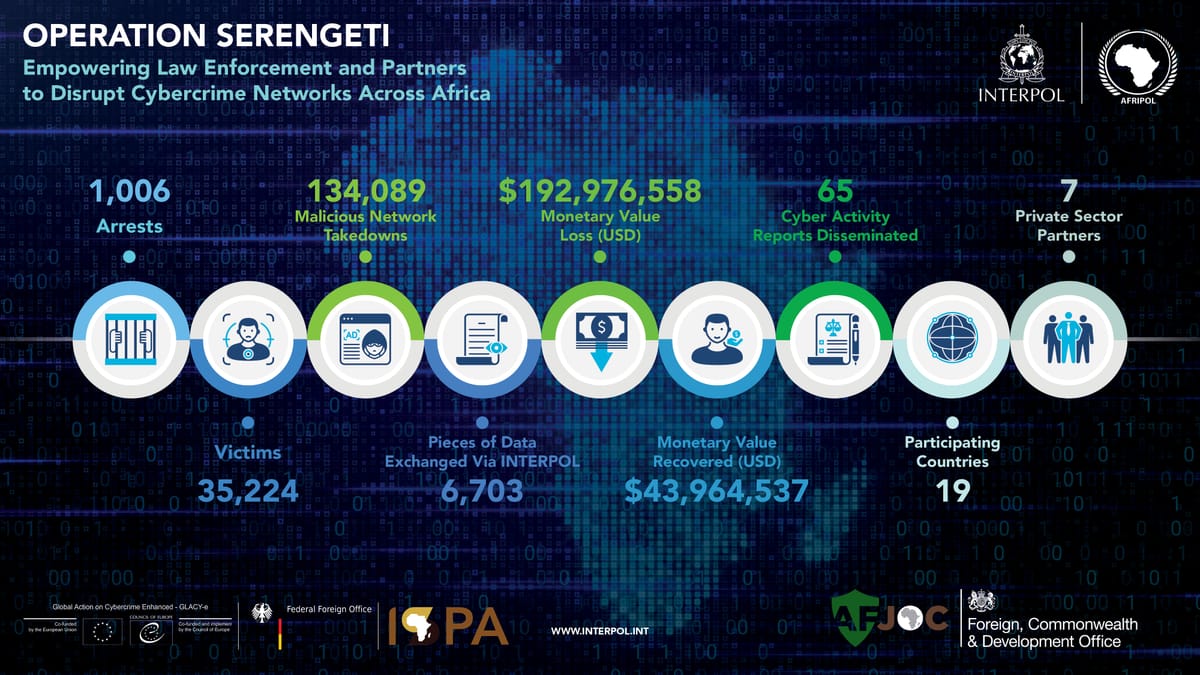
Interpol Busts 1,006 Suspects in Africa for a Host of Financial Cybercrimes
The third Snowflake suspect might be a US Army soldier, US court reverses sanctions on Tornado Cash, RomCom group chained zero days to target Firefox and Tor browsers, Uniswap offers $15.5m bug bounty, CrowdStrike can't gauge financial impact of July outage yet, much more