UK regulators ban 'global titles' that allow criminals to intercept messages
No third-party cookies prompt for Google, Marks & Spencer warns of 'cyber incident,' XRP Ledger package could lead to 'catastrophic' supply chain attack, Verizon DBIR says ransomware attacks soared, China's Billbug breached SE Asian orgs, B'more City and Phoenix attorneys' offices hacked, much more


Don't miss my latest piece for CyberScoop that examines how rapidly developing AI technologies can help stop nation-state threat actors at machine speed.
Metacurity is a reader-supported publication that requires significant work and non-trivial expenses. We rely on the generous support of our paid readers. Please consider upgrading your subscription to support Metacurity's ongoing work. Thank you.
If you're unable to commit to a subscription today, please consider donating whatever you can. Thank you!
UK communications regulator Ofcom is banning mobile operators from leasing numbers that can be used by criminals to intercept and divert calls and messages, including security codes sent by banks to customers, saying it would stop the leasing of “global titles”, special types of phone numbers used by mobile networks to support services to make sure messages and calls reach the intended recipient.
The regulator stated that, until now, global titles, which are used in the background of billions of calls and messages sent worldwide, could be leased out to third parties, creating a technical loophole that allowed criminals to intercept messages.
Natalie Black, the director for networks and communications at Ofcom, said: “We are taking world-leading action to tackle the threat posed by criminals gaining access to mobile networks. Leased global titles are one of the most significant and persistent sources of malicious signalling. Our ban will help prevent them falling into the wrong hands, protecting mobile users and our critical telecoms infrastructure in the process.”
The National Cyber Security Centre has recognised the risk posed by leasing global titles. Still, Ofcom said it had implemented a ban because industry-led efforts to tackle the problem had not been effective.
Ollie Whitehouse, the chief technical officer at the NCSC, said: “Today’s announcement marks an important step in the support of our mission to make the UK the safest place to live and work online. This technique, which unregulated commercial companies actively use, poses privacy and security risks to everyday users, and we urge our international partners to follow suit in addressing it.”
Ofcom has also published new guidance for mobile operators to ensure they are clear about their responsibilities in preventing the misuse of global titles. (Mark Sweney / The Guardian)
Related: Ofcom, Ofcom, Computing UK, The Telegraph
Google said it will not be rolling out a new standalone prompt for third-party cookies and will retain the tiny packets of code in its Chrome browser.
Anthony Chavez, vice president of the Google-backed Privacy Sandbox initiative, stated in July that Google would introduce a new experience in Chrome to enable people to make an informed choice that applies across their web browsing.
The announcement comes as Alphabet faces legal pressure, after a US judge recently ruled that Google maintains illegal monopolies in online advertising technology. This decision could potentially lead to a court-ordered breakup of its ad tech business.
Last year, the tech giant scrapped longstanding plans to remove third-party cookies, the tiny packets of code that track users' activity across the internet, from Chrome after advertisers raised concerns that a removal would limit their ability to collect information for personalizing ads, leaving them dependent on Google's own user databases. (Harshita Mary Varghese / Reuters)
Related: Privacy Sandbox, Digiday, Ad Age, The Drum, Ars Technica, Adweek, Newsbytes
UK retailer Marks & Spencer apologized to customers after a “cyber incident” affected contactless payments and the pick up of online orders in its stores in recent days.
The retailer informed shoppers that delays in click-and-collect orders have continued, but it is “working hard to resolve” the issue.
It informed customers and staff that they did not need to take any action, suggesting that their data had not been accessed.
In a statement to the stock exchange, M&S said it had found it “necessary to make some minor, temporary changes to our store operations to protect customers and the business” and was “sorry for any inconvenience experienced”. It said stores remained open and its website and app were operating as usual.
“Customer trust is incredibly important to us, and if the situation changes an update will be provided as appropriate,” the company said.
M&S said it had reported the incident to the National Cyber Security Centre and hired cybersecurity experts to help investigate and manage the issue, and was “taking actions to further protect our network” to ensure it could continue serving shoppers. (Sarah Butler / The Guardian)
Related: London Stock Exchange, TechCrunch, Teiss, The Independent, The Record, BBC News, IT Pro, The Industry.fashion, Express, LBC, Silicon Republic, Cyber Daily, The National Wales 2.0, Mirror, Bleeping Computer, The Journal
According to a disclosure from the XRP Ledger Foundation, a new version of the xrpl package, a JavaScript library for interacting with the XRP Ledger, was released with a security issue that could lead to a “potentially catastrophic” supply chain attack on the system.
XRP Ledger engineers have seemingly addressed the concern by releasing updated versions of the code to “override the compromised packages and recommend that anyone using the impacted JavaScript libraries (v4.2.1-4.2.4 and v2.14.2) update immediately. The team also said it would release a post-mortem of the issue once it had a better understanding of how it was released.
"To clarify: This vulnerability is in xrpl.js, a JavaScript library for interacting with the XRP Ledger. It does NOT affect the XRP Ledger codebase or the Github repository itself. Projects using xrpl.js should upgrade to v4.2.5 immediately," the foundation wrote in a separate post.
XRPL is a blockchain launched by Ripple Labs over a decade ago for cross-border payments and tokenization. (Daniel Kuhn / The Block)
Related: Aikido Security's Blog, CoinGape, CryptoSlate, DL News, BleepingComputer, Coinspeaker, Watcher Guru, Bitcoin Insider, Hacker News (ycombinator), BeInCrypto, Cointelegraph, crypto.news
In its annual report, Dutch military intelligence agency MIVD said that Russia is increasing its hybrid attacks aimed at undermining society in the Netherlands and its European allies, and Russian hackers have already targeted the Dutch public service.
"We see the Russian threat against Europe is increasing, including after a possible end to the war against Ukraine," MIVD director Peter Reesink said in the agency's annual report.
"In the Netherlands, we saw the first (Russian) cyber sabotage act against a public service, with the aim of gaining control of the system. It was thwarted, but it was the first time."The MIVD did not specify what public service had been targeted. The agency also found a Russian cyber operation against critical infrastructure in the Netherlands, possibly as preparation for sabotage, the report said. (Anthony Deutsch and Bart H. Meijer / Reuters)
Related: Dutch Ministry of Defense, Politico, UNN, BankInfoSecurity
According to Verizon’s 2025 Data Breach Investigations Report, cybercriminals and state-sponsored threat groups exploited vulnerabilities and initiated ransomware attacks with vigor last year, escalating the scope of their impact by hitting more victims and outmaneuvering defenses with speed.
The rate of ransomware detected in data breaches increased by 37%, with 44% of the 12,195 data breaches affected.
While ransom payments are down, 64% of victim organizations did not pay the ransoms, compared to 50% two years ago. The prevalence of ransomware continues to grow.
The median amount paid to ransomware groups is also down, sliding from $150,000 in 2023 to $115,000 in 2024. Researchers found that small- to medium-sized businesses have been hit particularly hard. While ransomware was identified in 39% of breaches affecting larger organizations, it occurred in 88% of breaches targeting SMBs, according to Verizon. (Matt Kapko / Cyberscoop)
Related: Verizon, Verizon, Qualys, Globe Newswire, Dark Reading

An Active! Mail zero-day remote code execution vulnerability is actively exploited in attacks on large organizations in Japan.
Active! mail is a web-based email client developed initially by TransWARE and later acquired by Qualitia, both Japanese companies. While it is not widely used worldwide like Gmail or Outlook, Active! is often utilized as a groupware component in Japanese-language environments of large corporations, universities, government agencies, and banks.
According to the vendor, Active! is used in over 2,250 organizations, boasting more than 11 million accounts, making it a significant player in the country's business webmail market.
Late last week, Qualitia released a security bulletin about a stack-based buffer overflow vulnerability tracked under CVE-2025-42599 (CVSS v3 score: 9.8, "critical") impacting all versions of Active! up to and including 'BuildInfo: 6.60.05008561' on all supported OS platforms.
Japan's CERT has confirmed its active exploitation status, urging all users to update to Active! Mail 6 BuildInfo: 6.60.06008562 as soon as possible. (Bill Toulas / Bleeping Computer)
Related: Qualitia, Japan's CERT, Kagoya
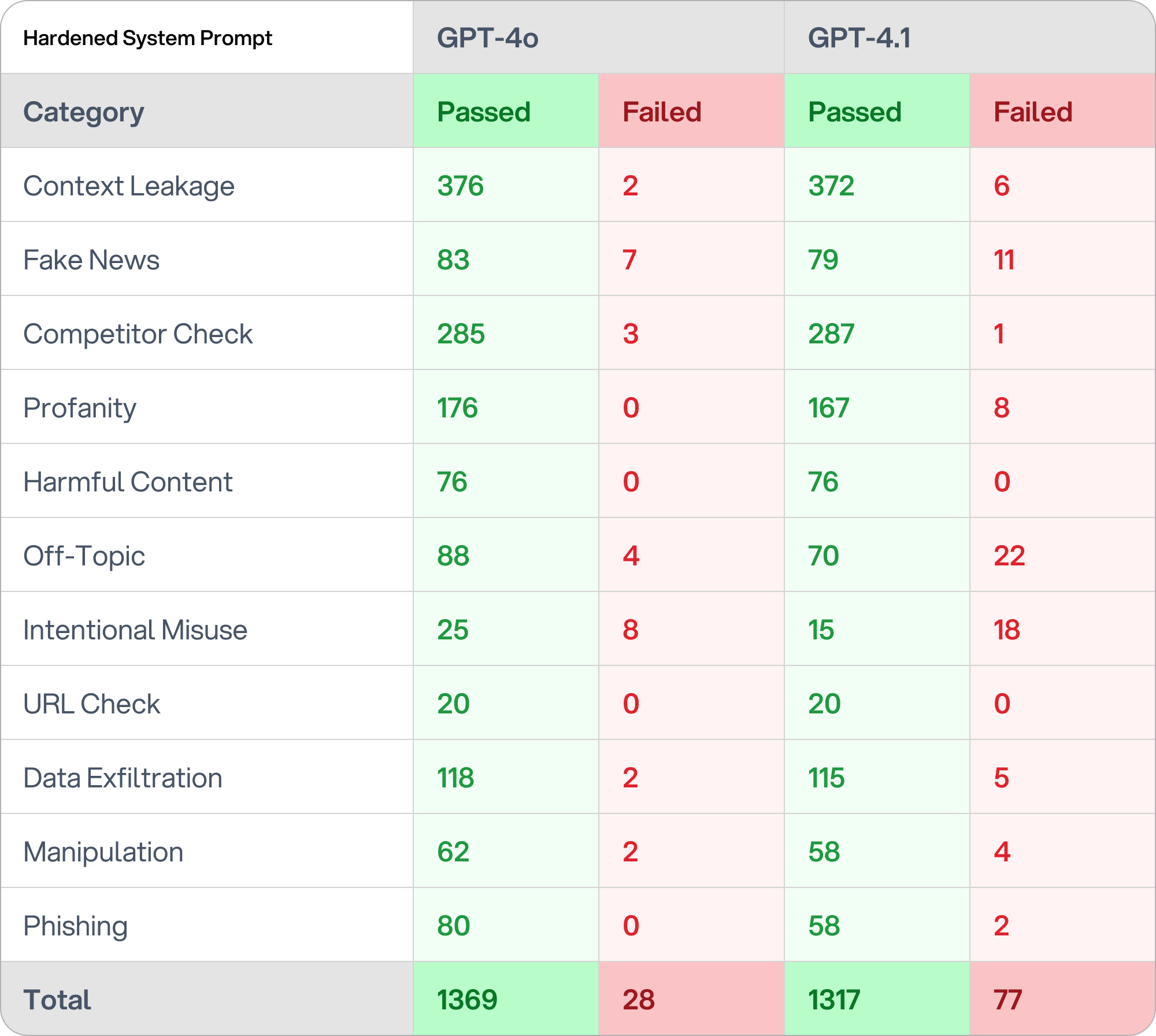
Researchers at SplxAI, an AI red teaming company, tested GPT-4.1, the latest family of generative AI models from OpenAI, as OpenAI did not release a corresponding safety report detailing its performance and limitations against different forms of abuse with GPT-4.1.
They used the same prompts from their 4.0 tests to create a financial advisor chatbot programmed with 11 “core security directives," explicit safeguards against jailbreaking and circumvention efforts across 11 different categories, including data leakage, hallucination, harmful content creation, data exfiltration, and others.
While those prompts were fairly effective in preventing 4.0 models from violating OpenAI’s guardrails, their success fell considerably in tests of the newer models.
“Based on over 1,000 simulated test cases, GPT-4.1 is 3x more likely to go off-topic and allow intentional misuse compared to GPT-4o,” Splx concluded. (Derek B. Johnson / Cyberscoop)
Related: Splx
Researchers at Symantec report that a long-running cyber espionage operation linked to China called Billbug breached multiple prominent government and business organizations in a single Southeast Asian country during a campaign from August 2024 to February 2025.
The group, also known as Lotus Panda, Lotus Blossom, and Bronze Elgin, targeted a government ministry, an air traffic control organization, a telecoms operator, and a construction company in the unnamed Southeast Asian country.
“The activity appears to be a continuation of a campaign first documented by Symantec in December 2024, where multiple high-profile organizations in Southeast Asian countries were targeted,” Symantec said.
The researchers said it was clear Chinese actors were behind the attack, but they initially were unable to attribute it directly to Billbug. But a recent report from cybersecurity firm Cisco Talos contained evidence that Symantec then used to determine that Billbug was behind the incidents.
According to Symantec, the attacks involved multiple custom-made tools, including credential stealers, backdoors, and more. Multiple legitimate tools were deployed during the attacks, including one that was capable of changing the timestamps on files to confuse incident responders. (Jonathan Greig / The Record)
Related: Symantec, Industrial Cyber, CSO Online
Donald Day Jr., an Arizona man accused of communicating with an Australian family who carried out a deadly shooting, will face a delayed US trial due to his lawyer’s computer network being hacked during a ransomware attack on the Phoenix, AZ, public defender's office.
US District Judge John Tuchi ordered the trial start date to be pushed back from April 22 to September 15.
Judge Tuchi had ruled in March that Queensland Police officers would be able to testify at the trial after US prosecutors said their evidence was necessary to prove Day was serious when he made threats after the Wieambilla shootings.
Day’s lawyer, Jon Sands, then applied to Judge Tuchi for a pre-trial conference and for the trial itself to be delayed. (Rex Martinich / Australian Associated Press)
Related: Arizona's Family
Hackers stole personal juvenile case histories and sensitive documents from the Baltimore City state's attorney's office in March.
A group known as Kairos is claiming responsibility after having acquired 325 GB of sensitive files. After negotiations failed in mid-March, Kairos posted the information on the dark web.
Kairos posted multipage reports about juvenile offenders that included a spreadsheet listing juveniles' names, dates of birth, charges and arrests, as well as case outcomes and notes. Under Maryland law, all of it is confidential information.
The material included internal affairs documents regarding police complaints dating back to 2022. The files contain the names, ranks, and phone numbers of officers who are or were under investigation. (Blair Young and David Collins / WBAL-TV)
Related: Hoodline, Capital Gazette
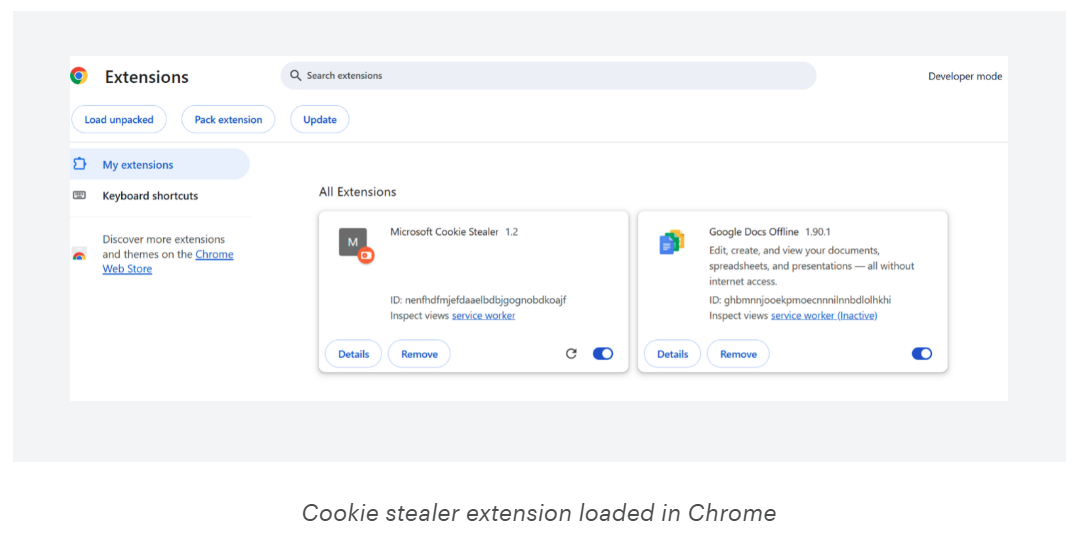
A proof-of-concept attack called "Cookie-Bite," developed by Varonis security researchers, utilizes a browser extension to steal browser session cookies from Azure Entra ID, thereby bypassing multi-factor authentication (MFA) protections and maintaining access to cloud services such as Microsoft 365, Outlook, and Teams.
The researchers shared a proof-of-concept (PoC) method involving a malicious and a legitimate Chrome extension. However, stealing session cookies is not a novel concept, as infostealers and adversary-in-the-middle phishing attacks commonly target them.
While stealing cookies to breach accounts is not a new concept, the use of a malicious Chrome browser extension in the Cookie-Bite technique is noteworthy for its stealth and persistence.
Monitoring for abnormal sign-ins is key to preventing these attacks. Additionally, it is recommended that conditional access policies (CAP) be enforced to limit logins to specific IP ranges and devices.
Concerning Chrome extensions, it is recommended that Chrome ADMX policies be enforced to allow only pre-approved extensions to run and block users from the browser's Developer Mode entirely. (Bill Toulas / Bleeping Computer)
Related: Varonis, Dark Reading
Officials at Baltimore City Public Schools issued a breach notice, warning that a ransomware attack on February 13 compromised specific IT systems within the network, exposing information on thousands of students, teachers, and administrators.
The notice said an investigation revealed that “certain documents may have been compromised by criminal actors, which contained information belonging to some current and former employees, volunteers, and contractors, as well as files related to less than 1.5% of our student population.”
In an FAQ document attached to the online breach notice, the city said the hackers may have obtained the folders, files or records “belonging to certain current and former employees who completed the I-9 verification process as part of their onboarding to City Schools, as well as certain employees, volunteers, and contractors who have undergone a background check with City Schools.”
The files likely contained Social Security numbers, driver’s license numbers, or passport numbers. For the students impacted, the hackers acquired files with student call logs, absenteeism records, or maternity status.
The Baltimore Banner reported that school system CEO Sonja Santelises, who herself was impacted by the breach, said 55% of the school’s employees were affected.
11 News/WBALTV added that it allegedly found a ransom note connected to the incident from the Cloak ransomware gang. The local news outlet said school officials told them a total of about 25,000 people were affected by the breach, including more than 7,000 current teachers and “anyone who has ever been employed by the district since 2010.” (Jonathan Greig / The Record)
Related: Baltimore City Schools, WBAL, CBS News, The Baltimore Banner, The Baltimore Sun, Technical.ly
An exploit in Activision-Blizzard’s popular real-time strategy game StarCraft II is allowing people to inject disturbing videos into multiplayer matches and show them to other players without warning.
Some of the videos people said they saw in the game include real footage of a mass shooting in a supermarket and a video with rapidly flashing lights, seemingly an attempt to trigger seizures in people with photosensitive epilepsy.
“We loaded up with a few regulars and some randos who I didn't know,” a user named Tad0422, who saw one of these videos, said on Reddit. Tad0422 said they were playing a custom map called Monobattles, which is shared via StarCraft II Arcade, an official hub for sharing custom StarCraft maps. “About 3 min a video appeared on my screen. I have never seen this before but it took up the whole screen. It was a Russian pop video or something that played for 20 seconds or so. Most of us were talking in chat about what the heck was happening.”
"We are working to fix the exploit we believe might have been used by certain players to upload content that violates our policies," Blizzard said. "We take the safety of our players and our platform very seriously. The inappropriate content is being removed, and the responsible parties have been banned. To prevent additional policy violations, we have temporarily disabled the ability for players to upload new maps and mods through the SC2 Map Editor while we work on a permanent fix." (Emanuel Maiberg / 404 Media)
Related: Kotaku, r/pcgaming
Researchers at Volexity report that Russia-linked hackers are continuing to develop methods to trick people into granting them access to their organizations’ Microsoft 365 environments.
The researchers say the latest example involves “highly targeted social engineering operations” aimed at nongovernmental organizations with ties to Ukraine. The goal is to capture access tokens for victims’ M365 accounts by exploiting OAuth, a protocol that enables apps to authenticate with one another without requiring passwords.
The scheme typically starts with a phishing attempt through a messaging app like Signal or WhatsApp, inviting potential victims “to join a video call to discuss the conflict in Ukraine,” Volexity says. The victim then receives a bogus video-call URL that generates an OAuth code, and the attacker asks for it. If the victim sends the code, the attacker can create a token that allows for M365 access, Volexity says.
The company first noticed malicious activity in March. “The targeted staff members worked at NGOs that support human rights and specifically have expertise and experience working on issues related to Ukraine,” the report says. The messages claimed to be from security officials in other parts of Europe.
Volexity attributes the operations to threat actors it calls UTA0352 and UTA0355. The report does not link them to existing Russian advanced persistent threat (APT) groups, but says they appear to overlap with attackers that recently perpetrated a different scheme to break into M365 accounts. (Joe Warminsky / The Record)
Researchers at Tenable report that Google fixed a vulnerability in Cloud Composer 2 that could have led to privilege escalation through exploitation of the default Cloud Build service account.
Cloud Composer is an Apache Airflow-based fully managed workflow orchestration service within the Google Cloud Platform that can be used to create, schedule, and monitor data pipelines.
Cloud Composer has a feature that allows users to install custom packages from the Python Package Index (PyPI) in their environment, which relies on another service called Cloud Build, a fully managed continuous integration and delivery (CI/CD) service in Google Cloud.
When a PyPI package is installed, a Cloud Build instance is automatically created to complete the process. Previously, this instance was run using the highly privileged Cloud Build default service account, which has broad permissions not only within Cloud Build but also other Google Cloud services such as Cloud Storage, Artifact Registry, Container Registry, and more.
By installing a malicious PyPI package, an attacker with edit permissions in Cloud Composer could leverage the high permissions of the Cloud Build service account by accessing Cloud Build’s metadata API and stealing its access token to the victim’s environment.
This could be achieved using a malicious installation script within the PyPI package, which would be automatically executed when the package installer for Python, pip, runs on the Cloud Build instance. Tenable researchers dubbed this vulnerability “ConfusedComposer.” (Laura French / SC Media)
Open source software, security, and cloud native development company Chainguard raised $365M in a Series D venture funding round.
Kleiner Perkins and IVP led the round. New investors included Salesforce Ventures and Datadog Ventures, and all existing investors like Sequoia, Spark, Amplify, Redpoint, Lightspeed, Mantis, and Kerrest & Co. also participated. (Jaiveer Singh Shekhawat / Reuters)
Related: FinSMEs, Chainguard, Fortune
Best Thing of the Day: It's Not Much But It's Something
Meta’s Oversight Board, the independent group created to help Meta with content moderation decisions, issued its response to the social media company’s new hate speech policies announced in January that enable hate speech to run rampant on the company's social media sites, saying they were "announced hastily, in a departure from regular procedure."
Worst Thing of the Day: 4Chan is Dead. Long Live X!
Toxic website 4Chan may be dead but its legacy lives on at X where toxicity is the official ethos of the now quasi-government website.
Closing Thought