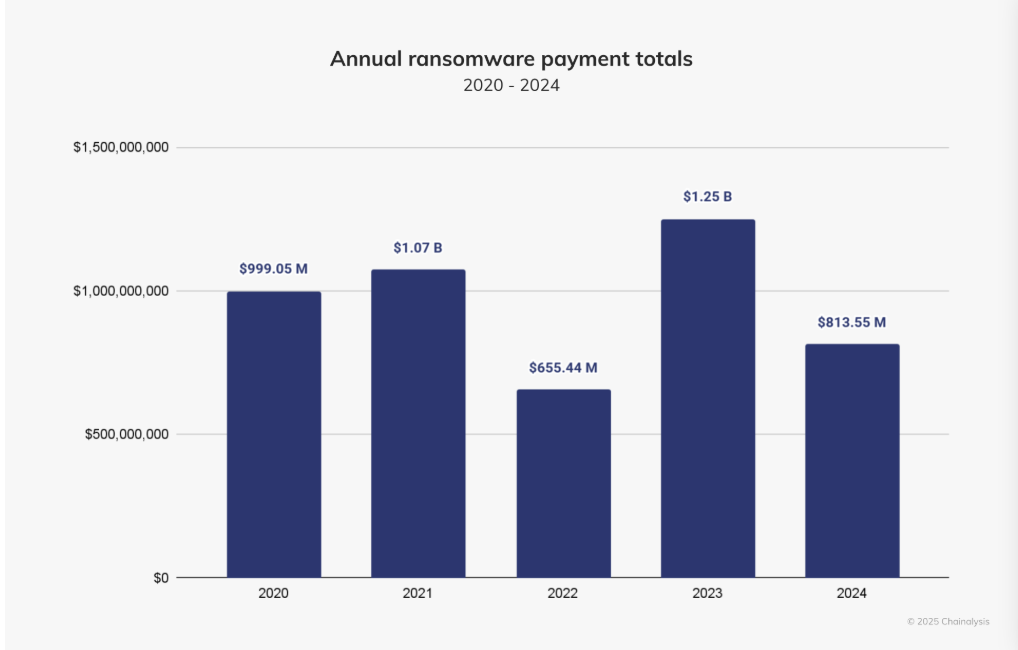
Ransomware payments fell 35% last year, Chainalysis
Fed CIOs will become political appointees, Trump tries to thin CIA's ranks, DeepSeek's R1 ranks lowest in cybersecurity, Oz bans DeepSeek from government offices, Thailand shuts power from scammer compounds, Unions sue Treasury for database plundering, Evans now CISA senior adviser, much more