FBI: Online scams stole nearly $17 billion in 2024, up sharply from 2023 levels
Hijacked brokerage accounts in Japan juiced $710m in fraudulent trading since Feb., BreachForums reportedly rises again, New malware appears in apps Russian soldiers use, S. Korea says DeepSeek transferred user data w/o permission, Millions affected by Blue Shield CA 2021 breach, so much more
Metacurity is a reader-supported publication that requires significant work and non-trivial expenses. We rely on the generous support of our paid readers. Please consider upgrading your subscription to support Metacurity's ongoing work. Thank you.
If you're unable to commit to a subscription today, please consider donating whatever you can. Thank you!
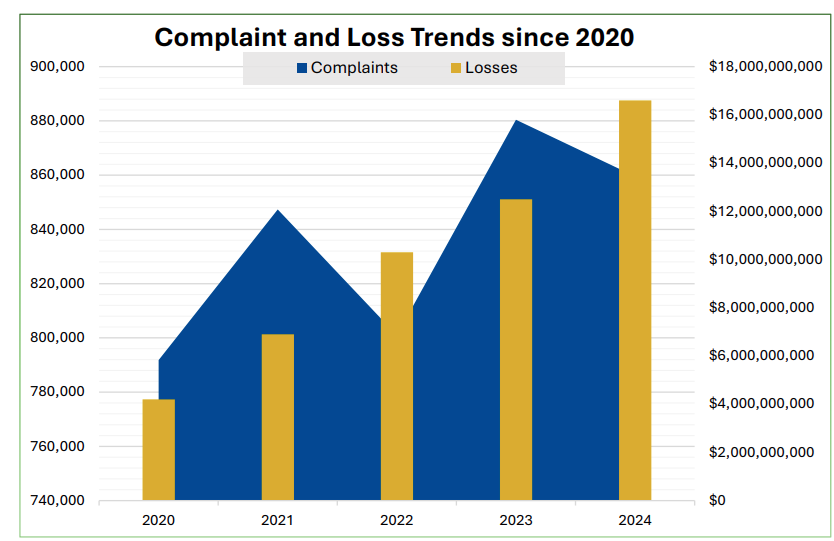
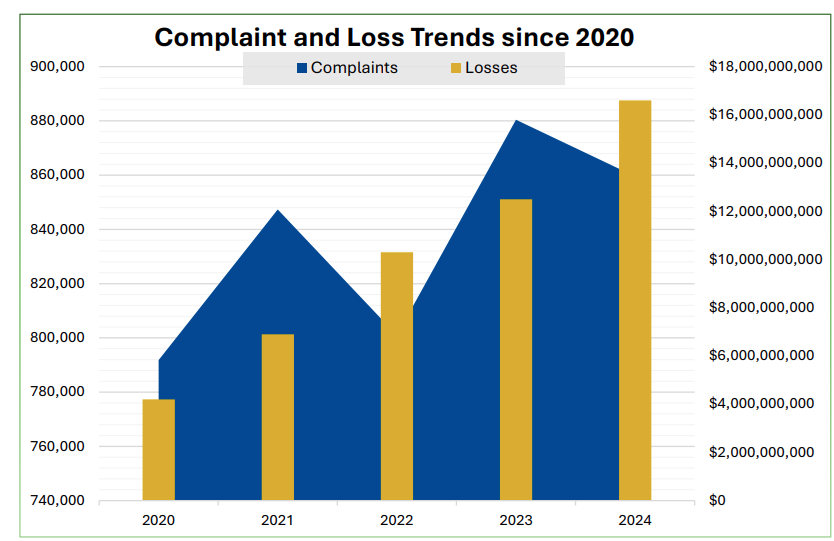
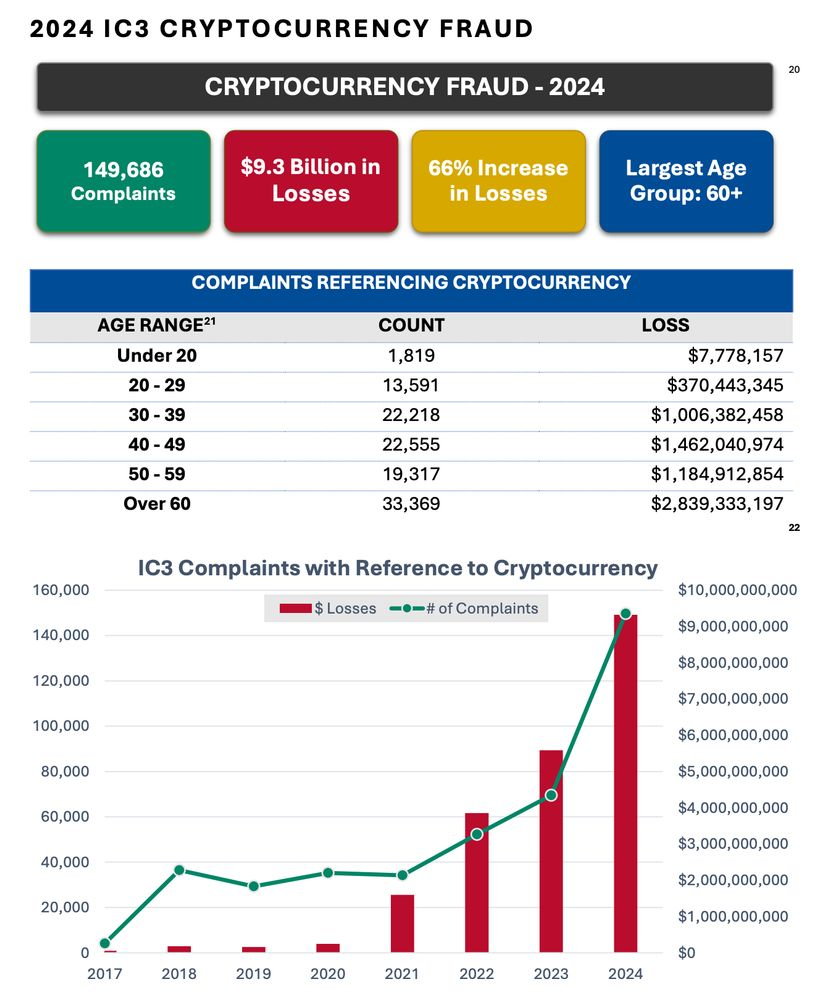
According to the FBI’s annual Internet Crime Complaint Center, online scammers stole a record $16.6 billion last year, up sharply from the $12.5 billion reported in 2023, reflecting the increased prevalence of online scams, particularly ones involving cryptocurrency and those targeting older Americans.
More than a quarter-million people reported actual financial loss from scams and cybercrime. Those numbers are likely an undercount, as they only reflect people who take the time to file a report with the agency. The agency received 859,532 total complaints of scams and cybercrime last year.
Fake toll scams, in which people frequently get text messages telling them to pay a small fee, prompted 58,271 complaints and $129,624 in reported losses.
The biggest scam victims were, by far, people aged 60 and older, who reported losing more than $4.8 billion. Older victims were also the most likely to say that cryptocurrency was involved in a scam that targeted them — complaints referencing cryptocurrency accounted for $2.8 billion among that age group.
People older than 60 lost the most money, $1.8 billion, in investment scams, a category that the FBI uses to include so-called “pig butchering” scams.
Money reported lost to investment scams has increased rapidly in recent years, rising from $3.3 billion in 2022 to $4.6 billion in 2023 and $6.6 billion the following year, according to the report. (Kevin Collier / NBC News)
Related: FBI.gov, The Record, BleepingComputer, Reuters, CBS News, Infosecurity, ABC News, Axios, UPI, Cyberscoop, New York Daily News, The420, The Register, VOI, Reuters
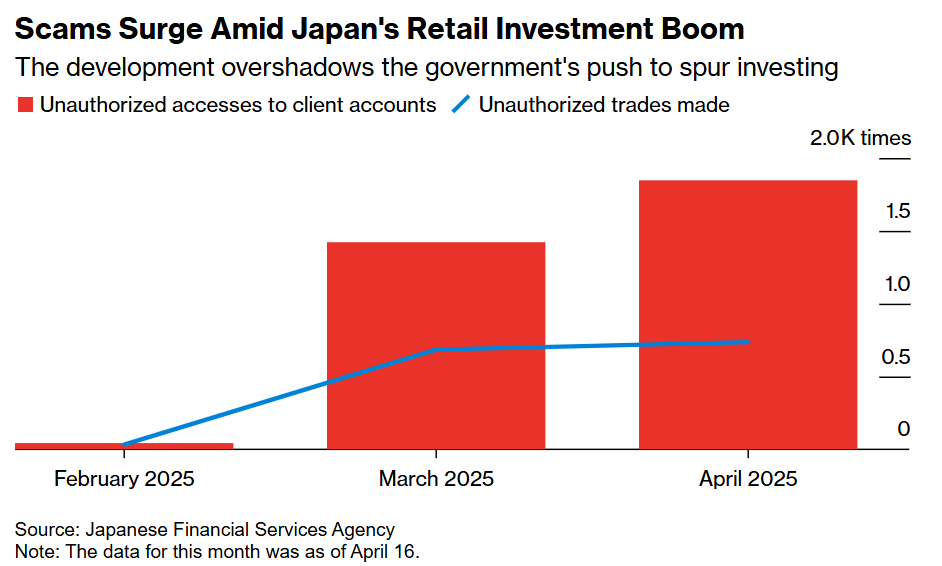
Criminals are hijacking online brokerage accounts in Japan and using them to manipulate penny stocks worldwide, with fraudulent trading reaching ¥100 billion ($710 million) since it started in February and shows no signs of cresting.
The scams typically use the hacked accounts to buy thinly traded stocks both domestically and overseas, allowing anyone who has built up a position earlier to cash out at inflated values. In response, some Japanese securities firms have stopped processing buy orders for certain Chinese, US, and Japanese stocks.
Eight of the country’s biggest brokers, including Rakuten Securities Inc. and SBI Securities Co., have reported unauthorized trading on their platforms. The breaches have exposed Japan as a potential weak point in efforts to safeguard global markets from hackers.
They also threaten to undermine the Japanese government’s push to get more people to invest for their retirement, particularly since some victims say they are baffled as to how their accounts were broken into, and the securities companies have so far largely refrained from covering the losses. (Aya Wagatsuma, Ryo Horiuchi, and Takashi Nakamichi / Bloomberg)
Related: Cryptopolitan, ChosunBiz, The Straits Times
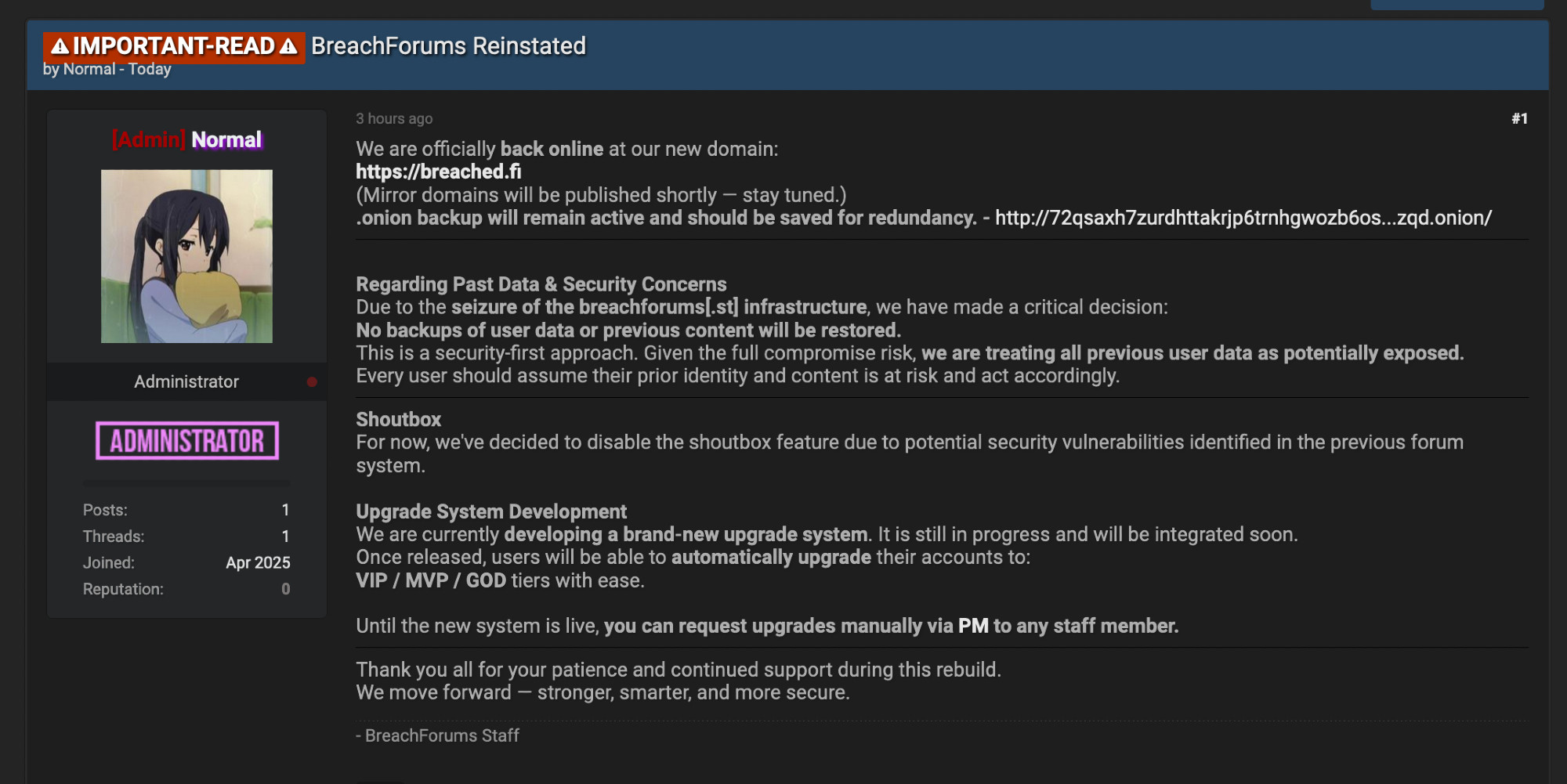
According to a new community post directed at its hundreds of thousands of users, along with an email, the infamous hacker marketplace BreachForums is set to rise from the dead for the third time, despite ongoing threats from the hacktivist group Dark Storm Team.
The pro-Palestinian hacktivist group posted about the April 16th Breached takeover on its Telegram channel, claiming to have carried out the distributed denial-of-service (DDoS) attack “for fun.”
The new owner of the BreachForums reboot announced its scheduled resurrection for this Thursday.
“Hello. The previous owner of BreachForums (Anastasia) has reinstated the forum!” they wrote in the email message sent via Proton, providing a link to its new home address and an official announcement.
The official statement was also posted on the BreachForums site. (Stefanie Schappert / Cybernews)
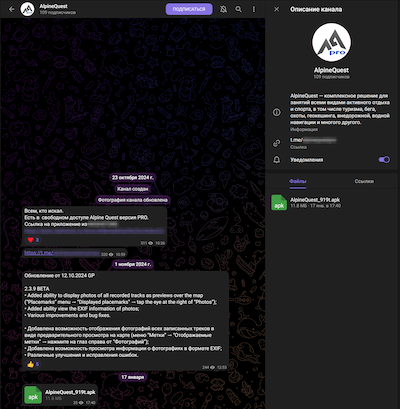
Researchers at Dr. Web discovered a new Android malware hidden inside trojanized versions of the Alpine Quest mapping app, which Russian soldiers reportedly use as part of war zone operational planning.
Attackers promote the trojanized app as a free, cracked version of the premium Alpine Quest Pro, using Telegram channels and Russian app catalogs for distribution.
AlpineQuest is a legitimate GPS and topographic mapping app for Android used by adventurers, athletes, search-and-rescue teams, and military personnel, valued for its offline capabilities and precision.
The app has two versions: a free Lite version with limited features and a paid Pro version that is free of tracking libraries, analytics, and advertisements.
The spyware hides inside a fully working Alpine Quest app, reducing suspicion and creating valuable data theft opportunities.
Once launched, it attempts to steal communication data and sensitive documents from the device, potentially revealing details about army operations. (Bill Toulas / Bleeping Computer)
Related: Dr. Web, The Register, HackRead
South Korea's Personal Information Protection Commission said that Chinese artificial intelligence startup DeepSeek transferred user information and prompts without permission when the service was still available for download in the country's app market.
The Commission stated that Hangzhou DeepSeek Artificial Intelligence did not obtain user consent when transferring personal information to several companies in China and the United States at the time of its launch in South Korea in January.
In February, South Korea's data agency suspended new downloads of the DeepSeek app in the country after it said DeepSeek acknowledged failing to take into account some of the agency's rules on protecting personal data.
The data protection agency said that DeepSeek also sent content in AI prompts entered by users to Beijing Volcano Engine Technology Co. Ltd., along with device, network, and app information. DeepSeek later told the agency that the decision to send information to Volcano Engine was to improve user experience and that it had blocked the transfer of AI prompt content from April 10. (Joyce Lee and Hyunsu Yim / Reuters)
Related: AFP, The Economic Times, Tech in Asia
Health insurance giant Blue Shield of California is notifying millions of people of a data breach, confirming that it had been sharing patients’ private health information with tech and advertising giant Google since 2021.
The insurer said that the data sharing stopped in January 2024, but it only learned this February that the years-long collection contained patients’ personal and sensitive health information.
Blue Shield said it used Google Analytics to track how its customers used its websites, but a misconfiguration had allowed for personal and health information to be collected as well, such as the search terms that patients used on its website to find healthcare providers.
The insurance giant said Google “may have used this data to conduct focused ad campaigns back to those individual members.”
Blue Shield said the collected data also included insurance plan names, types, and group numbers, along with personal information such as patients’ city, zip code, gender, and family size. Details of Blue Shield-assigned member account numbers, claim service dates, and service providers, patient names, and patients’ financial responsibility were also shared. (Zack Whittaker / TechCrunch)
Related: Blue California, Consumer Affairs, Bleeping Computer, San Francisco Chronicle, The Record, KRON4, Fierce Healthcare, Lifehacker, Tech Target
A man has been charged with hacking Australia’s largest online court-filing system, the New South Wales JusticeLink, although authorities believe he did not compromise any personal data.
The New South Wales JusticeLink allows lawyers, police, and businesses to upload sworn statements, identity information, and other files for the 400,000-plus court cases filed each year.
The state government revealed in March that an account had used automation to download more than 9,000 files before being booted from the system, with experts moving quickly to shut down the account.
“NSW police cybercrime squad detectives have laid charges about last month’s serious data breach involving the Department of Communities and Justice,” police minister, Yasmin Catley, said late on Wednesday.
A 38-year-old man was arrested in Maroubra in Sydney’s south-east, with officers seizing two laptops, police said.
He was charged with accessing or modifying restricted data held in a computer, as well as using a carriage service to cause harm. (Australian Associated Press)
Related: Information Age, Sydney Morning Herald, ABC.net.au, digwatch, Daily Mail, IT News

The ZKsync Association has confirmed the recovery of $5 million worth of stolen tokens from an April 15 ZKsync security incident involving its airdrop distribution contract.
The hacker agreed to accept a 10% bounty and return 90% of the remaining stolen tokens, transferring the ZKsync Security Council almost $5.7 million across three transfers on April 23.
“We’re pleased to share that the hacker has cooperated and returned the funds within the safe harbor deadline,” ZKsync Association posted to X on April 23, which was later reposted by ZKsync’s X account. (Brayden Lindrea / Cointelegraph)
Related: crypto.news, CoinDesk, Decrypt
Investigation into three code GitHub code repositories that a National Labor Relations Board (NLRB) whistleblower alleges that Elon Musk's DOGE team used to siphon gigabytes of data from the agency’s sensitive case files in early March reveals that one of those code bundles shows it is remarkably similar to a program published in January 2025 by Marko Elez, a 25-year-old DOGE employee who has worked at several of Musk’s companies.
According to a whistleblower complaint filed last week by Daniel J. Berulis, a 38-year-old security architect at the NLRB, officials from DOGE met with NLRB leaders on March 3 and demanded the creation of several all-powerful “tenant admin” accounts that were to be exempted from network logging activity that would otherwise keep a detailed record of all actions taken by those accounts.
Berulis said the new DOGE accounts had unrestricted permission to read, copy, and alter information contained in NLRB databases. The new accounts also could restrict log visibility, delay retention, route logs elsewhere, or even remove them entirely — top-tier user privileges that neither Berulis nor his boss possessed.
Berulis said he discovered one of the DOGE accounts had downloaded three external code libraries from GitHub that neither NLRB nor its contractors ever used. A “readme” file in one of the code bundles explained it was created to rotate connections through a large pool of cloud Internet addresses that serve “as a proxy to generate pseudo-infinite IPs for web scraping and brute forcing.” Brute force attacks involve automated login attempts that try many credential combinations in rapid sequence. (Brian Krebs / Krebs on Security)
Related: Hacker News (ycombinator)
Australia's SA Health says that personal data from more than 2,000 patients involved in sleep studies at Adelaide's Women's and Children's Hospital has been accessed in a ransomware attack.
SA Health said a third-party company known as Compumedics, which provides the sleep study software and equipment, had advised that the files of 2,254 patients who had used the inpatient sleep service at the hospital since 2018 were "likely to have been among those impacted."
SA Health chief executive officer Robyn Lawrence said the breach had "impacted Compumedics software directly and there is no evidence of a breach of any SA Health operated IT system." (ABC.net.au)
Related: News.com, Brisbane Times, The North West Star, The Northern Daily Leader, The Border Mail
According to Google Mandiant's latest M-Trends report, exploits were the most common initial infection vector in cyber incidents, representing one of every three attacks in 2024, and the four most frequently exploited vulnerabilities were all contained in edge devices, such as VPNs, firewalls, and routers.
These lightweight devices and services are designed to improve defenses and prevent intrusions. Yet, because they don’t typically support third-party software, including endpoint detection and response capabilities, organizations are often caught off guard when attackers gain access to their networks through a highly privileged system.
“Three of the four vulnerabilities were first exploited as zero-days,” Mandiant said. “While a broad selection of threat actors have recently targeted edge devices, Mandiant also specifically noted an increase in targeting from Russian and Chinese cyber espionage actors.”
A command injection vulnerability in the GlobalProtect feature of Palo Alto Networks’ PAN-OS, CVE-2024-3400, was the most frequently exploited defect across all of Mandiant’s incident response engagements last year. Mandiant said it observed one threat group exploit it as a zero-day, but malicious activities quickly escalated soon after. (Matt Kapko / Cyberscoop)
Related: Mandiant, GBHackers, Digit, The Register, Cyber Daily
The US Department of Health and Human Services (HHS) announced that Whittier, Calif.-based PIH Health, with three California hospitals serving Los Angeles and Orange Counties, has agreed to pay federal regulators $600,000 and implement a corrective action plan to resolve potential HIPAA violations identified during an investigation into a 2019 breach triggered by a phishing attack.
HHS said the resolution agreement with Whittier, Calif.-based PIH Health comes in the wake of the federal agency's investigation into a breach report PIH Health filed in January 2020 - seven months after a June 2019 phishing attack compromised 45 employee email accounts.
Under HIPAA, protected health information breaches affecting 500 or more individuals must be reported to HHS OCR within 60 days of discovery. Affected individuals and the media also must be notified of HIPAA breaches within 60 days of discovery.
The PIH Health phishing incident affected the electronic PHI of nearly 190,000 people, including names, addresses, date of birth, Social Security numbers, driver's license numbers, diagnoses, lab results, medications, treatment, claims information, and financial information. (Marianne Kolbasuk McGee / Bank Info Security)
In its latest Secure Future Initiative Progress Report, Microsoft said it had increased employee usage of multifactor authentication, standardized secure development pipelines, and adopted new security processes as part of its ongoing efforts to rebuild its security culture.
Moreover, tens of thousands of employees have taken part in security trainings, and "all 14 Deputy CISOs have completed a risk inventory and prioritization for their product or function."
Initially announced in November 2023 to "bring together every part of Microsoft to advance cybersecurity protection," Microsoft revamped the Secure Future Initiative with a much more ambitious "security above all else" plan last spring.
The change came after the US Department of Homeland Security's Cyber Safety Review Board (CSRB) criticized the tech giant's security culture as "inadequate" and one needing an overhaul. Specifically, the CSRB reviewed Microsoft's July 2023 response to a breach in which a Chinese nation-state threat actor accessed email accounts at 22 organizations, including a number of US federal agencies. The threat actor, tracked as Storm-0558, stole a Microsoft account (MSA) signing key and forged authentication tokens. (Alexander Culafi / Dark Reading)
Related: Microsoft
In a bid to promote international alignment of cyber defenses, including reciprocity agreements, over fifty CISOs from leading global companies, including Microsoft, signed a letter emphasizing the urgency to take such action.
The CISO letter highlights key challenges created by the current regulatory landscape, including incident response and crisis management complexities during cyberattacks and delays in coordinating defense efforts. The increasing divergence among regulations across different jurisdictions also limits the ability of governments and private sector entities to share threat intelligence efficiently, weakening collective cyber resilience.
The CISO community calls on governments to encourage high-level commitments from global policymakers to enhance regulatory alignment and promote a balanced approach to cybersecurity regulations. It also asks governments to facilitate international dialogue among regulators through established global platforms, including the OECD, ensuring diverse stakeholder participation.
Finally, it asks governments to explore mutual recognition agreements and other mechanisms that streamline compliance while raising the global cybersecurity baseline. (Bret Arsenault, Amy Hogan-Burney / Microsoft)
Related: CISO Letter, CSO Online
Sources say Defense Secretary Pete Hegseth directed the installation of Signal, a commercially available messaging app, on a desktop computer in his Pentagon office, illustrating the extent to which he has integrated use of the unclassified communications platform at the center of his political troubles with the highly secure systems the US government relies on to safeguard military plans and other sensitive information.
Hegseth effectively “cloned” the Signal app on his personal cellphone following a discussion among Hegseth and his aides about how they could circumvent the lack of cellphone service in much of the Pentagon and more quickly coordinate with the White House and other top Trump officials using the encrypted app.
Other aides, including Joe Kasper, Hegseth’s chief of staff at the time, also voiced interest in using Signal on Pentagon computers, but it is unclear how widely the app’s use proliferated. It’s also unclear whether Hegseth and his team of political advisers have adhered to U.S. law that would require them to preserve such messages. (Dan Lamothe / Washington Post)
Related: New York Times, The Daily Beast
The State Department’s Bureau of Cyberspace and Digital Policy was moved under the agency’s Economic Growth office following a massive reorganization announced by Secretary of State Marco Rubio.
CDP, which has operated under the Deputy Secretary’s office since being established in 2022, has spearheaded dozens of overseas engagements focused on bringing U.S. diplomacy into the digital age and has played a prime role in calling out Chinese officials on Beijing’s hacking pursuits against American critical infrastructure.
The office, which former cybersecurity executive Nate Fick led until he left his politically appointed post in January, has also worked frequently on counter-spyware pacts with other nations, an effort persisting even as recently as this month. Jennifer Bachus has been leading CDP in an acting capacity since Fick departed. (David DiMolfetta / NextGov/FCW)
Related: DefenseOne, ExecutiveGov, FedScoop
Application security company Endor Labs announced it had raised $93 million in a Series B venture funding round.
DFJ Growth led the round with participation from Salesforce Ventures and existing backers including Lightspeed Venture Partners, Coatue, Dell Technologies Capital, Section 32, and Citi Ventures. (Kyle Wiggers / TechCrunch)
Related: FinSMEs, Developer Tech News, DevOps.com, Endor Labs
Virtual CISO startup Cynomi announced it had raised $37M in a Series B venture funding round.
Insight Partners and Entrée Capital led the round with participation from existing investors Canaan, Flint Capital, and S16VC. (Ingrid Lunden / TechCrunch)
Related: FinSMEs, SiliconANGLE, Cynomi
Best Thing of the Day: The Surprising Thing Is They're All Correct
In his blog, HaveIBeenPwned owner Troy Hunt walks through the many ways of referring to credentialed system access, including "log in," "login," "logon," "log on," "sign in," and "sign on."
Worst Thing of the Day: We Must Track You Even If You're Playing Solitaire
UK privacy advocate noyb is suing French video game developer and publisher Ubisoft for forcing its customers to connect to the internet every time they launch a single-player game.
Closing Thought