Marks and Spencer sends 200 workers home as cyberattack fallout worsens
Meta's AI digital companions do not protect underage users from sexually explicit banter, UK commissioner calls for ban on apps that create sexual images of children, SK Telecom plummets in wake of cyberattack, DeFi protocol Loopscale loses $5.8m in exploit, Juice-jacking mitigation found, much more


Metacurity is a reader-supported publication that requires significant work and non-trivial expenses. We rely on the generous support of our paid readers. Please consider upgrading your subscription to support Metacurity's ongoing work. Thank you.
If you're unable to commit to a subscription today, please consider donating whatever you can. Thank you!
Prominent UK retailer Marks & Spencer (M&S) ordered hundreds of agency workers at its main distribution centre to stay at home as it grapples with the unfolding impact of a cyberattack, almost certainly a ransomware attack.
Around 200 people who had been due to undertake shift work at M&S's vast Castle Donington clothing and homewares logistics centre in the East Midlands have been told not to come in amid the escalating crisis.
Agency staff make up about 20% of Castle Donington's workforce, according to a source close to M&S. The retailer's own employees who work at the site have been told to come in as usual.
It is how long the disruption to M&S's e-commerce operations would last, although retail executives said the cyberattack was "extensive" and that it could take the company some time to resolve its impact fully. (Mark Kleinman / Sky News)
Related: Retail Gazette, BBC News, The Independent, The Guardian
Staffers across multiple departments at Meta have raised concerns that the company’s rush to popularize AI digital companions may have crossed ethical lines, including by quietly endowing AI personas with the capacity for fantasy sex, with no underage users protected from such sexually explicit discussions.
Unique among its top peers, Meta has allowed these synthetic personas to offer a full range of social interaction—including “romantic role-play”—as they banter over text, share selfies and even engage in live voice conversations with users.
To boost the popularity of these souped-up chatbots, Meta has cut deals for up to seven figures with celebrities like actresses Kristen Bell and Judi Dench and wrestler-turned-actor John Cena for the rights to use their voices. The social-media giant assured them that it would prevent their voices from being used in sexually explicit discussions, according to people familiar with the matter.
After learning of the internal Meta concerns through people familiar with them, The Wall Street Journal over several months engaged in hundreds of test conversations with some of the bots to see how they performed in various scenarios and with users of different ages.
The test conversations found that both Meta’s official AI helper, called Meta AI, and a vast array of user-created chatbots will engage in and sometimes escalate discussions that are decidedly sexual, even when the users are underage or the bots are programmed to simulate the personas of minors. They also show that the bots deploying the celebrity voices were equally willing to engage in sexual chats.
“We did not, and would never, authorize Meta to feature our characters in inappropriate scenarios and are very disturbed that this content may have been accessible to its users—particularly minors—which is why we demanded that Meta immediately cease this harmful misuse of our intellectual property,” a Disney spokesman said.
Meta called the Journal’s testing manipulative and unrepresentative of how most users engage with AI companions. The company nonetheless made multiple alterations to its products after the Journal shared its findings.
Accounts registered to minors can no longer access sexual role-play via the flagship Meta AI bot, and the company has sharply curbed its capacity to engage in explicit audio conversations when using the licensed voices and personas of celebrities. (Jeff Horwitz / Wall Street Journal)
Related: TechCrunch, The Verge, Gizmodo, Mint
Dame Rachel de Souza, the children's commissioner for England, called for an immediate ban on artificial intelligence “nudification” apps that create deepfake sexual images of children.
Girls said they were stopping posting images of themselves on social media out of a fear that generative AI tools could be used to digitally remove their clothes or sexualise them, according to the commissioner’s report on the tools, drawing on children’s experiences. Although it is illegal to create or share a sexually explicit image of a child, the technology enabling them remains legal.
De Souza urged the government to introduce an AI bill that would require developers of GenAI tools to address the risks their products pose, and to roll out effective systems to remove sexually explicit deepfake images of children. This should be underpinned by policymaking that recognises deepfake sexual abuse as a form of violence against women and girls, she suggested.
A report issued by De Souza's office urges Ofcom to ensure that age verification on nudification apps is properly enforced and that social media platforms prevent sexually explicit deepfake tools being promoted to children, in line with the Online Safety Act. (Rachel Hall / The Guardian)
Related: Children's Commissioner, Children's Commissioner, The Times, Tech Digest
SK Telecom shares fell as much as 8.5% on Monday to hit their lowest level since August last year, after South Korea's biggest mobile carrier disclosed it suffered a leak of customer data earlier this month caused by a cyberattack.
The company said it would take full responsibility for any harm caused as a result of the breach that was detected on April 18. It described the incident as a large-scale leak of data due to malware, without providing more details.
SK Telecom also said it would start offering free universal subscriber identity module (USIM) replacements to all 23 million users for free at more than 2,600 retail stores nationwide.
SK Telecom also urged customers to sign up for its USIM Protection Service, which it said provided the same level of prevention as replacing a USIM card.
About 5.54 million people had signed up for the service, accounting for nearly a quarter of SK Telecom's 23 million subscribers as of Sunday. (Heekyong Yang and Jihoon Lee / Reuters)
Related: The Korea Herald, Korea JoongAng Daily, The Chosun Daily, Yonhap News, Light Reading, Tech Xplore, Retail News Asia
Loopscale, a Solana-based decentralized finance (DeFi) protocol, became 2025's latest hacking victim on Saturday, losing over $5.8 million, or 12% of its TVL, to an exploit affecting one of its markets.
"The root cause of the exploit has been identified as an isolated issue with Loopscale’s pricing of RateX-based collateral," the protocol said on X. "There is an ongoing investigation into how this happened, who did this, and how we can most effectively recover funds."
"Our team is fully mobilized to investigate, recover funds, and ensure users are protected," Loopscale co-founder Mary Gooneratne wrote on X. (Zack Abrams / The Block)
Related: TronWeekly, Cryptopolitan, Cryptonews, Web3IsGoingJustGreat, BeInCrypto, Coinfomania
The number of reported cybercrime incidents in the US state of Georgia escalated to 859,532 in 2024, with total losses of $16.6 billion, up 33% from the year prior.
In Georgia, the starkest spike in cybercrime was seen around cryptocurrency, where reports rocketed by 122% and estimated losses burgeoned by a concerning 66% compared to 2023 figures.
According to the FBI's recent report on cybercrime, in 2024, Georgia stood at the 11th position for internet-related complaints, climbing two spots from the previous year, and its citizens witnessed a spike in potential financial losses to the tune of $420 million, a 40% increase from 2023. (Rohit Mehta / Hoodline)
Related: Hoodline, WUGA, The Georgia Sun, WFXG, WSB Radio, Savannah Morning News
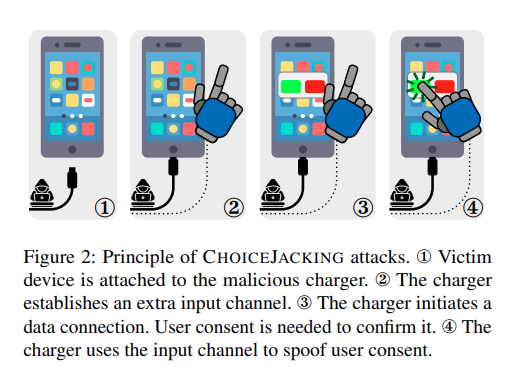
Researchers at the Graz University of Technology in Austria recently made a discovery that completely undermines the premise of juice-jacking, or equipping a charger with hidden hardware that can access files and other internal resources of phones.
They devised a new attack called ChoiceJacking, the first known attack to defeat juice-jacking mitigations.
“We observe that these mitigations assume that an attacker cannot inject input events while establishing a data connection,” the researchers wrote in a paper scheduled to be presented in August at the Usenix Security Symposium in Seattle. “However, we show that this assumption does not hold in practice.”
In response to the findings, Apple updated the confirmation dialogs in last month’s release of iOS/iPadOS 18.4 to require a user authentication in the form of a PIN or password. While the researchers were investigating their ChoiceJacking attacks last year, Google independently updated its confirmation with the release of version 15 in November.
The researchers say the new mitigation works as expected on fully updated Apple and Android devices. Given the fragmentation of the Android ecosystem, however, many Android devices remain vulnerable. (Dan Goodin / Ars Technica)
More than two dozen police records recently reviewed by WIRED show US law enforcement agencies regularly trained on how to take advantage of “connected cars,” with subscription-based features drastically increasing the amount of data that can be accessed during investigations.
The records make clear that law enforcement’s knowledge of the surveillance far exceeds that of the public and reveal how corporate policies and technologies, not the law, determine driver privacy.
“Each manufacturer has their whole protocol on how the operating system in the vehicle utilizes telematics, mobile wi-fi, et cetera,” one law enforcement officer noted in a presentation prepared by the California State Highway Patrol (CHP) and reviewed by WIRED. The presentation, while undated, contains statistics on connected cars for the year 2024. “If the vehicle has an active subscription,” they add, “it does create more data.”
Charlotte McCoy, a GM spokesperson, tells WIRED the company now requires a court order before handing over location data to law enforcement. (Dell Cameron / Wired)
The FBI is seeking information from the public about the Chinese Salt Typhoon hacking campaign that, last year, was found to have breached major telecommunications providers and their wiretap request systems over a two-year period.
The law enforcement agency said the Salt Typhoon hacks “resulted in the theft of call data logs, a limited number of private communications involving identified victims, and the copying of select information subject to court-ordered US law enforcement requests.” The statement affirmed reports about the cyberspies that have trickled out over the last several months after The Wall Street Journal brought the group to light this past fall.
“FBI maintains its commitment to protecting the US telecommunications sector and the individuals and organizations targeted by Salt Typhoon by identifying, mitigating, and disrupting Salt Typhoon's malicious cyber activity,” it said. “If you have any information about the individuals who comprise Salt Typhoon or other Salt Typhoon activity, we would particularly like to hear from you.”
In addition, the US Department of State's Rewards for Justice (RFJ) program is offering a reward of up to $10 million (USD) for information about foreign government-linked individuals participating in certain malicious cyber activities against US critical infrastructure in violation of the Computer Fraud and Abuse Act (CFAA). (David DiMolfetta / NextGov/FCW)
Related: IC3, Industrial Cyber, GBHackers, Homeland Security Today, The Cyber Express

Startup Lightrun, which offers a developer observability platform that detects, diagnoses, and even suggests code fixes in real time, announced it had raised $70 million in a Series B venture funding round.
Accel and Insight Partners led the round with participation from Citi, Glilot Capital, GTM Capital, and Sorenson Capital. (Meir Orbach / Calcalist)
Related: TechCrunch, Globes
Cloud native data security company Sentra announced it had raised $50 million in a Series B venture funding round.
Key1 Capital led the round with participation from existing investors Bessemer Venture Partners, Zeev Ventures, Standard Investments, and Munich Re Ventures. (Ryan Naraine / Security Week)
Related: CTech, Sentra, SiliconANGLE, Unite.AI, VC News Daily, FinSMEs, FinTech Global, Tech in Asia, Verdict
Best Thing of the Day: The Internet is Scary Enough Without Stuff Like This
Coinbase fixed a confusing bug in its account activity logs that caused users to think their credentials were compromised.
Worst Thing of the Day: Spying on Persecuted Minorities
Researchers at Citizen Lab discovered that senior members of the World Uyghur Congress (WUC) living in exile were targeted by China with a spearphishing campaign aimed at delivering Windows-based malware capable of conducting remote surveillance against its targets.
Closing Thought





