners, CRV, and F2 Venture Capital. (Meir Orbach / Calcalist)
Related: PR Newswire, Silicon Angle, FinSMEs, BankInfoSecurity, Globes, FinTech Global
Best Thing of the Day: Would It Be Wrong to Say It's About Time?
After its customers succumbed to devastating breaches of their accounts on cloud-based storage company Snowflake's servers, Snowflake says it will enforce multi-factor authentication for all its customers by August 2025.
Worst Thing of the Day: Our AI Overlords Apparently Like Murderous Teens
A chatbot hosted by Character.ai told a 17-year-old that murdering his parents was a "reasonable response" to them limiting his screen time, a lawsuit filed in a Texas court claims.
Closing Thought