UK government demands Apple create an encrypted cloud backdoor
DOGE worker had write access to US payment system, DOGE workers fan out through US agencies, CISA and NSA workers offered deferred resignations, US lawmakers plan to ban DeepSeek, UK Cyber Monitoring Centre launched, Japan moves on active cyber defense, Bondi disbands FBI task force, much more


Please consider supporting Metacurity with an upgraded subscription so that you can continue receiving our daily missives, packed with the top infosec developments you should know.
If you can't commit to a subscription today, consider tipping or donating to help keep Metacurity going.
Sources say security officials in the United Kingdom have demanded that Apple create a backdoor that would allow them to retrieve all the content any Apple user worldwide has uploaded to the cloud.
The British government’s undisclosed order, issued last month, requires blanket capability to view fully encrypted material, not merely assistance in cracking a specific account. It has no known precedent in major democracies. T
Sources said its application would mark a significant defeat for tech companies in their decades-long battle to avoid being wielded as government tools against their users.
The sources said that rather than break the security promises it made to its users everywhere, Apple is likely to stop offering encrypted storage in the UK.
However, that concession would not fulfill the UK demand for backdoor access to the service in other countries, including the United States.
The sources said the office of the Home Secretary has served Apple with a document called a technical capability notice, ordering it to provide access under the sweeping UK Investigatory Powers Act of 2016, also known as the Snooper's Charter, which authorizes law enforcement to compel assistance from companies when needed to collect evidence.
The law makes it a criminal offense to reveal that the government has even made such a demand.
Apple can appeal the UK capability notice to a secret technical panel, which would consider arguments about the expense of the requirement, and to a judge who would weigh whether the request was proportionate to the government’s needs. However, the law prohibits Apple from complying during an appeal.
In March, when the company was on notice that such a requirement might be coming, it told Parliament: “There is no reason why the U.K. [government] should have the authority to decide for citizens of the world whether they can avail themselves of the proven security benefits that flow from end-to-end encryption.” (Joseph Menn / The Washington Post)
Related: MacRumors, Financial Express, PhoneArena, Benzinga, Digital Trends, Reuters, Deccan Herald, Hacker News (ycombinator), The Verge
Despite White House and Treasury Department denials that technologists associated with Elon Musk’s Department of Government Efficiency (DOGE) could rewrite the code of the payment system through which the vast majority of federal spending flows, DOGE operative Marko Elez did, in fact, have write access.
Elez previously worked for SpaceX, Musk’s space company, and X, Musk’s social media company. Elez resigned Thursday after The Wall Street Journal inquired about his connections to “a deleted social-media account that advocated for racism and eugenics.”
Elez was granted privileges including the ability to not just read but write code on two of the most sensitive systems in the US government: the Payment Automation Manager (PAM) and Secure Payment System (SPS) at the Bureau of the Fiscal Service (BFS), an agency that according to Treasury records paid out $5.45 trillion in fiscal year 2024.
The ability to alter the code on these systems would, in theory, give a DOGE technologist, and, by extension, Musk, President Donald Trump, or other actors, the capability to, among other things, illegally cut off Congressionally authorized payments to specific individuals or entities. (Vittoria Elliott, Leah Feiger, and Tim Marchman / Wired)
Representatives of billionaire Elon Musk’s Department of Government Efficiency fanned out across several agencies, visiting the Atlanta headquarters of the Centers for Disease Control and Prevention and meeting with the Labor Department to seek access to sensitive data.
The moves followed the DOGE team's gaining access to sensitive health payment systems at the Department of Health and Human Services.
DOGE staffers met with agencies facing sweeping cuts in a project that has gutted whole programs and given Musk’s team broad access to private data. In a little more than two weeks, the Trump megadonor, acting as a “special government employee” while still running the companies that have made him the richest man in the world, has probed all over for cuts and begun enacting some, helping to shut down the US Agency for International Development effectively and suggesting that other departments could be next.
The speed and scope of DOGE’s work have stunned many in the government and raised widespread legal and security concerns. (Dan Diamond, Lauren Kaori Gurley, Lena H. Sun, Hannah Knowles, and Emily Davies / Washington Post)
Related: Wall Street Journal, Infosecurity Magazine
Employees at the Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CIsA) were initially excluded from broader government offers to take deferred resignation offers but some CISA employees have now been given the offer.
Sources said Elon Musk's DOGE-driven effort gave the employees just hours to decide whether to accept it.
"Team CISA, I am writing to provide an update that CISA employees may participate in the Deferred Resignation program ('Fork in the Road')," wrote Bridget Bean, who was identified in an email as the "senior official performing the duties of director" at CISA. "This is a deeply personal decision, and whichever decision you make, we support you."
Bean also wrote that the offer expires on Thursday, February 6, 2025, before midnight. It's unclear whether the offer is legally binding or whether Congress will appropriate funds to pay for it after March.
Separately, the National Security Agency (NSA) is the latest intelligence community entity, following the CIA, to offer its workforce the ability to leave their jobs in exchange for a paycheck for several months, according to two sources familiar with the move. (Jenna McLaughlin / NPR and Martin Matishak / The Record)
Related: NextGov/FCW, Federal News Network, Cyber Daily, Engadget
Following similar actions in Italy, South Korea, and Australia, US lawmakers said they plan to introduce a bill to ban DeepSeek’s chatbot application from government-owned devices over new security concerns that the app could provide user information to the Chinese government.
The legislation written by Reps. Darin LaHood (R-IL) and Josh Gottheimer (D-NJ) echoes a strategy that Congress used to ban Chinese-controlled TikTok from government devices, which marked the beginning of the effort to block the company from operating in the US.
“This should be a no-brainer in terms of actions we should take immediately to prevent our enemy from getting information from our government,” Gottheimer said. (Natalie Andrews / Wall Street Journal)
Related: Ars Technica, 9to5Mac, SiliconANGLE, Josh Gottheimer, Android Authority, NBC News, Android Police, WinBuzzer, Business Insider, The Record, Engadget, Bloomberg, Forbes, Associated Press, PYMNTS.com, CNN, Semafor, Techstrong.ai, Research & Development World, Fortune, nextpit, Washington Examiner, ABC News, DNyuz, Quartz, Fox Business, Krebs on Security
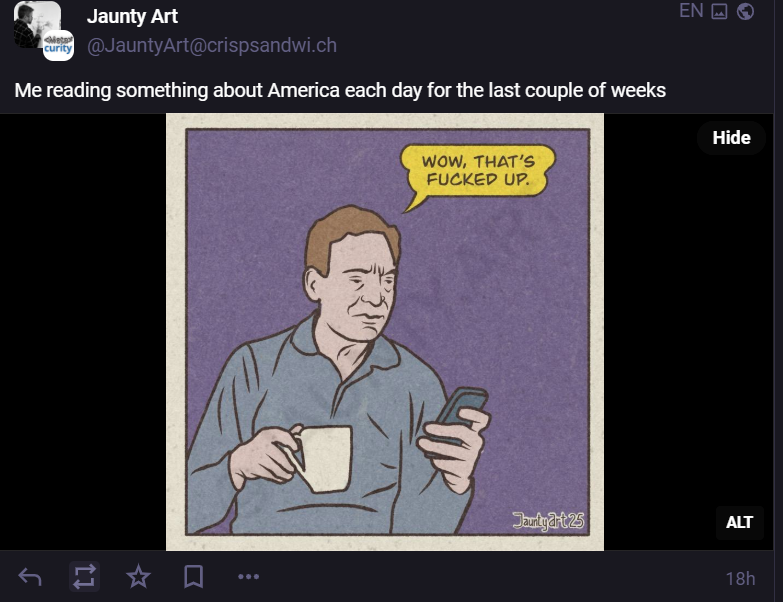
A world-first organization assembled to categorize the severity of cybersecurity incidents along a hurricane-type scale, the Cyber Monitoring Centre (CMC), is up and running in the UK following a year-long incubation period.
The cyber insurance industry and a handful of the UK's foremost cybersecurity thought leaders formed the CMC. It uses a severity classification system for the most severe computer assaults, similar to the Saffir-Simpson Scale, which differentiates hurricanes based on the damage they cause to affected regions.
Public communications about the CMC began in January 2024, when the literature suggested it was a system that would help cyber insurance companies and their reinsurers independently define a systemic event. A systemic event emanates from a single source, such as an attack on a vendor, but significantly impacts myriad other organizations.
The system categorizes cyber events on a 1-5 scale, with five being the most severe. Each event will be categorized by the CMC's technical committee, chaired by Ciaran Martin, the founding CEO of the UK's NCSC, comprising experts from industry, academia, and think tank The Royal United Services Institute (RUSI).
Committee members will meet on an ad hoc basis when an event shows signs of damages exceeding £100 million ($123.6 million), multiple organizations in the UK are affected, and when the information required for an assessment is available.
Methodology documents state that members will assemble for half a day to publish two deliverables: a severity categorization (1-5) and a report detailing how the decision was reached, what data informed it, and, in some cases, comments on the degree of confidence.
The severity score will be determined by examining the financial impact of the event and the number of organizations affected. The finances factored into the decision include, but are not limited to, incident response costs, notification costs, ransom payments, data restoration costs, and business interruption costs. It won't consider liability payments or fines issued after the fact. (Connor Jones / The Register)
Related: Cyber Monitoring Center, Cyber Monitoring Center, ONS.gov.uk, Computer Weekly, Insurance Business America, DIGIT, Infosecurity Magazine, Rayo, Computing, RedPacket Security, Morningstar, The Insurer, The Independent
Japan's cabinet approved two bills on "active" cyber defense security, paving the way for Japan to acquire preemptive capability against cyberattacks, often referred to as the “Achilles’ heel” of Japan’s defense system.
The new measures aim to strengthen cooperation and facilitate information-sharing between public and private cyber actors. They will allow the government to acquire information traveling through Japan and infiltrate the sources of cyberattacks to neutralize them.
If approved, the bills would give the government more powers to safeguard critical infrastructure and require private-sector entities to report the acquisition of critical infrastructure and potential cyberattacks to the authorities. The information would be shared with a group of relevant stakeholders.
Government officials said that the number of entities expected to become the target of the new measures currently hovers around 200. Those who leak cyberdefense-related secrets will be imprisoned for up to two years or fined up to ¥1 million ($6,600). Penalties for officials leaking intelligence information will be even harsher, at up to four years in prison. (Gabriele Ninivaggi and Himari Semans / The Japan Times)
Related: Kyodo News, Digwatch
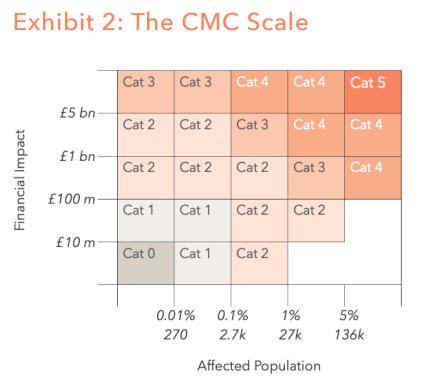
Researchers at AhnLab Security Intelligence Center (ASEC) recently observed the North Korean hacking group Kimsuky conducting attacks that used a custom-built RDP Wrapper and proxy tools to access infected machines directly.
RDP Wrapper is a legitimate open-source tool designed to enable Remote Desktop Protocol (RDP) functionality on Windows versions that do not natively support it, like Windows Home.
ASEC says the North Korean hackers now use diverse customized remote access tools instead of relying solely on noisy backdoors like PebbleDash, which is still used. It acts as a middle layer, allowing users to enable remote desktop connections without modifying system files.
Kimsuky's version altered export functions to bypass antivirus detection and likely differentiates its behavior enough to evade signature-based detection.
ASEC reports that once Kimsuky secures its foothold on the network, it drops secondary payloads. (Bill Toulas / Bleeping Computer)
The Yazoo Valley Electric Power Association, an electric utility serving multiple counties in Mississippi, was attacked by cybercriminals last summer, exposing the information of more than 20,000 residents.
The utility warned customers on August 26 through social media that, due to software problems, it was unable to process payments. The system was restored by August 30.
In breach notification letters filed with regulators last week, the utility confirmed it discovered “suspicious activity” on August 26 and initiated an investigation.
The organization completed its review on October 24, determining that a “limited” amount of personal information was accessed. It then “worked to obtain address information for potentially affected individuals” until December 20.
The organization redacted the information that was stolen by the hackers beyond the names of customers. Yazoo Valley Electric Power Association did not respond to requests for comment. The 20,997 victims are being offered one year of identity protection services. (Jonathan Greig / The Record)
Related: Yazoo Valley on Facebook, Office of the Maine Attorney General, JD Supra, Teiss, SC Media
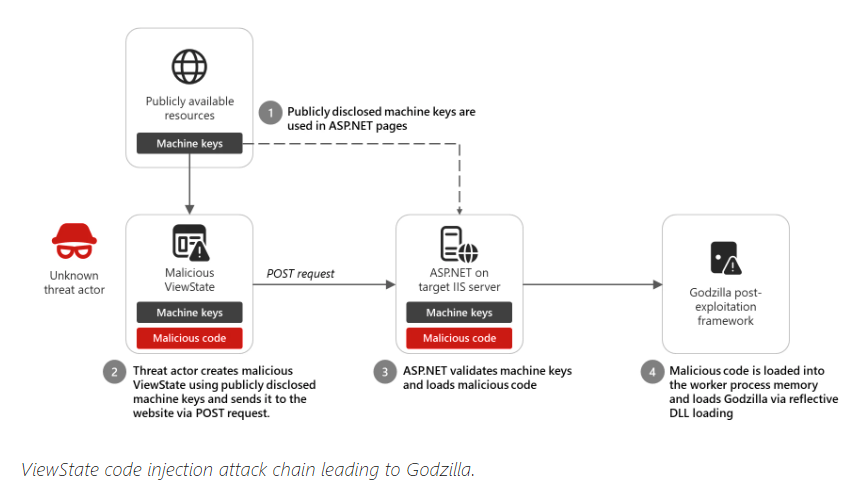
Microsoft warns that attackers are deploying malware in ViewState code injection attacks using static ASP. NET machine keys found online.
Microsoft Threat Intelligence experts recently discovered that some developers use ASP.NET validationKey and decryptionKey keys (designed to protect ViewState from tampering and information disclosure) found on code documentation and repository platforms in their own software.
ViewState enables ASP.NET Web Forms to control state and preserve user inputs across page reloads. However, suppose attackers get the machine key designed to protect it from tampering and information disclosure. In that case, they can use it in code injection attacks to craft malicious payloads by attaching crafted message authentication code (MAC).
In one instance observed in December 2024, an unattributed attacker used a publicly known machine key to deliver the Godzilla post-exploitation framework, which features malicious command execution and shellcode injection capabilities, to a targeted Internet Information Services (IIS) web server.
To block such attacks, Microsoft recommends developers securely generate machine keys, not use default keys or keys found online, encrypt machineKey and connectionStrings elements to block access to plaintext secrets, upgrade apps to use ASP.NET 4.8 to enable Antimalware Scan Interface (AMSI) capabilities and harden Windows Servers by using attack surface reduction rules such as Block Webshell creation for Servers.
Microsoft also shared detailed steps for removing or replacing ASP.NET keys in the web.config configuration file using either PowerShell or the IIS manager console. It removed key samples from its public documentation to discourage this insecure practice further. (Sergiu Gatlan / Bleeping Computer)
Related: Microsoft, gbhackers, Security Affairs
One of the first acts taken by Pam Bondi after being sworn in as US attorney general was to disband the FBI’s Foreign Influence Task Force that countered the influence of adversarial foreign governments on American politics.
In a memo, Bondi wrote that the Department of Justice would be shifting resources in its National Security Division, including disbanding the FBI task force, “to free resources to address more pressing priorities, and end risks of further weaponization and abuses of prosecutorial discretion.”
Bondi’s memo also states that the Department of Justice will now only refer criminal charges under the Foreign Agents Registration Act if they “alleged conduct similar to more traditional espionage by foreign government actors.” (Derek B. Johnson / Cyberscoop)
Related: Justice.gov, NBC News, Bloomberg Law
Gravy Analytics has been sued again for allegedly failing to safeguard its vast stores of personal data, which are now feared stolen, which include the locations of tens of millions of smartphones, coordinates of which were ultimately harvested from installed apps.
A complaint filed in federal court in northern California is at least the fourth such lawsuit against Gravy since January, when an unidentified criminal posted screenshots to XSS, a Russian cybercrime forum, to support claims that 17 TB of records had been pilfered from the American analytics outfit's AWS S3 storage buckets.
The suit this week alleges that a massive archive contains the geo-locations of people's phones. It alleges "the hacked Gravy Analytics data included tens of millions of mobile phone coordinates of devices inside the US, Russia, and Europe, obtained through individuals’ use of major mobile applications such as Tinder, Grindr, Candy Crush, Subway Surfers, Moovit, My Period Calendar & Tracker, MyFitnessPal, Tumblr, Microsoft’s 365 office application, Yahoo’s email client, religious-focused apps such as Muslim prayer and Christian Bible apps, various pregnancy trackers, and many VPN apps, which users generally download, ironically, in an attempt to protect their privacy." (Thomas Claburn / The Register)
Related: Courtlistener
On Feb. 3, Nigeria's Economic and Financial Crimes Commission (EFCC) arraigned 42 foreign nationals, mainly Chinese and Filipino, on charges related to alleged cryptocurrency investment and romance fraud, part of a massive raid conducted in December 2024 against a purported cybercriminal syndicate of nearly 800 people.
The EFCC said the defendants willfully "caused to be accessed, a computer system which was organized to seriously destabilize the economic and social structure of the Federal Republic of Nigeria, by procuring and employing several Nigerian youths for identity theft and other computer related fraud." (Robert Lemos / Dark Reading)
Related: EFCC.gov.ng
After Michigan-based Nader Eldamouni and his business partner decided to buy a $300,000 Rolls Royce Dawn convertible, car thieves used the vehicle's transport window to hack into the transport system and reroute the car's delivery elsewhere.
Eldamount believes thieves stole the car after it was picked up for transport on January 17. (Chris Chilton / Carscoops)
Related: WSVN
Cybersecurity startup Astra Security announced it had received $2.7 million in a venture capital growth round.
Emergent Ventures led the round, with additional support from Better Capital, Blume Ventures, Neon Fund, and PointOne Capital. (Ionut Arghire / Security Week)
Related: Analytics India Magazine, sdx central, CityBiz, Economic Times, Entrepreneur, Silicon Angle, Inc42, Unite.AI
Best Thing of the Day: You Can't Fight What You Can't Name
The journalists at ProPublica are keeping a database of the employees from Elon Musk’s companies and those of his allies, as well as young staffers he’s recruited, to participate in Musk's DOGE effort to demolish federal government agencies.
Bonus Best Thing of the Day: Everyone Can Do Their Part
Kevin Couture, a resident of Maine, submitted a breach report to the state of Maine naming Elon Musk as the entity responsible for a data breach involving his personal information, citing Musk's DOGE effort to rummage around in US government databases.
Worst Thing of the Day: Mean Phishing Tests
IT departments are crafting increasingly sensational phishing tests, which they say is a necessary response to increasingly sophisticated scams, but employees say these emails only scare, confuse, or shame them.
Closing Thought