Cybersecurity
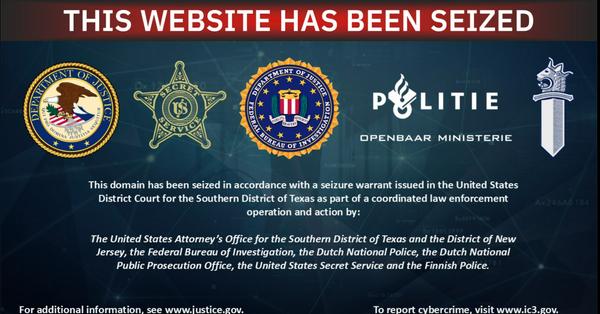
Law enforcement took down cybercriminal malware testing service AVCheck
German police ID Trickbot's "Stern," BitMEX thwarts Lazarus Group attack, Shin Bet thwarted 85 Iranian cyberattacks aimed at civilians, Vibe coding app Lovable failed to fix critical flaw, China's quantum satellite Micius has a security flaw, Russia's Unit 29155 has a hacker team, much more











