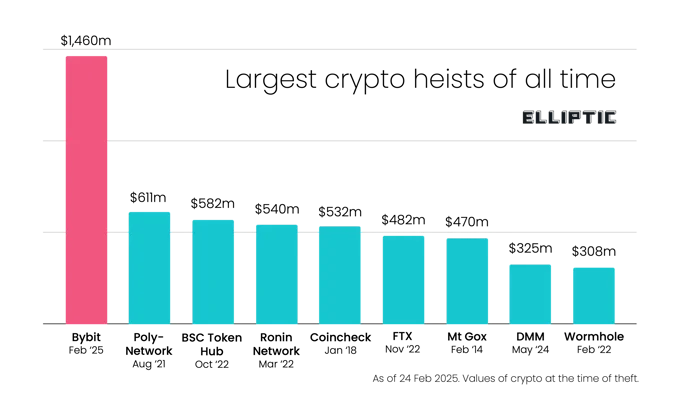
DPRK's Lazarus Group swiped $1.5 billion from crypto exchange Bybit
Apple strips encrypted security from UK cloud users after gov't edict, Hackers are targeting Signal, CISA stops election security work, DOGE workers are now CISA staff, Hacker pleads guilty to telco phone records theft, Pegasus infections more rampant than expected, much more