US Indicts 14 DPRK Fake IT Workers, Offers $5 Million Reward
Cops seize Rydox cybercrime market, Spanish & Peruvian cops scuttle big vishing scam, German cops sinkhole 30K BadBox-infected devices, BEC scammer extradited from S. Africa, Amazon delays MSFT cloud due to Midnight Blizzard, Yahoo lays off 25% of cyber team, Recalls saves sensitive data, much more


Sponsor Message

In today's digital landscape, protecting your software supply chain from rising threats is essential. This free whitepaper offers five key strategies for enhancing container security, one of the main attack surfaces in dynamic software development practices. Learn about using SBOMs for transparency, shifting vulnerability detection left, and automating policy enforcement, all for a superior developer experience and securing third-party code.
Interested in reaching the elite audience of cybersecurity decision-makers, public policy professionals, and journalists who read Metacurity? Send an email to info [at] Metacurity.com with the subject line "Sponsorship."
The US offered a $5 million reward for information about an alleged scheme in which North Korean technology workers got jobs at unsuspecting US companies and then stole their trade secrets for ransom, with the proceeds used to fund Pyongyang's weapons programs.
The US State Department said about 130 North Korean workers got IT jobs at US companies and nonprofits from 2017 to 2023 and generated at least $88 million that Pyongyang used for weapons of mass destruction.
The US said that part of the total was the workers' compensation from the employers, which ultimately went to the North Korean government.
The companies were not identified. The State Department said it sought information on two sanctioned North Korean companies, China-based Yanbian Silverstar Network Technology, and Russia-based Volasys Silverstar, that it handled the workers.
The US Justice Department announced indictments of fourteen North Koreans accused of operating and working for the two companies as part of the scheme.
Operating from either China or Russia, the workers stole sensitive company information, including proprietary source computer code, and threatened to leak it unless the employer made an extortion payment, the government said. The 14 people were charged with wire fraud, money laundering, and identity theft, among other offenses. (Susan Heavey and AJ Vicens / Reuters)
Related: Justice.gov, State Department, Cyberscoop, Euronews, NK News, Associated Press, Bleeping Computer, The Record, Security Week, The Register, UPI, BBC News
Albanian law enforcement seized the Rydox cybercrime marketplace and arrested three administrators in collaboration with international partners.
Kosovo nationals Ardit Kutleshi, Jetmir Kutleshi, and Shpend Sokoli were arrested by Kosovo law enforcement and Albania's Special Anti-Corruption Body (SPAK). The US Justice Department indicted the first two for involvement in Rydox's operations, and they're awaiting extradition to the United States.
Ardit Kutleshi and Jetmir Kutleshi face multiple charges related to their Rydox admin roles, including two counts of identity theft, conspiracy to commit identity theft, aggravated identity theft, access device fraud, and money laundering. If convicted, each could receive five years for each charge, 10 years for access device fraud, and up to 20 years for money laundering.
Since February 2016, Rydox marketplace sellers have been involved in over 7,600 sales of credit card information, login credentials, and personal information such as social security numbers, names, and addresses stolen from thousands of U.S. citizens and various cybercrime tools and devices.
Rydox also offered for sale over 321,000 other "cybercrime products" to more than 18,000 users, including tools and materials for committing cyber crimes, such as tutorials and spam tools.
According to the indictment, registered users had to deposit a sum of cryptocurrency into their accounts before making a purchase via Perfect Money, Ethereum, Litecoin, Bitcoin ("BTC"), Monero, Ripple, Tron, or Verge payments deposited into a cryptocurrency wallet controlled by Rydox.
They could use the funds to purchase illicit products, services, tools, and programs from Rydox sellers. However, once the funds were deposited, they were under the defendants' control, who controlled the Rydox cryptocurrency wallets.
The operation was carried out with the help of the FBI's Pittsburgh Office, Albania's National Bureau of Investigation (BKH), the Albanian Directorate of Cybercrime Investigation, the Kosovo Special Prosecutor's Office, the Kosovo Police, and the Malaysian Royal Police. (Sergiu Gatlan / Bleeping Computer)
Related: Spak.gov.al, Justice.gov, Cyberscoop, Soyacincau, Balkan Insight, Albanian Daily News, Pamfleti, CNA.al
Spanish police, working with colleagues in Peru, conducted a simultaneous crackdown on a large-scale voice vishing scam ring in the two countries, arresting 83 individuals.
Thirty-five of the arrested people were located across Spain, including in Madrid, Barcelona, Mallorca, Salamanca, and Vigo, and another 48 were arrested in Peru.
The ringleader was also apprehended in Spain during the 29 simultaneous raids conducted by the cooperating police forces, which seized cash, mobile phones, computers, and documents.
According to the Spanish police (Policia Nacional), the scammers operated a large call operation that employed 50 people in three distinct call centers, defrauding at least 10,000 people and making €3,000,000 ($3.15M) in proceeds.
The calling agents used stolen databases, pre-written social engineering, and scripts to trick the call recipients into giving away their sensitive banking information.
To make the calls appear legitimate, the agents used caller spoofing technology, making their number and caller name match those of the official bank they impersonated, adding credibility to the process.
The bait was an alert about unauthorized ATM withdrawals, directing victims to go through a process of fake account verification and give away their one-time passcodes.
Once the cash was withdrawn, the operators kept about 20% and 30%, and the rest was sent to the organization in Peru. (Bill Toulas / Bleeping Computer)
Related: Policia Nacional
The German Federal Office for Information Security ( BSI ) said it was able to disrupt and sinkhole around 30,000 devices infected with the BadBox malware across Germany, including digital picture frames or media players equipped with the malware at the factory.
BSI said that in all cases known to it, the BadBox malware was already installed on the respective devices, which typically have outdated Android versions, at the time of purchase.
BadBox can create undetected accounts for email and messenger services, which can be used to spread fake news. The malware also has a built-in function for advertising fraud; it can surf websites in the background.
It can also serve as a so-called residential proxy, which usually allows criminals to disguise its origin, enabling cyberattacks or the distribution of illegal content.
The BSI has now been able to block communication between infected devices and control servers with a sinkholing measure, registering the domains used for malware communication and redirecting the messages to its servers. (Dirk Knop / Heise Online)
Related: BSI, Cybernews, Security Week
The US Justice Department announced that Afeez Akinloye, a 42-year-old Nigerian, was extradited from South Africa to Nebraska for defrauding real estate buyers and sellers of nearly $2 million.
Akinloye appeared in a Nebraska court to face conspiracy charges for committing wire fraud and access device fraud.
Between September 2016 and June 2017, Akinloye allegedly participated in a business email compromise (BEC) scheme related to real estate transactions.
During the stated period, the Nigerian and other members of his gang took advantage of their insider knowledge of real estate transactions.
They sent fraudulent emails to their unsuspecting victims, instructing them to wire funds to accounts they could easily access, defrauding them of nearly $2 million. (Foundation for Investigative Journalism)
Related: Justice.gov, The Street Journal, Tori Newsconspiracy charges
Amazon delayed the deployment of Microsoft's cloud-based Office suite for a year as the two companies worked to resolve Amazon's concerns about the security of the bundle of email and productivity software.
Amazon paused the rollout after Microsoft discovered Russia-linked hacker group Midnight Blizzard had gained access to some of its employees’ email accounts. After conducting its own analysis of the software, Amazon asked for changes to guard against unauthorized access and create a more detailed accounting of user activity in the apps, some of which Microsoft also markets as Office 365.
“We deep-dived into O365 and all of the controls around it and we held – just as we would any of our service teams within Amazon – we held them to the same bar,” said CJ Moses, Amazon’s chief information security officer. Moses’s team gave Microsoft security chief Charlie Bell – a former Amazon engineering executive – a list of requested enhancements, and engineers from both companies have spent months working on those changes.
“We believe we’re in a good place to start redeployment next year,” Moses said in an interview last week at Amazon Web Services’ re:Invent conference. (Matt Day / Bloomberg)
Related: WinBuzzer, Runtime, Techzine, Channelnews
In this generous giving season, please consider supporting Metacurity with an upgraded subscription. Thank you
Yahoo laid off around 25% of its cybersecurity team, known as The Paranoids, over the last year.
The company has laid off or lost through attrition 40 to 50 people from a total of 200 employees in the cybersecurity team since the start of 2024, according to multiple current and former Yahoo employees.
The Paranoids are not the only team affected by the layoffs. Valeri Liborski, who was appointed Yahoo’s chief technology officer in September, sent an email this week to employees announcing changes across the broader technology unit, including enterprise productivity and core services. (Zack Whittaker / TechCrunch)
Related: Slashdot
Microsoft’s Recall feature, which recently made its way back to Windows Insiders after having been pulled from test builds back in June due to security and privacy concerns, captures credit card numbers, usernames, and passwords typed into a Windows Notepad window despite having filters that are supposed to prevent it from recording any app or website that is showing credit card numbers, social security numbers, or other important financial or personal information.
It also captured an HTML web page that explicitly asked users to " enter their credit card number below.” The form had fields for credit card type, number, CVC, and expiration date.
However, Recall refused to capture the credit card fields on the payment pages of two online stores, Pimoroni and Adafruit. (Avram Piltch / Tom's Hardware)
Related: Windows Copilot News, Windows Copilot News, Laptop Mag, XDA Developers, The Verge, Tom's Guide, Digital Trends, WinBuzzer, Hacker News, r/pcmasterrace, r/privacy, r/technology, r/Windows11, Slashdot
Researchers at WPScan say that hackers are exploiting a critical vulnerability in the "Hunk Companion" plugin to install and activate other plugins with exploitable flaws directly from the WordPress.org repository.
By installing outdated plugins with known vulnerabilities with available exploits, the attackers can access a large pool of flaws that lead to remote code execution (RCE), SQL injection, cross-site scripting (XSS) flaws, or create backdoor admin accounts.
According to WordPress.org stats, Hunk Companion is currently used by over 10,000 WordPress sites, so it's a relatively niche tool in the space.
The critical vulnerability was discovered by WPScan researcher Daniel Rodriguez and is tracked as CVE-2024-11972. The flaw allows the arbitrary installation of plugins using unauthenticated POST requests.
WPScan reported it to Hunk Companion, with a security update addressing the zero-day flaw released yesterday. (Bill Toulas / Bleeping Computer)
Related: WPScan, Ars Technica, Security Week, TechRadar
Byte Federal, one of the biggest Bitcoin ATM operators in the United States, suffered a significant data breach that potentially affected 58,000 customers.
Florida-based Byte Federal submitted a filing with Maine’s attorney general, reporting a security breach resulting in unauthorized access to its clients’ data.
Byte Federal said it discovered the attack on Nov. 18, more than 30 days after it occurred on Sept. 30. A bad actor exploited a vulnerability in software provided by a third party.
After detecting the incident, the Bitcoin ATM operator immediately shut down its platform and assured customers that no user assets or funds had been compromised.
Byte Federal said that the bad actor attempted to gain unauthorized access to the personal information of as many as 58,000 customers, including 111 Maine residents.
The potentially exposed data included names, dates of birth, addresses, phone numbers, email addresses, government-issued IDs, social security numbers, transaction activity, and photographs of users.
Following the breach, Byte Federal performed a hard reset on all customer accounts, sending a notice of the incident.
The platform has also updated its internal passwords, password management system, tokens, and keys to prevent any further unauthorized access. The firm also urged customers to reset their login credentials and said they may be asked to verify their personal data and confirm their identities for their protection. (Helen Partz / Cointelegraph)
Related: Office of the Maine Attorney General, ByteFederal, CCN, Crypto News Flash, Bleeping Computer, Crypto Basic, TechCrunch
Claroty's Team82 researchers report that Iranian threat actors are utilizing a new malware named IOCONTROL to compromise Internet of Things (IoT) devices and OT/SCADA systems used by critical infrastructure in Israel and the United States.
Routers, programmable logic controllers (PLCs), human-machine interfaces (HMIs), IP cameras, firewalls, and fuel management systems are among the targeted devices.
The malware's modular nature allows it to compromise various devices from various manufacturers, including D-Link, Hikvision, Baicells, Red Lion, Orpak, Phoenix Contact, Teltonika, and Unitronics.
The researchers say it's a nation-state cyberweapon that can cause significant disruptions in critical infrastructure.
Given the ongoing geopolitical conflict, IOCONTROL is currently used to target Israel and U.S. systems, like Orpak and Gasboy fuel management systems.
The tool is reportedly linked to an Iranian hacking group known as CyberAv3ngers, who have shown interest in attacking industrial systems. OpenAI also recently reported that the threat group uses ChatGPT to crack PLCs, develop custom bash and Python exploit scripts, and plan its post-compromise activity. (Bill Toulas / Bleeping Computer)
Related: Claroty, Industrial Cyber, Security Week, Infosecurity Magazine
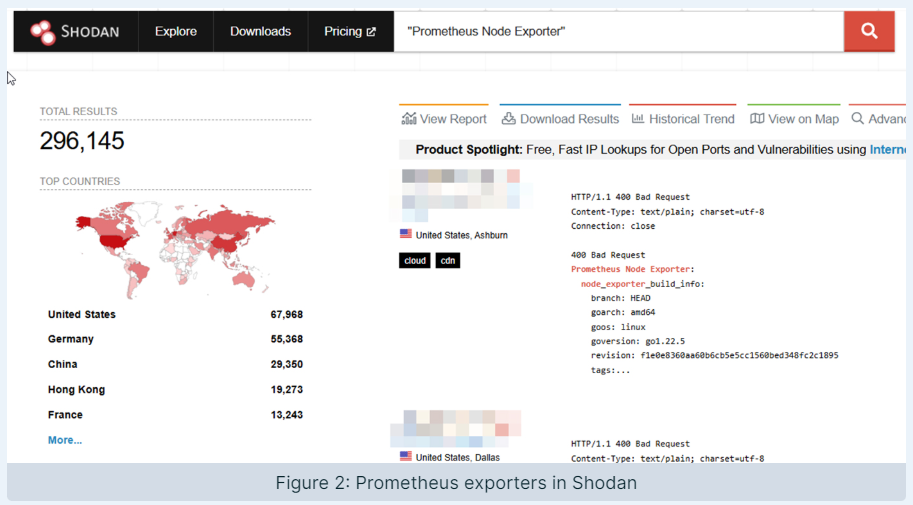
Aqua Security researchers discovered hundreds of thousands of servers running Prometheus open source monitoring software on the open Web are exposing passwords, tokens, and opportunities for denial of service (DoS) and remote code execution.
Prometheus is used widely by organizations to monitor the performance of their applications and cloud infrastructure. However, as noted in its documentation, "It is presumed that untrusted users have access to the Prometheus HTTP endpoint and logs. They have access to all time series information in the database, plus various operational/debugging information."
Many users are apparently either unaware of the ways in which Prometheus is exposed by default or don't realize the value of the data that's exposed along the way. Using Shodan, researchers from Aqua Nautilus discovered more than 40,000 exposed Prometheus servers and more than 296,000 exposed "exporters."
The researchers found sensitive data in those servers and exporters and opportunities for "repojacking" and DoS attacks. The researchers found sensitive data in those servers and exporters and opportunities for "repojacking" and DoS attacks.
Users can protect their Prometheus servers and exporters by taking them offline or adding a layer of authentication to keep out prying eyes and using tools designed to mitigate DoS risks. (Nate Nelson / Dark Reading)
Related: Aquasec
Software company Cleo urged companies to implement security updates for a zero-day flaw in its LexiCom, VLTransfer, and Harmony software, which is currently exploited in data theft attacks.
The company patched a pre-auth remote code execution vulnerability (CVE-2024-50623) in its managed file transfer software and recommended that "all customers upgrade immediately." But, Huntress security researchers first spotted evidence of attacks targeting fully patched Cleo software.
There was a notable increase in activity on Sunday, December 8, after attackers quickly discovered a CVE-2024-50623 bypass (with no CVE-ID) that lets them import and execute arbitrary bash or PowerShell commands by exploiting the default Autorun folder settings.
This zero-day bug is now being exploited in ongoing attacks linked by cybersecurity expert Kevin Beaumont to the Termite ransomware gang, which recently claimed the breach of software as a service (SaaS) provider Blue Yonder. (Sergiu Gatlan / Bleeping Computer)
Related: Cleo, The Record, Help Net Security, Security Week, CSO Online
Researchers at automotive security firm PCAutomotive discovered multiple vulnerabilities in the infotainment units used in some Skoda cars that could allow malicious actors to remotely trigger certain controls and track the cars’ location in real time.
The firm unveiled twelve new security vulnerabilities impacting the latest Skoda Superb III sedan model at Black Hat Europe this week.
The vulnerabilities could be chained together and exploited by hackers to inject malware into the vehicle. An attacker would need to connect with the Skoda Superb III’s media unit via Bluetooth to exploit the flaws, but the attack can be performed within 10 meters without authentication.
The vulnerabilities discovered in the vehicle’s MIB3 infotainment unit could allow attackers to execute unrestricted code and run malicious code every time the unit starts. This could let an attacker obtain live vehicle GPS coordinates and speed data, record conversations via the in-car microphone, take screenshots of the infotainment display, and play arbitrary sounds in the car/
The vulnerable MIB3 units are used in multiple Volkswagen and Skoda models, and based on public sales data, estimates there are potentially more than 1.4 million vulnerable vehicles out there.
A Skoda spokesperson said: “The reported vulnerabilities in the infotainment system have been and are being addressed and eliminated through continuous improvement management via the lifecycle of our products. At no time was and is there any danger to the safety of our customers or our vehicles.” (Carly Page / TechCrunch)
Related: Black Hat Europe, Digit.in
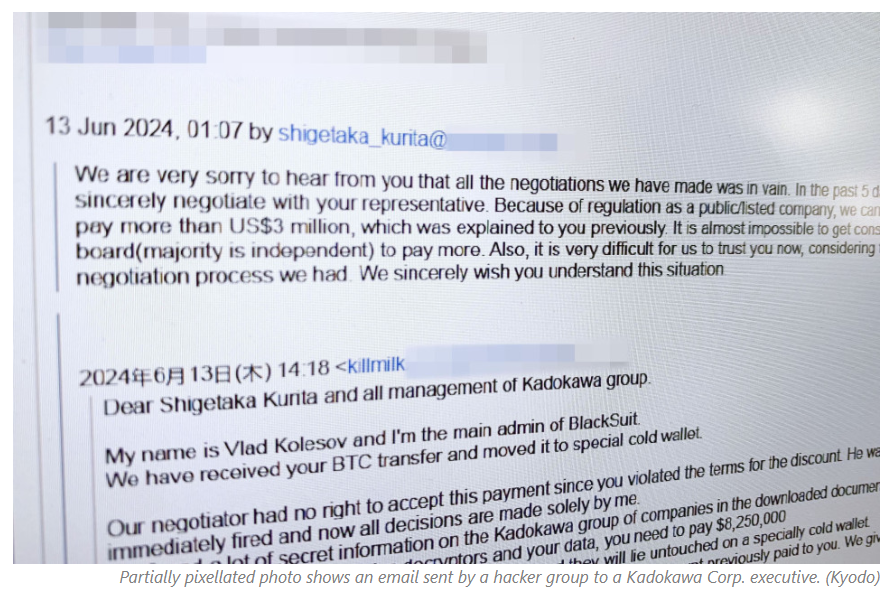
Russian ransomware group BlackSuit e-mailed multiple executives of Japanese publisher Kadokawa Corp. that it had received $2.98 million in cryptocurrency from the firm after a massive cyberattack hit it in June.
An investigation by security firm Unknown Technologies, commissioned by Kyodo News, found online records of a $2.98 million transaction made the same month.
On June 8, servers located in Kadokawa group's data center experienced a significant cyberattack, including ransomware, targeting major video streaming website niconico and related services operated by the publishing firm.
The company confirmed later that month that the personal information of all employees of Dwango Co., its subsidiary operating niconico, had been leaked. (Kyodo News)
Related: Mainichi
Andreas Kohl, co-founder of Bitcoin sidechain Sequentia, claimed that he had crashed 69% of the Dogecoin network using an old laptop in El Salvador to execute it.
Data from Blockchair indicated that Dogecoin had 647 active nodes before the vulnerability was exploited. At the time of writing, Dogecoin had 315 active nodes.
Kohl said he used a vulnerability discovered by researcher Tobias Ruck to cause the nodes to crash.
On Dec. 4, an X account called “Department Of DOGE Efficiency” publicly disclosed a vulnerability on the Dogecoin network called DogeReaper that they said could have crashed the chain entirely.
The account said that the vulnerability functions like a “Death Note” from the Japanese manga and anime of that name. In that fictional world, writing someone’s name in a notebook will cause them to die of a heart attack.
The account said that the vulnerability does something similar to Dogecoin nodes. With the DogeReaper, the social media account said, anyone could write a node’s address and cause the node to die of a segmentation fault. (Ezra Reguerra / Cointelegraph)
Related: The Daily Hodl, crypto.news, Daily Coin, Blockchain News, CryptoNinjas, Altcoin Buzz, Coinpedia
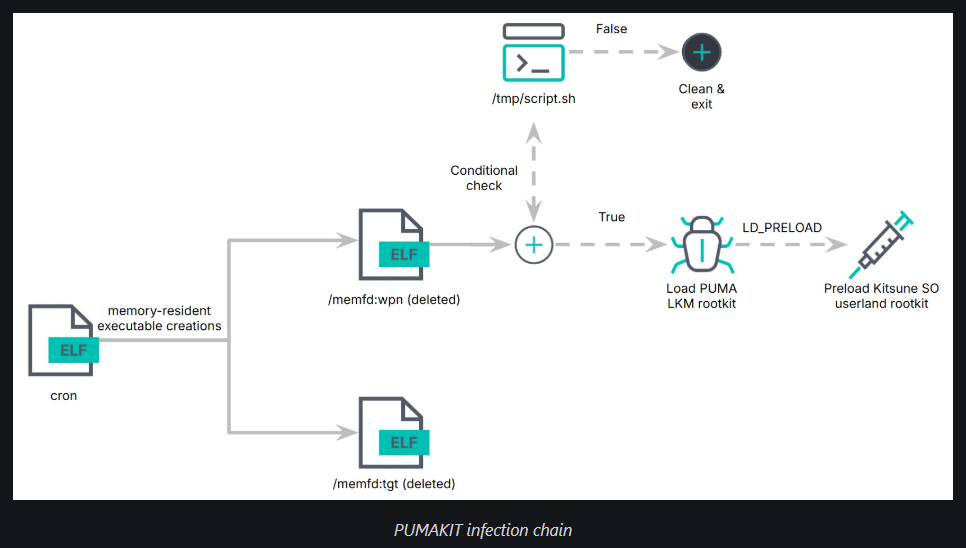
Researchers at Elastic Security report that a new Linux rootkit malware called Pumakit has been discovered that uses stealth and advanced privilege escalation techniques to hide its presence on systems.
The malware is a multi-component set that includes a dropper, memory-resident executables, a kernel module rootkit, and a shared object (SO) userland rootkit.
The researchers discovered Pumakit in a suspicious binary ('cron') upload on VirusTotal, dated September 4, 2024, and reported having no visibility into who uses it and what it targets.
Pumakit employs a multi-stage infection process starting with a dropper named 'cron,' which executes embedded payloads ('/memfd:tgt' and '/memfd:wpn') entirely from memory.
The malware's rootkit can hide its own presence from kernel logs, system tools, and antivirus, and can also hide specific files in a directory and objects from process lists. (Bill Toulas / Bleeping Computer)
Related: Elastic Security, Techzine
Email security startup Sublime Security announced it had raised $60M in a Series B venture funding round.
IVP led the round with participation from new investor Citi Ventures and existing investors Index Ventures, Decibel Partners, and Slow Ventures. (Jordan Novet / CNBC)
Related: FinSMEs, Sublime Security, Pulse 2.0, FinTech Global, Security Week
Best Thing of the Day: Cash-Strapped Local Governments Do Have Options
The nonprofit Center for Internet Security recommends local governments use federally funded resources, including the Malicious Domain Blocking and Reporting program offered by the Multi-State Information Sharing and Analysis Center or CISA's Cyber Hygiene scanning assessment service, given their limited resources to tackle cybersecurity challenges.
Worst Thing of the Day: Why Don't You Get Constantly Surveilled First?
During a recent meeting, Oracle co-found Larry Ellison described "a world where artificial intelligence systems would constantly monitor citizens through an extensive network of cameras and drones, stating this would ensure both police and citizens don't break the law."
Closing Thought
it




