NCA Links LockBit Affiliate to Evil Corp While US, UK, and Australia Issue Sanctions
Investment firm hacker who stole $37M pleads guilty, Attackers target Zimbra RCE flaw, Journalist who uncovered scam compounds arrested in Cambodia, UK ministers slam bank account scan plan, Man who faked death was a serial hacker, Durov says Telegram policy is unchanged, much more


Check out what our sponsor, Anchore, is offering

Learn the building blocks for adopting a secure software factory model in a highly informative webinar. The Department of Defense (DoD) software factory model has emerged as a cornerstone of innovation and security for national defense and cybersecurity. Software factories represent an integration of principles and practices found within the DevSecOps movement, with technical guidelines to support continuous cyber-readiness with real-time visibility.
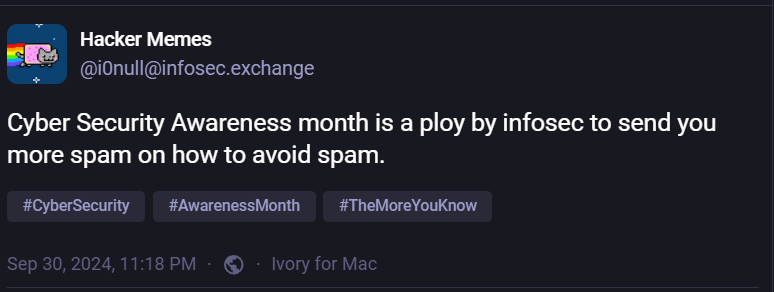
The UK's National Crime Agency linked a long-standing affiliate of the LockBit ransomware group, Aleksandr Ryzhenko, also known as Beverley, to the notorious Russia-backed Evil Corp.
British authorities believe Ryzhenko to be “second in command” at Evil Corp.
This is the latest effort by UK and international law enforcement, dubbed Operation Cronos, to disrupt the operations of LockBit, once one of the most prolific Russian ransomware gangs, and Evil Corp, one of Russia’s top cybercrime groups with known links to the Russian government.
The authorities provided evidence of further overlaps between the two Russian cybercrime gangs, partly by briefly resurrecting the dark web leak site of the notorious LockBit ransomware gang that the authorities had previously seized.
According to NCA, Ryzhenkov is close friends with Evil Corp founder and leader Maksim Yakubets, who was charged by the U.S. government in 2019 for his alleged role in developing and distributing the Dridex malware. Yakubets was previously accused of providing “direct assistance” to the Russian government.
The UK, US, and Australian authorities issued sanctions against Ryzhenkov, effectively making it unlawful for anyone affiliated with those countries to transact with him, including paying a ransom.
US prosecutors also charged Ryzhenkov with alleged computer crimes related to launching ransomware attacks against US-based victims.
The NCA said that while most Russian hackers it tracks are financially motivated, Evil Corp maintains a “privileged” relationship with the Russian state and was often tasked with carrying out cyberattacks on NATO countries on behalf of the Russian government.
Ryzhenkov, described by the NCA as Yakubets’ “right-hand man,” became a LockBit affiliate in 2022 who went on to target at least 60 victims, the authorities said.
The NCA has also identified Viktor Yakubets, Maksim’s father, and Eduard Benderskiy, Maksim’s father-in-law and a former high-ranking Russian intelligence official, as key to Evil Corp’s operations. The latter is a “key enabler” of the gang’s relationship with the Russian intelligence services. Both Yakubets and Benderskiy were also sanctioned.
The NCA announced several further arrests in its ongoing efforts to disrupt the prolific LockBit ransomware gang. British authorities arrested two people in the US who are believed to be associated with a LockBit affiliate on suspicion of computer hacking and money laundering offenses. A suspected LockBit developer was also arrested in France, and Spanish police detained one of the main facilitators of LockBit infrastructure, seizing nine servers used by the group.
The NCA says that while LockBit remains active, the actions taken so far have significantly affected ransomware operations. The NCA said the number of LockBit affiliates has fallen from around 200 to 70 since May. The gang claims to still be active by posting new victims to its dark web leak site, but most of those are repeat victims or false claims.
The agency said its investigations into the LockBit ransomware have also revealed new details about the gang’s source code and operation. The authorities said LockBit’s code was written to not delete a victim’s data even if the victim paid a ransom demand. (Carly Page / TechCrunch)
Related: NCA, NCA, Europol, GOV.uk, Domain Tools, Bloomberg, Justice Department, Treasury Department, Cyber Daily, iTnews, InfoRiskToday.com, The Record, DomainTools, CyberScoop, SC Media, The Guardian, The Register, Wired, SiliconANGLE, UPI, ComputerWeekly.com, Infosecurity Magazine, UPI, Dark Reading, The Guardian, Bleeping Computer, Security Affairs, BBC News, FBI.gov, Daily Mail
Evan Frederick Light, a hacker who infiltrated a company’s computer servers and stole more than $37 million in cryptocurrency from almost 600 victims, pleaded guilty to charges of conspiracy to commit wire fraud and money laundering.
The US Justice Department said that Light unlawfully accessed an investment firm's computer servers to steal customer information. He then used the data to steal cryptocurrencies from clients who had digital assets with the company.
Light, who authorities say worked with another unidentified perpetrator, then funneled funds from the “cyber-intrusion” through crypto mixers and gambling websites to conceal his identity and to hide the funds.
Light pleaded guilty on Sept. 30 and faces up to 20 years behind bars for each charge. (Brayden Lindrea / Cointelgraph)
Related: Justice Department, crypto.news, Cryptonews, Databreaches.net
In a series of posts on X, researchers at Proofpoint report that attackers are actively targeting a severe remote code execution vulnerability that email collaboration software suite Zimbra recently disclosed in its SMTP server, heightening the urgency for affected organizations to patch vulnerable instances immediately.
The bug, CVE-2024-45519, is present in the Zimbra postjournal service component for email journaling and archiving. It allows an unauthenticated, remote attacker to execute arbitrary commands on a vulnerable system and take control of it. Zimbra issued updates for affected versions last week but has not yet released any details of the flaw.
The security vendor described the attackers as sending spoofed emails that look like they are from Gmail to vulnerable Zimbra servers. The emails contain base64-encoded malicious code instead of normal email addresses in the CC field. This code is crafted to trick Zimbra into running it as shell commands rather than processing it as a regular email address. This technique could potentially allow attackers to execute unauthorized commands on affected Zimbra servers, Proofpoint said.
Ivan Kwiatkowski, a threat researcher at HarfangLab, said the malcious emails are coming from 79.124.49[.]86, which appears to be based in Bulgaria. "If you're using @Zimbra, mass-exploitation of CVE-2024-45519 has begun. Patch yesterday."
Researchers at the open-source Project Discovery released a proof-of-concept for the vulnerability on Sept. 27. They identified the issue as stemming from a failure to properly sanitize user input, enabling attackers to inject arbitrary commands. The researchers wrote that Zimbra's patched versions of the software have addressed the issue and neutralized the ability for direct command injection. (Jai Vijayan / Dark Reading)
Related: Project Discovery, Zimbra, Security Week, Security Affairs
Cambodian journalist Mech Dara, who was given a hero award last year by US Secretary of State Antony Blinken for his work exposing the existence of massive scam compounds staffed primarily by trafficked workers in Cambodia, was charged by a Cambodian court with "inciting social unrest," meaning he may face two years in prison.
The Phnom Penh Municipal Court in the country’s capital said Mech Dara, who has worked for local and international media, had posted "provocative" and "false" messages and pictures about a rock quarry on a sacred mountain.
According to a joint statement by civil society organizations working in the country, he was sent to pretrial detention in Kandal province.
Before his detention, local officials issued a statement on Facebook accusing Dara of wanting to "cause social disorder or confusion" through an image he posted showing quarrying at Ba Phnom in Prey Veng province, an important religious and historical site, the groups said.
"Dara must be freed so he can continue his work to shed light on issues like human trafficking, forced labour and corruption," said the co-director of one of the signatories, Licadho's Naly Pilorge. (Poppy Mcpherson / Reuters)
Related: The Record, BBC News, The Hill, NPR, UCA News, The Guardian, The Independent, Malaysiakini, Sky News
In a letter to Liz Kendall, the secretary of state for work and pensions, UK ministers said requiring banks to scan accounts for suspicious behavior would be a severe “intrusion into the nation’s privacy, with potentially punitive consequences for vulnerable individuals."
They urged the government not to tackle welfare fraud by launching mass algorithmic surveillance of bank accounts.
Prime Minister Keir Starmer announced a fraud, error, and debt bill last week to require banks to share data on account holders that “may show indications of potential benefit overpayments.”
Details have yet to be published, but the Department for Work and Pensions (DWP) stressed that the government would not have access to people’s bank accounts and would not use artificial intelligence to investigate data.
It said it would be able to request data from banks to indicate where a customer may not meet eligibility rules for benefits and that if there were a signal of fraud or error, a member of staff would always investigate it.
Separately, Meta said it’s working with two leading banks in the UK on the information-sharing arrangement to help protect consumers from fraud. (Robert Booth / The Guardian and Ryan Browne / CNBC)
Related: Tech Monitor, Meta, The Guardian, UPI, The Mirror, Infosecurity, CNBC, City A.M., Financial Times
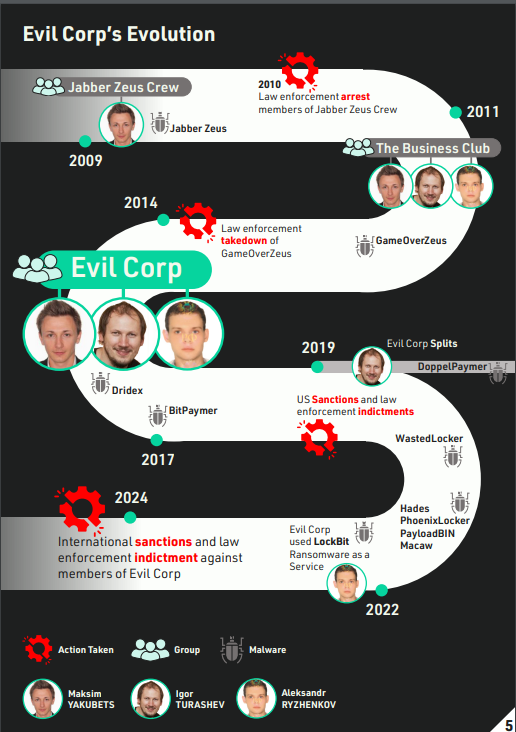
Austin Larsen, a senior threat analyst at Google’s cybersecurity firm Mandiant, along with his colleagues, spotted a post on a cybercrime forum by a hacker named FreeRadical, later identified as Jesse Kipf, who claimed to have hacked the electronic death registration system of a state, later determined to be Hawaii, setting into motion a federal investigation that revealed Kipf faked his death to avoid paying his ex-wife around $116,000 owed to support their daughter.
Kipf, whom prosecutors later called a “serial hacker” with “ample technical knowledge towards making a living by stealing from others,” had made a series of mistakes, including using his home internet from Somerset, Kentucky, to directly connect to the Hawaii death registration system, which eventually led federal agents right to his door.
According to Larsen, FBI Special Agent Andrew Satornino, and Assistant U.S. Attorney for the Eastern District of Kentucky Kate Dieruf, Kipf was a prolific hacker with multiple identities.
Larsen said that Mandiant identified the FreeRadical and GhostMarket09 personas as being connected to what the company calls UNC3944, or Scattered Spider, a prolific hacking and cybercrime group allegedly behind the MGM Resorts hack, and linked to the wider criminal underworld behind a string of violent crimes known as “the Com.”
Kipf was sentenced to prison for 81 months, just shy of seven years. (Lorenzo Franceschi-Bicchierai / TechCrunch)
Telegram CEO Pavel Durov said that the messaging app's recently announced updates to its terms of service haven’t led to many changes, despite his recent post that seemed to announce a major shift in how Telegram works.
Durov, who was charged by French prosecutors in August in connection to crimes committed on the app, announced last week that Telegram had beefed up moderation and updated its terms of service to deter criminals from abusing it.
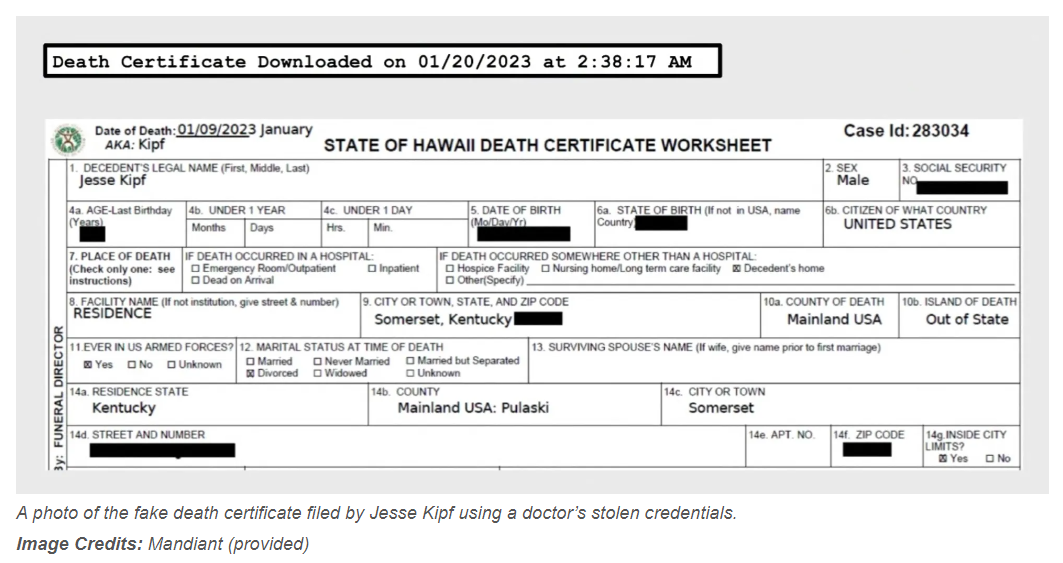
In a new Telegram post, Durov said Telegram’s policy since 2018 has been to disclose data from criminals to the authorities when it “received a properly formed legal request via relevant communication lines.”
“My previous post may have seemed to announce a major shift in how Telegram works. But in reality, little has changed,” Durov said in his most recent communication.
According to Durov, Telegram has been able to disclose IP addresses and phone numbers of criminals to authorities since 2018, in accordance with its privacy policies in “most countries.”
“For example, in Brazil, we disclosed data for 75 legal requests in Q1 (January-March) 2024, 63 in Q2, and 65 in Q3. In India, our largest market, we satisfied 2461 legal requests in Q1, 2151 in Q2, and 2380 in Q3,” Durov said. (Jake Rudnitsky / Bloomberg and Helen Partz / Cointelegraph)
The UK's Post Office ended its contract with Moneygram after a serious cyber security incident at the American money transfer giant.
MoneyGram said it is “shocked and disappointed” by the Post Office's portrayal of a contract breakdown that saw money transfer services removed from thousands of branches.
The money transfer firm also confirmed that the UK is the only country it operates where services are yet to resume following the cyber incident.
The Post Office said the US-based financial services firm turned down an offer of a short contract extension from the Post Office. (Karl Flinders / Computer Weekly)
Related: Finextra
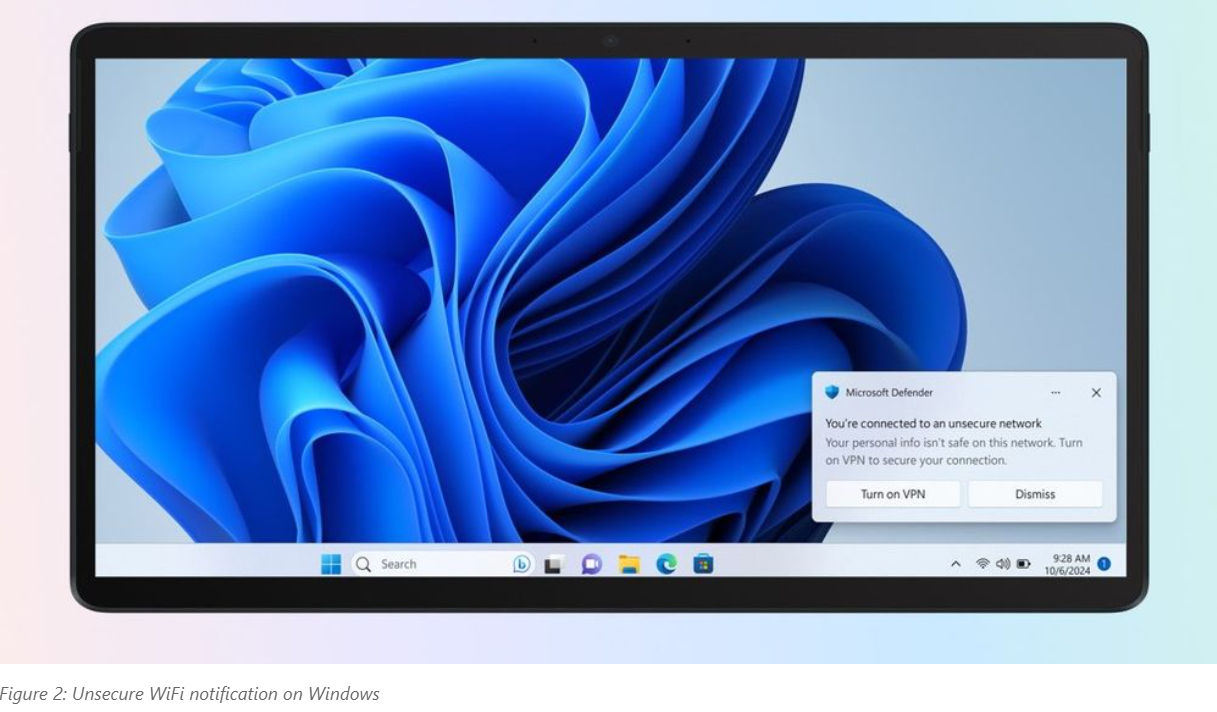
Microsoft Defender automatically detects and notifies users with a Microsoft 365 Personal or Family subscription when connected to unsecured Wi-Fi networks.
The Defender privacy protection feature (also known as Defender VPN) protects user privacy and security when connected to public Wi-Fi or an untrusted network, where a user's data and identity could be exposed or stolen.
To do that, it encrypts and routes a user's internet traffic through Microsoft's servers and hides your internet address (IP address) using a VPN (Virtual Private Network).
This can help defend users against attackers setting up a rogue wireless access point to trick users into connecting to it in Evil Twin attacks. After the victims connect, they can steal sensitive information in Man-in-the-Middle (MiTM) attacks or use phishing techniques to get more information.
The unsafe Wi-Fi alerts are now only available in Defender for Android, iOS, and Windows, with macOS support also to roll out soon.
The company has also added support for Defender VPN on Windows and macOS systems and made it available in Germany and Canada. More countries will be added in the upcoming months. (Sergiu Gatlan / Bleeping Computer)
Related: Microsoft, SC Media, Tom's Hardware, Channel E2E, WebProNews, Tech Radar
Managed cloud security remediation provider Tamnoon announced it had raised $12 million in a Series A venture funding round.
Bright Pixel Capital (formerly Sonae IM) led the round with participation by new investors Blu Ventures and Mindset Ventures as well as existing investors Merlin Ventures, Secret Chord Ventures, Inner Loop Capital, and Elron Ventures. (Duncan Riley / Silicon Angle)
Related: Business Wire, CTech, FinTech Global, FinSMEs
Apono, a startup that develops and manages an artificial intelligence-based solution for cloud permissions and access management, announced it had raised $15.5 million in a Series A venture funding round.
New Era Capital Partners led the round with additional participation from Mindset Ventures, Redseed Ventures, Silvertech Ventures, and existing investors Meron Capital and Booster Ventures. (Sophie Shulman / CTech)
Related: SC Media
Best Thing of the Day: Sunlight Is Always Good
After Meta failed to provide information about a missing child's online activity quickly enough, the Delhi High Court in India directed major social media platforms, including Meta and Google, to provide a detailed account of their Standard Operating Procedures (SOPs) when law enforcement agencies request information.
Worst Thing of the Day: How Not to Be Cybersecure
Researchers at Socura report that cybersecurity is now the fastest-growing IT role in the UK, but the share of women in such positions has fallen dramatically to just 17% of the total UK cybersecurity workforce since 2021.
Closing Thought