Judge stops DOGE access to Treasury systems, slams data access process
Top Russian IT provider breached, 'OpenAI' job scams stole from Bangladesh workers, Warby Parker hit with $1.5m fine, Chinese cyber firm's details exposed, Google unveils quantum-safe digital signatures, Threat actors defraud Steam gamers, Detroit PBS cops to 2024 breach, much more


Don't miss my latest CSO piece, which examines how security leaders can ease the mental health burdens of serious cybersecurity incidents.
Metacurity is mostly a reader-supported publication that relies on the generous support of our paid readers. Please consider supporting Metacurity with an upgraded subscription.
If you can't commit to a subscription today, please consider donating whatever you can. Thank you!
In a glimmer of hope that the US justice system might serve as a check on the seemingly unlimited power of Elon Musk, US District Court Judge Jeannette Vargas extended an order to keep Musk’s DOGE team out of Treasury Department payment systems, ruling that the Trump administration’s process for granting access to sensitive data was so flawed and haphazard that it was likely illegal.
Vargas ruled that Democratic attorneys general were likely to prevail in their claim that Treasury acted arbitrarily and capriciously in giving two DOGE employees access to the systems that control trillions of dollars of federal payments each year.
She also ruled that the Treasury’s “rushed and ad hoc process” for granting DOGE access to the payment systems created a “realistic danger that confidential financial information will be disclosed.”
Vargas dinged Treasury officials for standing up its DOGE operation in a “chaotic and haphazard” manner. The agency moved with “inexplicable urgency” to permit its DOGE team to access critical payment systems, Vargas wrote, leaving career staff “with almost no time” to develop measures to mitigate the “serious risks that access entailed.”
The preliminary injunction Vargas issued prohibits anyone affiliated with the US DOGE Service or the Treasury DOGE team from accessing federal payment systems until further notice. This is narrower than an earlierThis nearly all political appointees from barred the data.
Judge Vargas said that Treasury’s explanations for the hurried process were “riddled with inconsistencies” and “lack credibility.” She said that Treasury’s error in briefly granting one DOGE employee, Marko Elez, full access to the payment system instead of “read-only” access was emblematic of a “hurried” and flawed process. She also raised questions about the adequacy of Treasury’s training and vetting of DOGE employees.
Among her other observations was that DOGE worker Marco Elez and his ostensible boss, Thomas Krause, were not seemingly provided any specific training on the numerous federal regulations and policies governing the handling and care of sensitive information.
She also noted that Elez was issued a secure laptop, but his activities at Treasury were only monitored for one day. His activities were only monitored via logging, and Treasury is reviewing those logs to determine what actions Elez took concerning PAM while he had access to those systems.
She further found that
- It's unclear if any measures were employed or were adequate to protect against unauthorized disclosures of the information contained in the BFS systems.
- Elez emailed data outside the dept. but Treasury cannot say what he emailed or whether it was sensitive data.
- No forensic review was conducted of Elez’s activity, and the logs were not reviewed to determine what he was doing when he had access to certain source codes and payment systems. (Michael Stratford / Politico and Metacurity)
Related: Court Listener, SC World, Fedscoop, Meritalk, Courthouse News, CNBC, The Hill, Federal News Network, Reuters, Ars Technica
Russia's National Coordination Center for Computer Incidents (NKTsKI) is warning organizations in the country's credit and financial sector about a breach at LANIT, a major Russian IT service and software provider.
According to the organization's bulletin, the attack occurred on February 21, 2025, and potentially impacted LLC LANTER and LLC LAN ATMservice, both part of the LANIT Group of Companies.
LANIT serves prominent entities such as the Russian Ministry of Defense and major players in the military-industrial complex, including Rostec, which is why the US Department of the Treasury sanctioned it in May 2024.
LLC LANTER and LLC LAN ATMservice are Russian companies that specialize in banking technology and services, including software for banking equipment, payment systems, and Automated Teller Machines (ATMs).
Due to the breach at these two entities, NKTsKI recommends all potentially impacted organizations rotate passwords and access keys and change remote access credentials. (Bill Toulas / Bleeping Computer)
Related: Gossopka.ru, Security Affairs, TechRadar
Sponsored Interview
What exactly is zero trust again?
Last week, a spotlight was cast on the concept of zero trust in Orlando, FL, when ThreatLocker held its annual Zero Trust World. Although a desired goal and a buzzy term in cybersecurity, the phrase zero trust has so many variations that it can lose meaning.
IBM, for example, defines zero trust as "a security strategy for modern multicloud networks. Instead of focusing on the network perimeter, a zero trust security model enforces security policies for each individual connection between users, devices, applications and data."
The Cybersecurity and Infrastructure Security Agency says zero trust "provides a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised."
Gartner defines zero trust "as a mainstay of modern security strategies, taking over from traditional 'castle-and-moat' network security models in which no one outside the network can access data on the inside, but everyone inside the network can."
Although all of these and other definitions of zero trust are interconnected, their varying nature can lead to an imprecise grasp of how to go about implementing ideas and technologies that all share the fundamental goal of keeping harmful software out of good networks. Or, in the words of Rob Allen, ThreatLocker's Chief Product Officer, "It's all about stopping things from being weaponized."
Zero trust is defined as "Grant access only to any service node or user only where access is required to perform its function," Danny Jenkins, CEO and Co-Founder of ThreatLocker, told Metacurity. "That, in my mind, is what zero trust means. There's a whole framework around it, but the philosophy is very simple. It's the new word for least amount of privilege."
Jenkins emphasized that "the bottom line is it means only grant where access is required to only allow an application to run if it needs to run. It's irrelevant whether it's good or bad, it's not allowed."
Allen defines zero trust more succinctly. "It's to deny by default," he told Metacurity. But, he conceded, "there's a number of definitions that have been used. One way to look at it is about removing implicit trust and adding explicit trust. Removing implied trust from implicit trust and adding explicit trust is one way of looking at it."
Yet another way to look at it is "to give people access or only the access that they need to do their jobs and no more is another way of looking at it," Allen said. "Probably my favorite way of looking at it is it was an executive order that the US government brought out a number of years ago, and what they said was to assume a breach is inevitable or has already likely occurred."
ThreatLocker's model of zero trust is achieved through a series of menu-driven options where allow access to any serviced node is denied by default, which runs contrary to the industry standard of letting everything in but blocking only those things you find undesirable and permit access only as exceptions. Once access is granted, everything is ring-fenced to create boundaries around approved applications to control their actions.
Of course, Jenkins believes if the whole world followed this approach to zero trust, cybercriminals would give up in frustration. "If the whole world did this and they did it right, cybercrime would be an unprofitable business that turned to do something else."
According to FTC complaints, an alleged job scam led by someone named "Aiden" from "OpenAI "recruited workers in Bangladesh for months before disappearing overnight.
After connecting with the startup on Telegram and creating an account through a ChatGPT-branded app, a Bangladeshi worker invested crypto into the platform and began a months-long job working for “Aiden” from “OpenAI.”
The work was performed through the website “OpenAi-etc,” and internal conversations were held on Telegram. The process is simple: Invest crypto, complete a few tasks, and earn daily profits based on the investment.
During this worker’s tenure with the company, mentors continuously encouraged them to invest more money in the fund and recruit more Bangladeshi people to the team. The worker convinced over 150 to join, and the mentors divided the growing team of “brokers” into a hierarchy based on seniority.
All seemed well until the morning of August 29, 2024, when everyone woke up to find that the website, all of their money, Aiden, and the other fake OpenAI employees had vanished overnight.
A review of domain name system records for the now-defunct OpenAi-etc website shows that it appears to have been hosted by a China-based web hosting company. (Reece Rogers / Wired)
Related: dev.ua
The Department of Health and Human Services (HHS) Office for Civil Rights, which oversees the Health Insurance Portability and Accountability Act (HIPAA) rules, fined eyewear retailer Warby Parker $1.5 million in 2018 for a credential stuffing attack that compromised the personal information of nearly 200,000 people.
Warby Parker failed “to conduct an accurate and thorough risk analysis to identify potential risks and vulnerabilities” to electronic personal health information, HHS said and didn’t implement security measures to reduce risks to patient information.
The company first detected unusual log-in activity in November 2018 and determined that a third party had gained access to customer accounts by credential stuffing, a method in which a hacker uses log-in information obtained elsewhere to try to breach accounts.
The compromised information included names, addresses, payment information, and records related to eyewear prescriptions. After smaller incidents affecting fewer than 500 people, Warby Parker filed two other breach reports in April 2020 and June 2022.
According to the OCR, as of September 2024, Warby Parker had still not conducted an assessment of the “potential risks and vulnerabilities” to the confidentiality of the health information.
They said the company didn’t implement reasonable security measures around sensitive information until July 2022 and didn’t review “records of information system activity review” until May 2020. (James Reddick / The Record)
Related: HHS, SC World, TechTarget, BankInfoSecurity
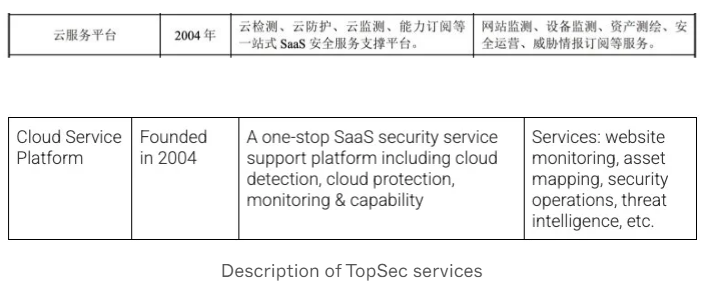
The SentinelLABS threat research team revealed that a data leak from TopSec, a prominent Chinese cybersecurity firm, has exposed details about the company’s operations and its probable involvement in internet censorship for the Chinese government.
The team analyzed the leaked data, including over 7,000 lines of work logs and code used for DevOps practices. The data revealed scripts connecting to Chinese government hostnames, academic institutions, and news sites, suggesting TopSec’s services extend to a wide range of organizations.
The documents detail TopSec’s involvement in projects for Bureaus of the Ministry of Public Security in several cities, including Shanghai, suggesting their participation in monitoring website security and content. One such project, the “Cloud Monitoring Service Project,” involved monitoring website security and content with alerts for breaches or policy violations.
The data, submitted to a multi-scanner platform, includes employee work logs, scripts, and commands used for infrastructure administration. It features DevOps technologies like Ansible, Docker, and Kubernetes. Critically, hardcoded credentials were found, posing a significant security risk. (Deeba Ahmed / HackRead)
Related: Sentinel Labs, SC Media
Google announced the development of quantum-safe digital signatures (FIPS 204/FIPS 205) in Google Cloud Key Management Service (Cloud KMS) for software-based keys.
The search giant also provided a high-level view into its post-quantum strategy for Google Cloud encryption products, including Cloud KMS and the Cloud Hardware Security Module (Cloud HSM).
This development is significant because the security of many of the world’s most widely used public-key cryptography systems has become a concern as experimental quantum computing advances. Large, cryptographically relevant quantum computers have the potential to break these algorithms.
However, using existing hardware and software post-quantum cryptography (PQC) can mitigate these risks. In August 2024, the National Institute of Standards and Technology (NIST) released new PQC standards, enabling tech vendors worldwide to begin PQC migrations. (Esther Shein / TechRepublic)
Related: Google, SC Media, The Quantum Insider, Bleeping Computer, BankInfoSecurity, Techzine
Researchers at Bitdefender Labs report that threat actors are exploiting major Counter-Strike 2 (CS2) competitions, like IEM Katowice 2025 and PGL Cluj-Napoca 2025, to defraud gamers and steal their Steam accounts and cryptocurrency.
The security firm warns that threat actors impersonate professional CS2 players like S1mple, NiKo, and Donk in live streams on YouTube, promoting fake CS2 skins and cryptocurrency giveaways.
The channels that promote these scams are hijacked legitimate YouTube accounts, which the scammers rebrand as needed to impersonate professional players.
What they show in these livestreams is loops of old gameplay footage, making it appear live to anyone who hasn't watched them before.
Bitdefender says these scams often use names of legitimate platforms like CS.MONEY or esports sponsorships to further enhance the deception. (Bill Toulas / Bleeping Computer)
Related: Bitdefender, The Record, HackRead
Detroit PBS notified 1,694 people about a data breach in August 2024 that compromised a significant amount of their personal information.
The public broadcaster says unauthorized users accessed its systems between August 12 and August 31, 2024. Ransomware gang Qilin claimed responsibility for the breach on September 23, 2024, saying it stole 573 GB of data.
Detroit PBS is offering eligible victims 12 months of free credit monitoring via Experian. The deadline to enroll is May 30, 2025. (Paul Bischoff / Comparitech)
Related: Cybernews, Maine Attorney General

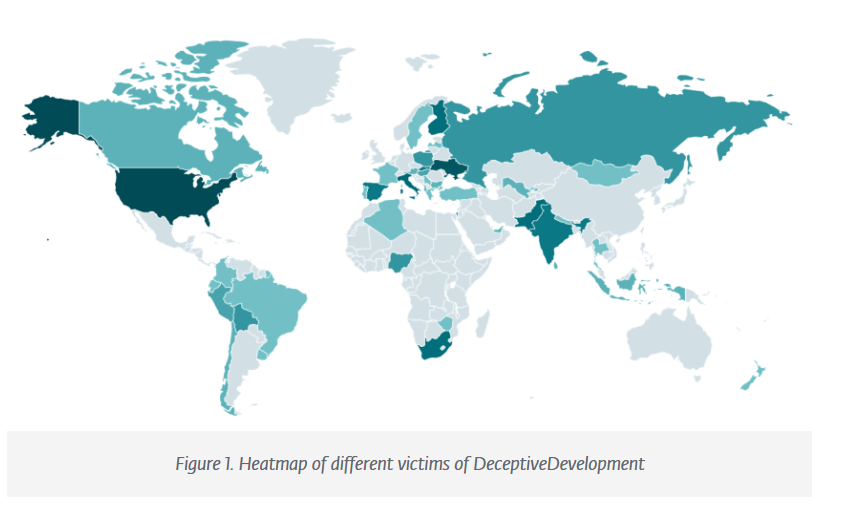
Researchers at ESET report that hundreds of freelance software developers, ranging from junior developers to highly experienced professionals, have been targeted and infected with North Korean malware over the past year in a campaign they call DeceptiveDevelopment.
As part of the attacks, ongoing since early 2024, the threat actors relied on fake personas and copied profiles to pose as software development recruiters and convince victims to download software projects that contained malware.
North Korean hackers have long been using fake job offers to deliver malware to unsuspecting victims, either for espionage or financial gain. ESET notes that the DeceptiveDevelopment campaign follows the same patterns.
On platforms like LinkedIn, Upwork, Freelancer.com, We Work Remotely, Moonlight, and Crypto Jobs List, the attackers post fake job offerings or approach targets looking for employment to convince them to download a malicious project.
ESET warns that the targets are asked to inspect the software project, which is delivered either via file transfer or through a link to a private repository on GitHub, GitLab, or Bitbucket,. They are then asked to compile and execute the project and report any issues discovered back to the fake recruiter (Ionut Arghire / Security Week)
Related: WeLiveSecurity, Infosecurity Magazine
US-based employee screening services company DISA Global Solutions said it suffered a data breach that affected more than 3.3 million people.
DISA, which provides services like drug and alcohol testing and background checks to more than 55,000 enterprises and a third of Fortune 500 companies, confirmed the data breach in a filing with Maine’s attorney general on Monday.
DISA said it discovered it had been the victim of a “cyber incident” that affected a “limited portion” of its network on April 22, 2024. An internal investigation determined that a hacker had infiltrated the company’s network on February 9, 2024, where they went unnoticed for over two months.
In a letter to those affected by the data breach, including individuals who underwent employee screening tests, DISA said the attacker “procured some information” from its systems.
In a separate filing with the Massachusetts attorney general, DISA confirmed the stolen information included individuals’ Social Security numbers, financial account information including credit card numbers, and government-issued identification documents.
This filing confirmed that more than 360,000 Massachusetts residents were affected by the breach. (Carly Page / TechCrunch)
Related: Maine Attorney General, CyberInsider
Google wants to replace text-based two-factor authentication with QR codes when creating a new Gmail account.
Google wants to “move away from sending SMS messages for authentication” when creating a new Gmail/Google account.
In a preview, Google said it is “reimagining how we verify phone numbers.” Historically, the process involves entering a phone number and getting a 6-digit code over an SMS/text message that a user has to enter online to complete the account creation process.
SMS codes present numerous security challenges, according to Gmail spokesperson Ross Richendrfer and his colleague at Google, Kimberly Samra. They can be phished, people don’t always have access to the device the codes are sent to, and they are reliant on the security practices of the user’s carrier. “If a fraudster can easily trick a carrier into getting hold of someone’s phone number,” Richendrfer said, any “security value of SMS goes away.” (Davey Winder / Forbes)
Related: Gigazine, 9to5Google, Gadgets 360, The Verge, Android Authority, The Tech Portal, Inc.
AI-driven defense platform company Rad Security announced it had raised $14 million in a Series A venture funding round.
Cheyenne Ventures led the round, which included participation from Forgepoint Capital, Lytical Ventures, Akamai, .406 Ventures, Vertex Ventures, and Gula Tech Adventures. (Eduard Kovacs / Security Week)
Related: Silicon Angle, FinSMEs
Israeli cybersecurity company Skybox Security has laid off all its employees and ceased operations.
The company employed approximately 100 people in Israel and another 200 in the United States.
In Israel, employees were informed that their final salary would not be paid and were advised to contact the National Insurance Institute.
Skybox’s CEO, Mordecai Rosen, met with employees to officially announce the company's closure and layoffs. Simultaneously, an email was sent to all employees regarding their next steps.
Skybox sold all of its business and technology to Israeli cybersecurity company Tufin. (Meir Ohrbach / CTech)
Related: CTech, TechInAsia, Ynet News
Best Thing of the Day: How to Become a Billionaire
Chainalysis issued a report that details how the North Korean hackers managed to steal $1.5 billion from Bybit.
Worst Thing of the Day: It's All Part of Their Plan
The layoffs at CISA and the efforts to dismantle US foreign efforts to fight foreign disinformation meddling are making US elections less secure.
Closing Thought