Krebs expresses outrage at Trump's gutting of cyber pros while industry rallies behind him
Take It Down Act goes to Trump's desk, Musk DOGE boys given access to highly guarded nuclear weapon data, Scattered Spider might be behind M&S attack, Zero days exploited in the wild dropped in 2024, British defense firms warned away from Chinese EVs, 4chan back after hack, so much more


Don't miss my latest CSO report on whether Secure by Design is dead at CISA and if the private sector will carry on with its pledges.
Metacurity is a reader-supported publication that requires significant work and non-trivial expenses. We rely on the generous support of our paid readers. Please consider upgrading your subscription to support Metacurity's ongoing work. Thank you.
If you're unable to commit to a subscription today, please consider donating whatever you can. Thank you!
Speaking at this year's RSA Conference, Chris Krebs, the former head of the US Cybersecurity and Infrastructure Security Agency, whom President Donald Trump targeted for investigation for affirming the integrity of the 2020 election, said he was “outraged” at the Trump administration’s gutting of cyber personnel.
The comments are the first Krebs has made in public since Trump directed the Justice Department to take action against him.
“Cybersecurity is national security. We all know that, right? That’s why we’re here. That’s why we get up every morning and do our jobs. We are protecting everyone out there. And right now, to see what’s happening to the cybersecurity community inside the federal government, we should be outraged. Absolutely outraged.”
Since January, the Trump administration has made repeated cuts to cybersecurity personnel. It has directed the agency Krebs helmed during Trump’s first administration, the Cybersecurity and Infrastructure Security Agency, to cut probationary employees and advisory committees, and it sent out two rounds of emails encouraging employees to retire.
Separately, the Electronic Frontier Foundation (EFF) and dozens of prominent cybersecurity and election security experts in an open letter urged the Trump administration to cease its politically motivated investigation of Krebs.
“By placing Krebs and SentinelOne in the crosshairs, the President is signaling that cybersecurity professionals whose findings do not align with his narrative risk having their businesses and livelihoods subjected to spurious and retaliatory targeting, the same bullying tactic he has recently used against law firms,” EFF’s letter said. “As members of the cybersecurity profession and information security community, we counter with a strong stand in defense of our professional obligation to report truthful findings, even – and especially – when they do not fit the playbook of the powerful. And we stand with Chris Krebs for doing just that.” (Kevin Collier / NBC News and EFF)
Related: EFF Letter, Politico, The Record, Washington Times, Nextgov/FCW, NBC News, SC Media, The Record, Cyberscoop, NextGov
The US House of Representatives voted overwhelmingly to pass a bill, the Take It Down Act, aimed at cracking down on the posting of sexual images and videos of people online without their consent, including AI-generated “deepfake” nudes of real people.
The bill, which passed the Senate unanimously in February, now heads to the desk of President Donald Trump, who is expected to sign it into law. The bill makes it a federal crime to publish nonconsensual intimate imagery, or NCII, of any person. It requires online platforms to remove such imagery within 48 hours when someone reports it.
That would make it the first significant internet law of Trump’s second term and the first US law to take aim at the fast-growing problem of NCII. The bill’s passage delighted many advocates for survivors and victims of revenge porn and “sextortion” scams, while some free-expression and privacy advocates said they worry it will be abused.
Critics, however, say the bill provides autocrats with the ability to scrub from the internet legitimate content they dislike and could weaponize Donald Trump's Federal Trade Commission for political ends. (Will Oremus / Washington Post)
Related: Techdirt, Information Age, CBS News, Blockchain.News, Axios, The Hill, Tech Policy Press, Benzinga, Washington Times, USA Today, Bloomberg, New York Times, Congressman Mike Johnson, The 19th, NBC News, Senate Commerce Committee, The Daily Wire, StartupNews.fyi, Deadline, r/politics, r/technology, EFF, The Verge, Ars Technica, Electronic Frontier Foundation, SiliconANGLE, Washington Examiner
Sources say two members of Elon Musk's Department of Government Efficiency were given accounts on classified networks that hold highly guarded details about America's nuclear weapons.
The networks in question are used by the National Nuclear Security Administration, the agency within the Department of Energy that oversees the nation's vast nuclear stockpile, and the Department of Defense.
The first network, known as the NNSA Enterprise Secure Network, is used to transmit detailed "restricted data" about America's nuclear weapons designs and the special nuclear materials used in the weapons, among other things. The network is used to transfer this extremely sensitive technical information between the NNSA, the nation's nuclear weapons laboratories, and the production facilities that store, maintain, and upgrade the nation's nuclear arsenal.
The second network, known as the Secret Internet Protocol Router Network (SIPRNet), is used by the Department of Defense to communicate with the Department of Energy about nuclear weapons. SIPRNet is also used more broadly for sharing information classified at the secret level, information that "could potentially damage or harm national security if it were to get out," explained a former career civil servant at the Department of Defense who requested anonymity to discuss classified systems.
Luke Farritor, a 23-year-old former SpaceX intern, and Adam Ramada, a Miami-based venture capitalist, have had accounts on the computer systems for at least two weeks. Before their work at DOGE, neither Farritor nor Ramada appeared to have had experience with either nuclear weapons or handling classified information.
A spokesperson for the Department of Energy initially denied that Farritor and Ramada had accessed the networks.
"This reporting is false. No DOGE personnel have accessed these NNSA systems. The two DOGE individuals in question worked within the agency for several days and departed DOE in February," the spokesperson told NPR in an emailed statement.
In a second statement, the spokesperson clarified that the accounts had been created but said the DOGE staffers never used them. "DOE is able to confirm that these accounts in question were never activated and have never been accessed," the email statement read. (Geoff Brumfiel, Jenna McLaughlin / NPR)
Related: Daily Beast
Sources say ongoing outages at British retail giant Marks & Spencer are caused by a ransomware attack believed to be conducted by the hacking collective known as Scattered Spider.
The threat actors are believed to have first breached M&S as early as February, when they reportedly stole the Windows domain's NTDS.dit file.
An NTDS.dit file is the main database for Active Directory Services running on a Windows domain controller. This file contains the password hashes for Windows accounts, which can be extracted by threat actors and cracked offline to gain access to associated plaintext passwords.
Using these credentials, a threat actor can then laterally spread throughout the Windows domain, while stealing data from network devices and servers.
Sources said that the threat actors ultimately deployed the DragonForce encryptor to VMware ESXi hosts on April 24th to encrypt virtual machines. Marks and Spencer asked for help from CrowdStrike, Microsoft, and Fenix24 to investigate and respond to the attack.
The investigation so far indicates that the hacking collective known as Scattered Spider, or as Microsoft calls them, Octo Tempest, is behind the attack. (Lawrence Abrams / Bleeping Computer)
Related: Tech Monitor, Sky News, Cyber Daily, BBC News, iNews
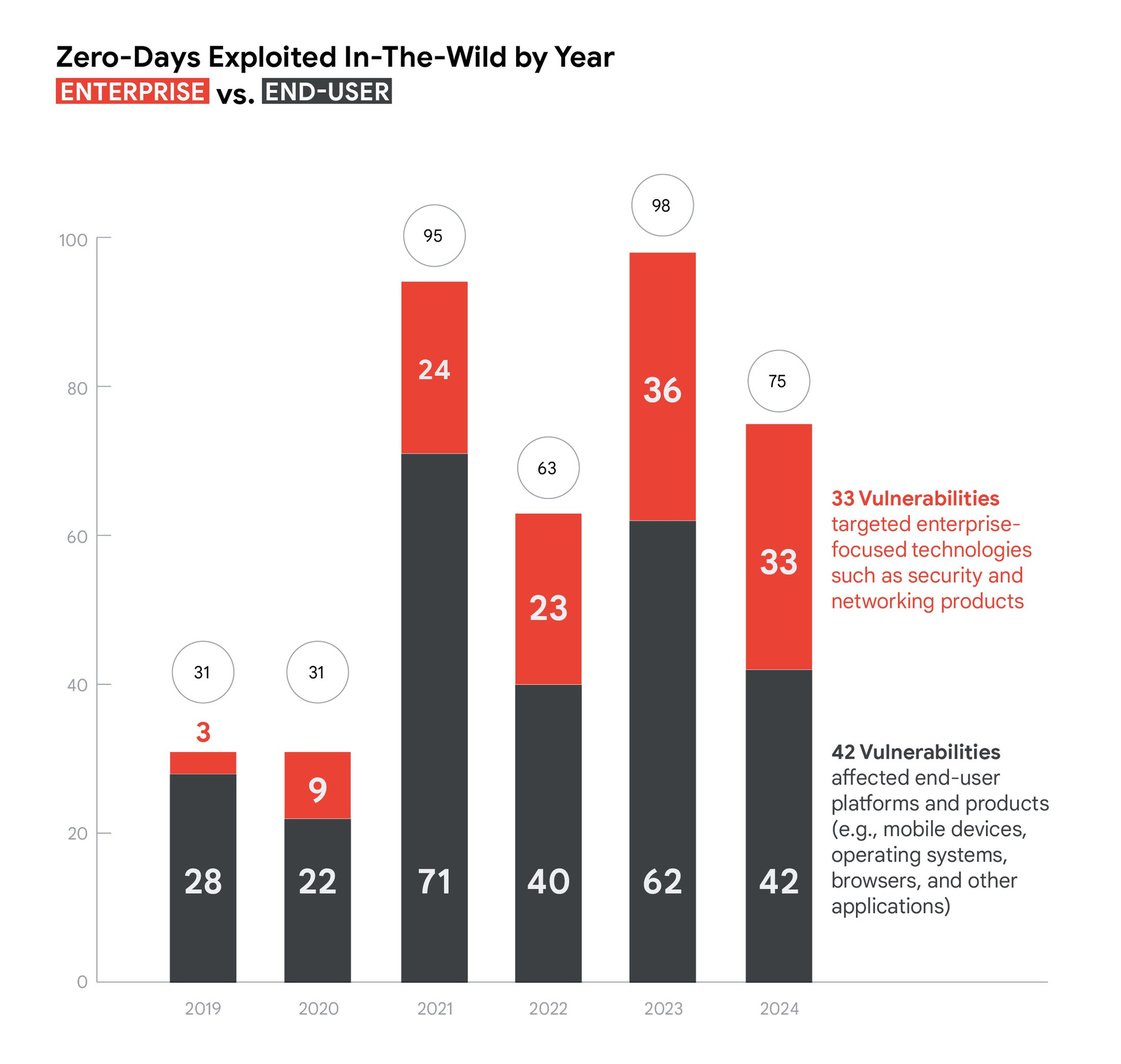
Google Threat Intelligence (GTIG) said it had tracked 75 zero-day vulnerabilities exploited in the wild in 2024, a decrease from the number we identified in 2023 (98 vulnerabilities), but still an increase from 2022 (63 vulnerabilities).
The tech giant says it sees zero-day exploitation targeting a greater number and wider variety of enterprise-specific technologies, although these technologies remain a smaller proportion of overall exploitation when compared to end-user technologies.
Of the proportion of zero-days that Google could attribute, at least 23 zero-day exploits were linked to government-backed hackers. Among those 23 exploits, 10 zero-days were attributed to hackers working directly for governments, including five exploits linked to China and another five to North Korea.
Another eight exploits were identified as having been developed by spyware makers and surveillance enablers, such as NSO Group, which typically claim to only sell to governments. Among those eight exploits made by spyware companies, Google is also counting bugs that were recently exploited by Serbian authorities using Cellebrite phone-unlocking devices.
Google did continue to see an increase in adversary exploitation of enterprise-specific technologies throughout 2024. In 2023, 37% of zero-day vulnerabilities targeted enterprise products. This jumped to 44% in 2024, primarily fueled by the increased exploitation of security and networking software and appliances. (Casey Charrier, James Sadowski, Clement Lecigne, Vlad Stolyarov / GTIG and Lorenzo Franceschi-Bicchierai / TechCrunch)
Related: Infosecurity Magazine, SiliconANGLE, Security Affairs, Security Week
The US Department of Health and Human Services fined a New York neurology practice, Comprehensive Neurology, $25,000 following an investigation into a 2020 ransomware breach affecting nearly 7,000 individuals.
HHS said the practice failed to conduct an accurate and thorough risk analysis to determine the potential risks and vulnerabilities to its electronic protected health information. The settlement also imposes a corrective action plan on the practice.
The settlement is HHS' Office for Civil Rights' 12th ransomware-related HIPAA enforcement action since that effort was kicked off in 2023. It marks the eighth enforcement action under the agency's security risk analysis initiative, which launched last year. (Marianne Kolbasuk McGee / BankInfoSecurity)
Related: HHS, The HIPAA Journal
British firms working for the UK’s military or intelligence services are advising staff not to connect their mobile phones to Chinese-made electric cars over fears that Beijing could steal sensitive national security data.
Executives at two of the nation’s leading defence giants said that the entire sector is taking a “cautious” and “belt and braces” approach to the possibility of the Chinese state spying on staff via the country’s electric vehicles (EVs).
The security clampdown within the UK’s highly secretive defence sector follows revelations that the Ministry of Defence (MoD) has banned cars relying on Chinese technology from sensitive military sites across the country. In some cases, the MoD has asked staff to park their EVs at least two miles from their workplace. (David Parsley / The iPaper)
Related: The Guardian, The Telegraph, Daily Mail, The Times
An investigation by Australian cybersecurity firm Dvuln revealed that more than 31,000 passwords belonging to Australian customers of the Big Four banks are being shared amongst cyber criminals online, often for free.
The investigation showed that credentials belonging to at least 14,000 Commbank customers, 7,000 ANZ customers, 5,000 NAB customers, and 4,000 Westpac customers are available on the messaging platform Telegram and the dark web.
It comes in the wake of recent attacks on Australian superannuation funds, where hackers stole from pensioners and used leaked passwords to try to gain access to members' accounts.
"This is not a vulnerability in the banks," Dvuln's founder Jamie O'Reilly said. "These are customer devices that have been infected" by infostealer malware. (Ange Lavoipierre / ABC.net.au)
Related: 9News, The Nightly, News.com, AA, Information Age, Pedestrian TV
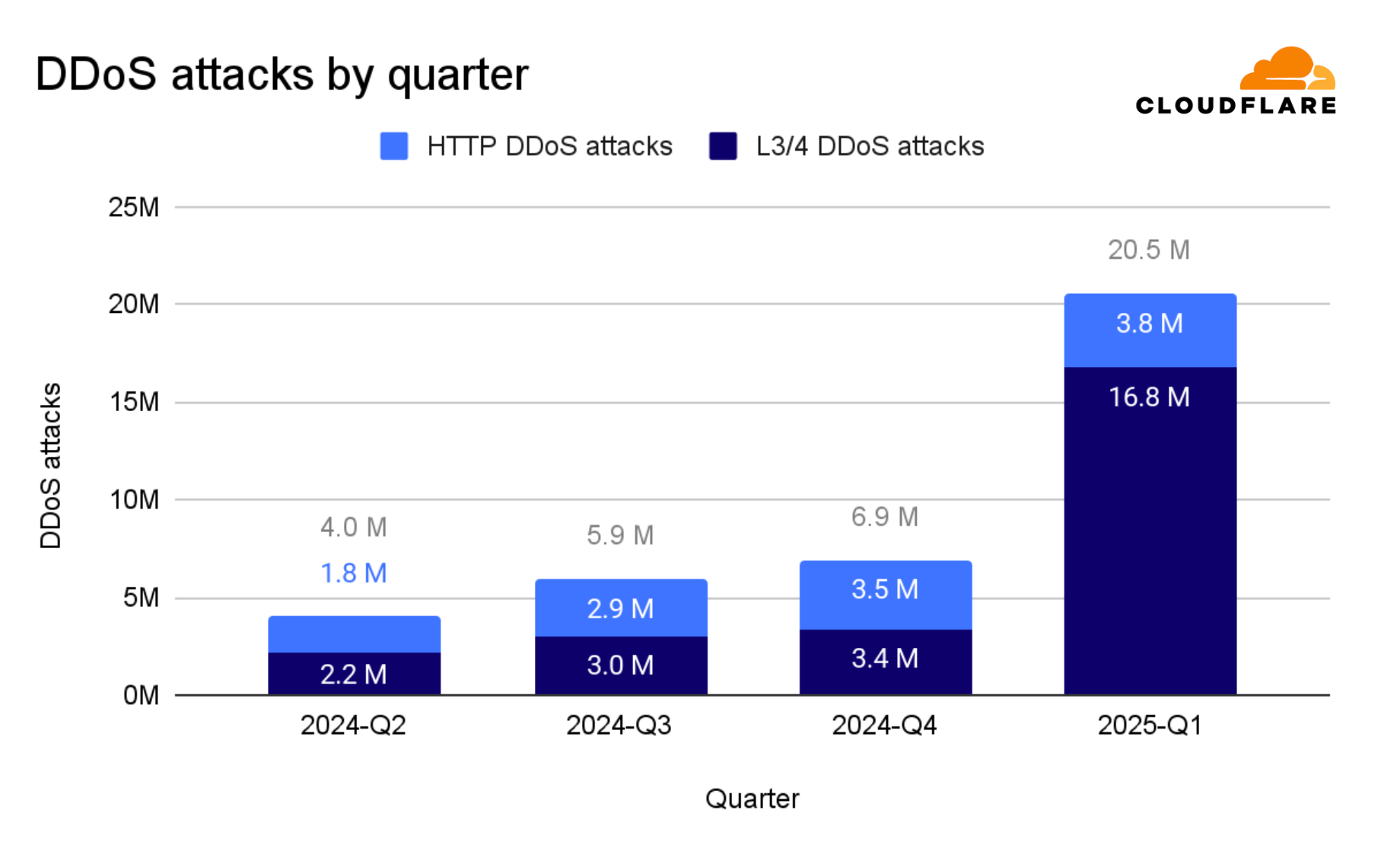
In its 2025 Q1 DDoS Report, Cloudflare said it mitigated a record number of DDoS attacks in 2024, recording a massive 358% year-over-year jump and a 198% quarter-over-quarter increase.
The company said it mitigated a total of 21.3 million DDoS attacks in 2024.
However, 2025 is looking to be an even bigger problem for online entities and companies, with Cloudflare already responding to 20.5 million DDoS attacks in just the first quarter of 2025.
These attacks include Cloudflare itself, whose infrastructure was targeted directly in 6.6 million attacks over an 18-day multi-vector campaign. "Of the 20.5 million DDoS attacks, 16.8M were network-layer DDoS attacks, and of those, 6.6M targeted Cloudflare's network infrastructure directly," explains Cloudflare.
"These attacks were part of an 18 day multi-vector DDoS campaign comprising SYN flood attacks, Mirai-generated DDoS attacks, SSDP amplification attacks to name a few."
The largest driver of this increase was network-layer attacks, which saw the sharpest growth in recent months, gaining 509% YoY. (Bill Toulas / Bleeping Computer)
Related: Cloudflare, Help Net Security
Researchers from the cybersecurity firm Oligo revealed what they’re calling AirBorne, a collection of vulnerabilities affecting AirPlay, Apple’s proprietary radio-based protocol for local wireless communication.
Bugs in Apple’s AirPlay software development kit (SDK) for third-party devices would allow hackers to hijack gadgets like speakers, receivers, set-top boxes, or smart TVs if they’re on the same Wi-Fi network as the hacker’s machine.
Another set of AirBorne vulnerabilities would have allowed hackers to exploit AirPlay-enabled Apple devices too, Apple told Oligo, though these bugs have been patched in updates over the last several months, and Apple says that those bugs could have only been exploited when users changed default AirPlay settings. (Lily Hay Newman and Andy Greenberg / Wired)
SentinelOne says that cybersecurity companies are frequently targets of threats themselves including ransomware, Chinese government-sponsored hackers and North Korean IT workers posing as job applicants.
SentinelOne said it had tracked roughly 360 fake personas and 1,000 job applicants with links to North Korean IT worker operations applying for SentinelOne jobs, including those trying to get jobs on the SentinelLabs intelligence engineering team. In investigating the campaign, SentinelOne concluded that there was value in sharing threat info with different, non-investigative teams, in this case, recruiters.
Ransomware operators have targeted SentinelOne as part of an underground economy geared toward buying, selling, or renting access to enterprise security tools. They include a group operated by a Russian national.
Chinese state-sponsored hackers targeting the company include a group known for targeting critical infrastructure around the globe, such as telecommunications, IT, and government organizations. (Tim Starks / Cyberscoop)
Related: SentinelOne, Cybernews
Several DuPage County offices in Illinois were the victims of a ransomware attack, officials announced.
County officials say the attack affected the sheriff’s office, the 18th Judicial Circuit Court, and the DuPage County Circuit Court Clerk’s office.
“This afternoon, DuPage County confirmed it had been the target of a ransomware attack,” Chief Judge Bonnie Wheaton, Circuit Court Clerk Candice Adams, and Sheriff Jim Mendrick said. “Systems have been taken offline, and the County is working to determine the full extent of the attack."
The county has reported the attack to the FBI and the Secret Service. (Susan Sarkauskas / The Daily Herald)
Related: Chicago Tribune, Positively Naperville, ABC7, Chicago Sun-Times
Employee benefits administration firm VeriSource Services is warning that a data breach exposed the personal information of four million people.
The firm has begun data breach notifications to impacted individuals about a cybersecurity incident that occurred in February 2024, but the impact of which it took them until April 2025 to evaluate.
According to VeriSource's investigation, the incident exposed sensitive information to external threat actors.
"On February 28, 2024, VSI became aware of unusual activity that disrupted access to certain systems," reads the firm's notice shared with the authorities.
"Upon discovery, VSI immediately took steps to secure its network and engaged a leading, independent digital forensics and incident response firm to investigate what happened and whether any sensitive data may have been impacted."
"The investigation subsequently revealed that certain personal information may have been acquired without authorization by an unknown actor on or about February 27, 2024."
Related: Maine Attorney General, Security Week, The Register, Security Affairs
Hitachi Vantara, a subsidiary of Japanese multinational conglomerate Hitachi, was forced to take servers offline over the weekend to contain an Akira ransomware attack.
The company provides data storage, infrastructure systems, cloud management, and ransomware recovery services to government entities and some of the world's biggest brands, including BMW, Telefónica, T-Mobile, and China Telecom.
One source said the attack has also affected multiple projects owned by government entities.
Hitachi Vantara said it hired external cybersecurity experts to investigate the incident's impact and is now working on getting all affected systems online.
"On April 26, 2025, Hitachi Vantara experienced a ransomware incident that has resulted in a disruption to some of our systems," Hitachi Vantara said. (Sergiu Gatlan / Bleeping Computer)
Related: Techzine
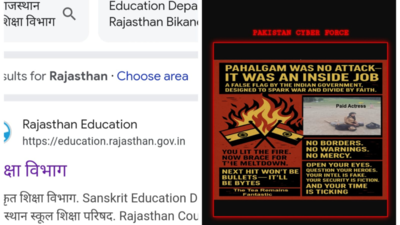
The official website of the Rajasthan Education Department in New Delhi, India, was hacked, with the home page displaying the name Pakistan Cyber Force.
A message on the homepage read: “Pahalgam was no attack – it was an inside job… You lit the fire, now brace for the meltdown.
The message further stated: “No borders. No warnings. No mercy… The next hit won’t be bullets — it’ll be bytes…”
After the incident came to light, the Education Department restored the home page to its original content. (Suparna Roy / Times of India)
Related: Pragativadi, Munsif News, Free Press Journal
Controversial online forum 4chan is partly back online after a hack took the infamous image-sharing site down for nearly two weeks.
The site first went down on April 14, with the person responsible for the hack leaking data, including a list of moderators and “janitors” (one janitor said they were “confident” that the leaked data was real).
On Friday, the site came back online. Shortly afterward, a post on the official 4chan blog said “a hacker using a UK IP address” was able to gain access to one of 4chan’s servers using a “bogus PDF upload,” subsequently “exfiltrating database tables and much of 4chan’s source code,” then beginning to “vandalize 4chan at which point moderators became aware and 4chan’s servers were halted, preventing further access.”
The damage, the post said, was “catastrophic.”
The breached server was subsequently replaced, the post said, although the site has new limitations — PDF uploads are “temporarily” disabled, and a board for sharing Flash animations has been left offline as the team saw “no realistic way to prevent similar exploits using .swf files.” (Anthony Ha / TechCrunch)
Related: 4Chan Blog, Engadget, PC Mag, The Express Tribune, NewsBytes
The US cybersecurity agency CISA issued a warning on the active exploitation of recently patched vulnerabilities in Broadcom, Commvault, and Qualitia products.
The Broadcom flaw, tracked as CVE-2025-1976 (CVSS score of 8.6), is described as a code injection issue that could allow an authenticated attacker with administrative privileges to execute arbitrary code as root.
“Through a flaw in IP address validation, a local user, assigned one of the pre-defined admin roles or a user-defined role with admin-level privileges, can execute arbitrary code as if they had full root-level access,” Broadcom explains in its advisory.
Certain 11.x versions of the Commvault web server are impacted by an unspecified vulnerability, tracked as CVE-2025-3928 (CVSS score of 8.7), that can be exploited by a remote, authenticated attacker to compromise the instance by “creating and executing webshells."
The Qualitia flaw is a stack-based buffer overflow defect in Active! mail 6 that could be exploited by a remote, unauthenticated attacker via crafted requests. Tracked as CVE-2025-42599 (CVSS score of 9.8), the issue would lead to remote code execution or denial-of-service (DoS) conditions. (Ionut Arghire / Security Week)
Related: CISA, Security Affairs, GBHackers, Broadcom
Cybersecurity giant Palo Alto Networks plans to acquire Protect AI, a Seattle startup founded in 2022 that helps companies monitor the various layers and components of machine learning systems, in a deal that sources say is worth more than $500 million.
Palo Alto said the acquisition will help expand its capabilities “to protect the dynamic new attack surface created by the explosion of AI.” The company also announced a new AI security platform called Prisma AIRS. (Taylor Soper / GeekWire)
Related: Palo Alto Networks, Salesforce Ventures, The Information, SiliconANGLE, Channel Futures, Security Boulevard, Constellation Research, Investor's Business Daily, CRN, Bloomberg
Zero-trust networking startup NetFoundry Inc. said it has received its first cash injection from venture capitalists, raising $12 million in funding.
SYN Ventures led the funding round. (Mike Wheatley / Silicon Angle)
Related: Industrial Cyber, Business Wire, FinSMEs
Pistachio, an Oslo-based "automated awareness training platform" for cybersecurity, has raised $7M in a Series A venture funding round.
Walter Ventures led the round with participation from Idékapital, Angel Invest, MP Pensjon, and J12 Ventures. (Lucy Adams / Tech.eu)
Related: Tech Funding News, FinSMEs
Best Thing of the Day: An Expensive Line of Code
Software developer Adam Pietrasiak came clean in a blog post, revealing how a stupid bug in his company's screen recorder app screen.studio app kept downloading the auto-update file repeatedly, every 5 minutes for every single user, resulting in 9 million file downloads and more than 2 petabytes of traffic on Google Cloud, costing the company $8,000.
Worst Thing of the Day: Punching Healthcare Systems in the Eye
Oracle engineers mistakenly triggered a five-day software outage at a number of Community Health Systems hospitals, causing the facilities to return to paper-based patient records temporarily, a giant goof coming weeks after the company’s federal electronic health record experienced a nationwide outage.
Closing Thought