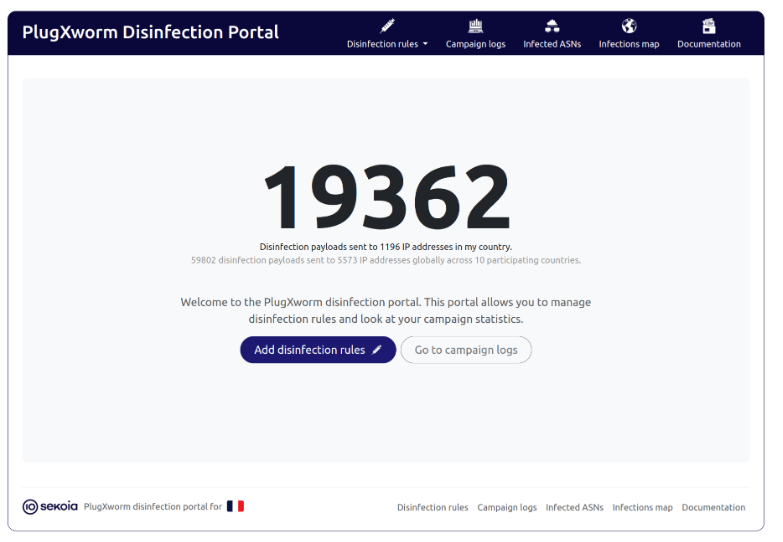
US Feds Deleted Chinese-Implanted PlugX Malware From Thousands of Systems
Biden to effectively bar many Chinese-made connected vehicles, US, S. Korea, and Japan say DPRK hackers stole $659m in 2024, Microsoft issued 161 Patch Tuesday fixes, Another Fortinet zero day exploited in the wild, CISA issues AI playbook, Woman bilked of savings by deepfake Brad Pitt, much more