Cybersecurity
A hacker stole content from the Telemessage system used by the US government
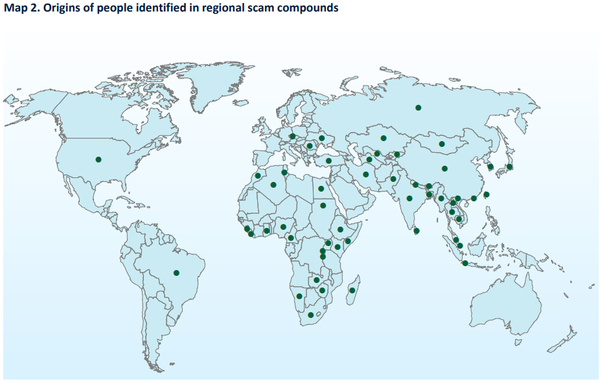
Criminal scam network run by Darcula exposed by journalists, DragonForce takes credit for Co-op attack, NoName attacked Romanian gov't websites on election day, US indicts Black Kingdom ransomware dev, Trump wants to slash nearly $500m from CISA, Qilin claims Cobb Co. attack, much more