DPRK spies launched two US businesses to spread malware among crypto workers
DPRK hackers used Russian internet infrastructure, Lazarus Group targeted multiple businesses in Operation SyncHole, DPRK workers use genAI for US and European jobs, Scattered Spider member extradited to US, Antitrust probe launched into TP-Link, FBI tracks down Nigerian sextortionists, much more
Metacurity is a reader-supported publication that requires significant work and non-trivial expenses. We rely on the generous support of our paid readers. Please consider upgrading your subscription to support Metacurity's ongoing work. Thank you.
If you're unable to commit to a subscription today, please consider donating whatever you can. Thank you!
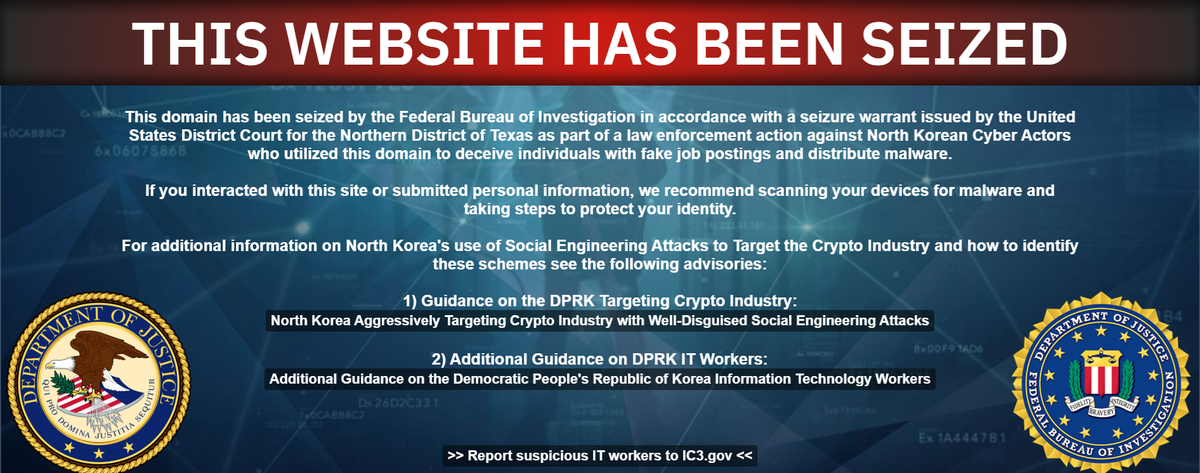
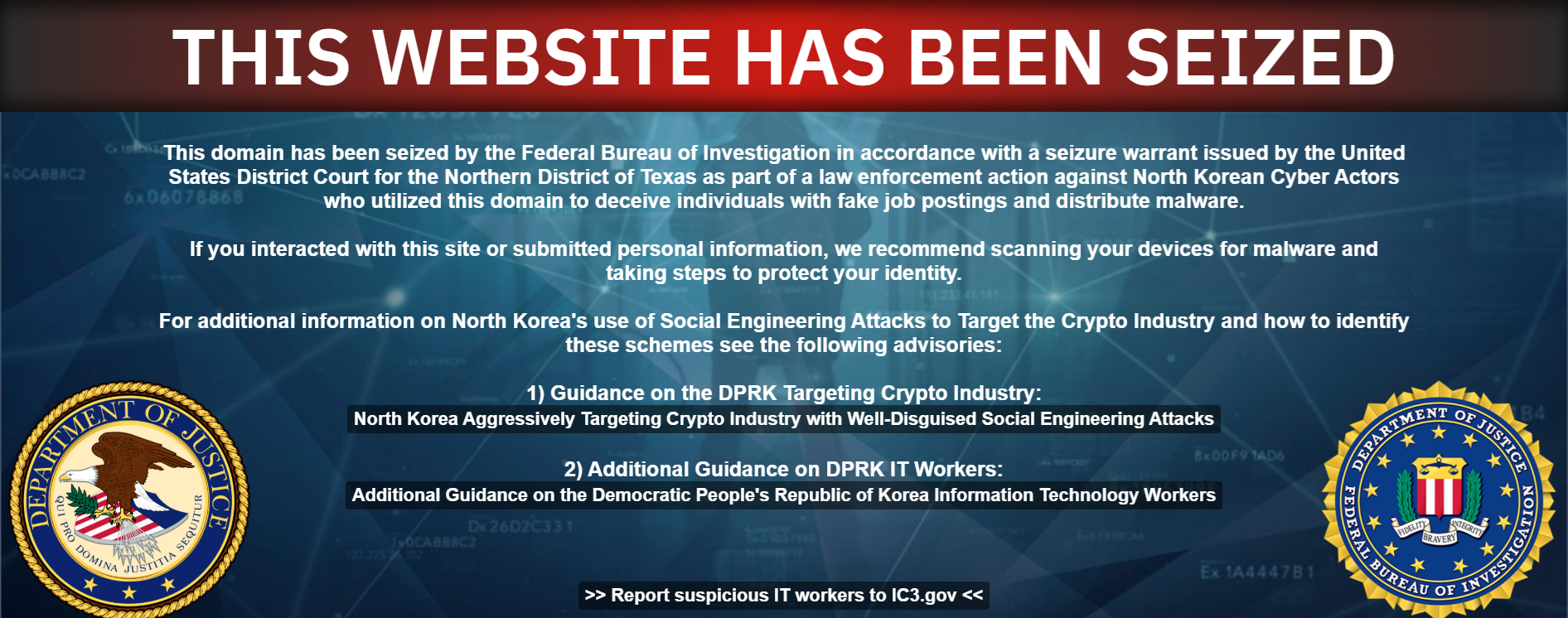
Researchers at Silent Push report that North Korean cyber spies created two businesses in the US, Blocknovas LLC and Softglide LLC, in violation of Treasury sanctions, to infect developers working in the cryptocurrency industry with malicious software.
The businesses were set up in the states of New Mexico and New York using fake personas and addresses. A third business, Angeloper Agency, is linked to the campaign, but does not appear to be registered in the United States.
Blocknovas' registration listed a physical address in Warrenville, South Carolina, that appears on Google Maps to be an empty lot. Softglide seems to have been registered by a small tax office in Buffalo, New York.
The hackers are part of a subgroup within the Lazarus Group, an elite team of North Korean hackers that is part of the Reconnaissance General Bureau, Pyongyang’s main foreign intelligence agency, Silent Push said.
The FBI declined to comment specifically on Blocknovas or Softglide. But an FBI seizure notice posted to the website for Blocknovas said the domain was seized “as part of a law enforcement action against North Korean Cyber Actors who utilized this domain to deceive individuals with fake job postings and distribute malware.”
The FBI said it continues “to focus on imposing risks and consequences, not only on the DPRK actors themselves, but anybody who is facilitating their ability to conduct these schemes.”One FBI official said North Korean cyber operations are “perhaps one of the most advanced persistent threats” facing the United States. (AJ Vicens and James Pearson / Reuters)
Related: Silent Push, CoinDesk, Times of India
Researchers at Trend Micro report that North Korean hackers look north toward Russia for the internet infrastructure behind the many online scams that Pyongyang has built to funnel stolen cash into the rogue nation, which they tie to a group called Void Dokkaebi that used Block Novas as a Front Company.
The company traced cybercrime activities aligned with North Korea to IP addresses assigned to an organization in the Russian city of Khabarovsk, which has cultivated ties with North Korea since the demise of the Soviet Union. It also traced activity to Khasan, a hamlet just across the Russian border from the Hermit Kingdom that's the site of the "Korea–Russia Friendship Bridge." A prominent Russian telecommunications firm laid a fiber-optic cable across the bridge in 2017.
Hackers behind campaigns related to the Void Dokkaebi intrusion set, also known as Famous Chollima, use Russian IP address ranges cloaked by a VPN, a proxy, or a remote desktop protocol session to evade detection and attribution. Five Russian IP ranges serve as the backbone of campaigns that include social engineering, malware deployment, and crypto wallet cracking.
Void Dokkaebi used a front company called BlockNovas, complete with a slick website and presence on platforms like LinkedIn and Upwork, to lure developers into fake job interviews. Victims are tricked into downloading malware "BeaverTail" by Palo Alto Networks, a JavaScript-based backdoor hidden inside node package manager packages.
Trend Micro researchers linked BlockNovas to known Beavertail infrastructure and discovered that the company advertised for a senior software engineer role targeting Ukrainian professionals as recently as December 2024. Investigators found that malware-laced tasks distributed during interviews injected obfuscated scripts that compromised victims' systems. (Prajeet Nair / BankInfoSecurity)
Related: Trend Micro, NK Pro
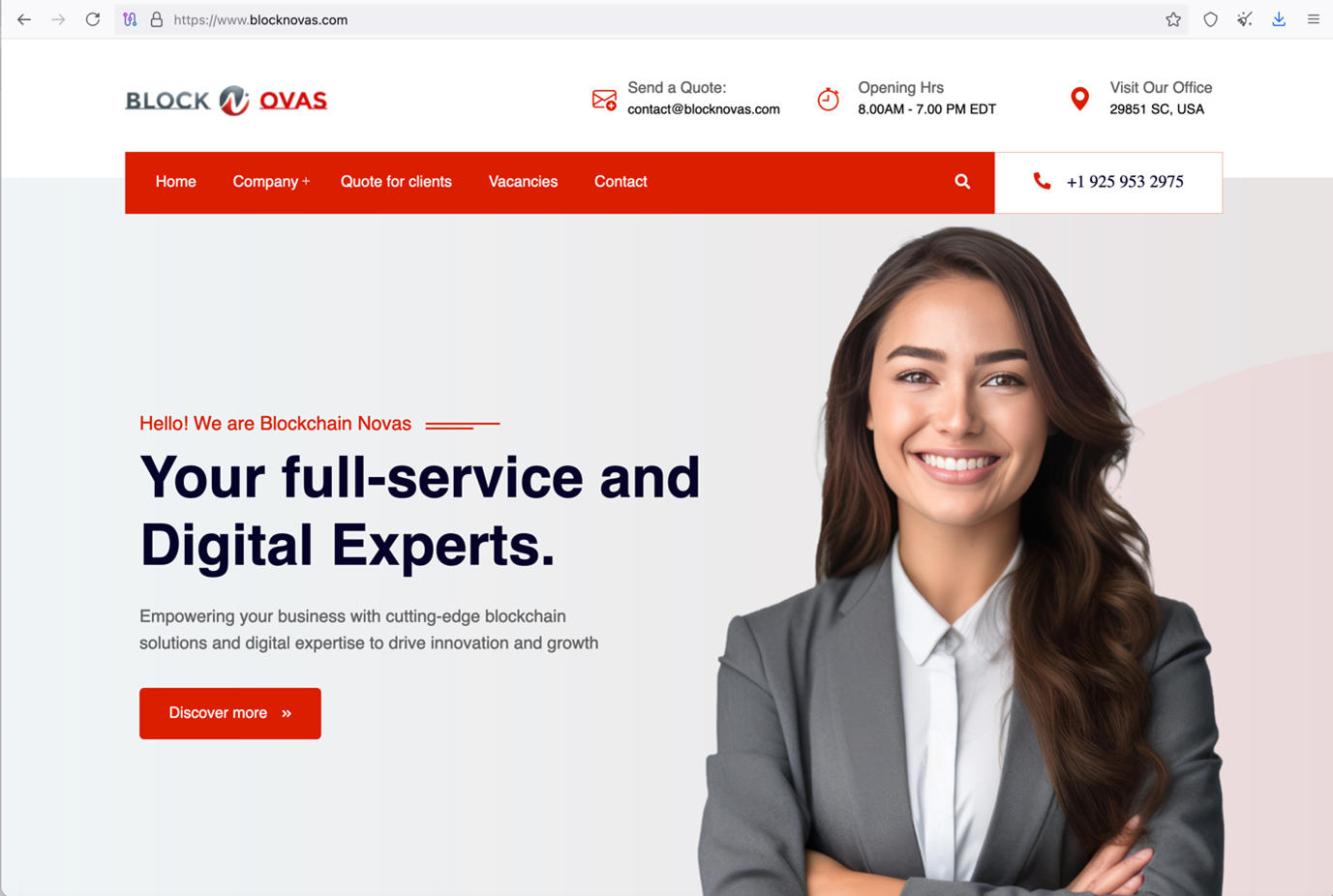
According to Kaspersky researchers, in a recent espionage campaign they call Operation SyncHole, the infamous North Korean threat group Lazarus targeted multiple organizations in the software, IT, finance, and telecommunications sectors in South Korea.
The operation combined a watering hole attack strategy with an exploit for a vulnerability in a file transfer client that is required in South Korea to complete certain financial and administrative tasks.
“We identified at least six software, IT, financial, semiconductor manufacturing, and telecommunication organizations in South Korea that fell victim to 'Operation SyncHole,” Kaspersky said, adding that they believed there were many more operations affected across a wide range of industries.
The attack started with targets visiting legitimate South Korean media portals that Lazarus had compromised with server-side scripts for profiling visitors and redirecting valid targets to malicious domains.
Victims were redirected to sites that mimic software vendors, such as the distributor of Cross EX. This tool enables South Koreans to use security software in various web browsers for online banking and interactions with government websites.
Kaspersky observed multiple infection chains across the six confirmed victims, which differ in earlier and later phases of the attack, with the initial infection being the common ground.
Based on the tooling used in Operation SyncHole attacks, Kaspersky was able to confidently attribute the compromises to the Lazarus hacker group backed by the North Korean government.
Additional clues pointing to the threat actor were the working hours/apparent timezone along with techniques, tactics, and procedures (TTPs) specific to Lazarus. (Bill Toulas / Bleeping Computer)
Related: Kaspersky
Researchers at Okta report that North Korean IT workers illicitly gaining employment at US and European tech companies are increasingly using generative artificial intelligence in a variety of ways to assist them throughout the job application and interview process.
Okta researchers observed the use of multiple AI-enhanced services used to manage the email and phone communications of multiple personas; translate and transcribe communications; generate resumes and cover letters; conduct mock job interviews; test and improve job applications; and more.
“Facilitators extensively employ AI-enhanced tools to help minimally skilled, non-native English-speaking workers maintain software engineering positions, allowing them to channel earnings towards the sanctioned DPRK regime,” Okta said.
“The scale of observed operations suggests that even short-term employment for a few weeks or months at a time, when scaled with automation and GenAI, can present a viable economic opportunity for the DPRK.” (Jonathan Greig / The Record)
Tyler Buchanan, a 23-year-old from Scotland and an alleged member of the notorious Scattered Spider cybercrime group, was extradited from Spain to the US.
Buchanan was arrested last year over his alleged involvement in the theft of sensitive data about American consumers and tens of millions of dollars worth of cryptocurrency.
Buchanan, who was charged with conspiracy to commit wire fraud, conspiracy, wire fraud, and aggravated identity theft, was detained in California after a court appearance, said the official.
Buchanan and four co-defendants are accused of fooling employees at numerous companies, including four major US telecommunication providers and one US cryptocurrency company, into sharing their login credentials. That allowed the hackers to break into corporate systems, with the ultimate goal of stealing cryptocurrency from their customers.
The hackers allegedly stole data about customers or accessed phone providers’ tools that helped them intercept text messages or calls. Then, they would target specific customers with phishing links in an attempt to breach cryptocurrency or financial accounts, according to the indictment. (Margi Murphy / Bloomberg)
Related: Reuters
Sources say the US is conducting a criminal antitrust investigation into pricing strategies by TP-Link Systems Inc., a California-based router maker with links to China, whose equipment now dominates the American market.
Prosecutors in the Justice Department’s antitrust division are investigating whether TP-Link engaged in predatory pricing, according to the people. Such a pricing strategy involves selling goods below cost in order to gain market share before raising prices once competitors have either been hobbled or eliminated.
Beyond pricing, a focus of the inquiry is also whether the company’s growing US market share represents a threat to national security. The scrutiny began in late 2024 under the Biden administration and has continued under President Donald Trump. (Josh Sisco and Kate O'Keeffe / Bloomberg)
Related: Reuters
The FBI is sending agents to Nigeria to help track down sextortion scammers in "Operation Artemis," which has already led to the arrest of 22 Nigerians, half of whom are “directly linked” to sextortion incidents in which victims died by suicide.
The FBI noted it’s been “observing a significant increase over the last three years in financially motivated sextortion schemes targeting young males ages 14-17, resulting in more than 20 minor victims dying by suicide.”
The agency is also facing a 30% year-over-year increase in sextortion-related tips. “According to the FBI’s Internet Crime Complaint Center or IC3, there were over 54,000 [extortion-related] victims in 2024, up from 34,000 in 2023,” it says. “Over the last two years there have been nearly $65 million in financial losses due to this crime.”
In response, the FBI says 55 agency field offices came together to identify “nearly 3,000 victims of financially motivated sextortion,” which led investigators to track down the culprits in Nigeria. The US has since extradited at least three suspects from Nigeria. (Michael Kan / PC Mag)

US efforts to help Ukraine protect itself against Russian cyberattacks have been curtailed amid wide-ranging disruption by the Trump administration, raising concerns about the erosion of vital defenses against Kremlin-backed hackers.
According to sources, dozens of people located in Ukraine and the US, who had provided technical assistance on cybersecurity at hundreds of facilities across the war-torn country, have had their contracts cancelled or paused.
Moreover, planned shipments of computer hardware and software intended to keep Ukraine’s infrastructure secure haven’t been delivered.
In the last five years or so, the US Agency for International Development alone has committed more than $200 million for cybersecurity aid to Ukraine. The National Security Agency and US Cyber Command have also provided assistance.
That aid has been viewed as critical to helping the country prevent and recover from cyberattacks on government officials, telecommunications companies, and energy providers amid the conflict.
However, USAID has been gutted in the first months of Trump’s presidency by Elon Musk’s Department of Government Efficiency, and Trump has become increasingly impatient with Zelenskiy. This week, Vice President JD Vance warned the US could walk away from the peace process if Russia and Ukraine don’t accept the proposal, potentially complicating any future cybersecurity assistance. (Ryan Gallagher / Bloomberg)
Related: CSO Online
The US Justice Department announced that Michael Scheuer has been sentenced to three years in federal prison, ordered to forfeit his computer, and pay $687,776.50 in restitution for hacking into the Walt Disney World food menu production manager to indicate that food items were safe for customers with certain allergies when they were not.
Prosecutors say he also altered menu information related to wine regions to reflect locations of recent mass shootings.
He also launched denial-of-service attacks designed to lock certain company employees out of their accounts. (Jonathan Grass / WFTV News)
Related: United States Attorneys Office, Orlando Sentinel, WKMG, WHIO, Databreaches.net
Acting Pentagon Chief Information Officer Katie Arrington said that a new fast-track approval process for software on Defense Department networks will use AI tools to shorten a process that currently takes months or years radically.
Arrington said new Software Fast Track (SWIFT) process will use “AI tools on the back end” to replace the Authorization To Operate (ATO) process, which governs the way software products are certified for use on military networks, and the venerable Risk Management Framework (RMF), which has guided decisions about cybersecurity in DOD for more than a decade.
“I’m blowing up the RMF, blowing up the ATOs. They’re stupid. They’re archaic,” she said, lambasting the extensive paper-based documentation ATOs require.
Instead, SWIFT will collect third-party data about the cybersecurity of vendors and technical information about the makeup of their software, through a government web application called eMASS, and keep it in the Supplier Performance Risk System (SPRS), a database where contractor performance and cybersecurity compliance information is stored. (Shaun Waterman / Air and Space Forces Magazine)
Related: r/NISTcontrols
Three European funding agencies, the German Research Foundation, Swedish Research Council, and Swiss National Science Foundation, said they had suspended funding for projects with the National Natural Science Foundation of China (NSFC) since 2021, when China's Data Security Law took effect.
The funding agencies said they would not jointly fund new research projects with the NSFC due to concerns over access to data, potential conflict with local data law, or legal liabilities for themselves or research institutes for breaches of the law's vaguely defined provisions.
The suspension highlights the widening impact of a Chinese data protection law that has already impeded some business projects, as international institutions and companies assess how to navigate the regulations. (Andrew Silver / Reuters)
Related: Times of India
Yale New Haven Health (YNHHS), the largest nonprofit healthcare network in Connecticut, is warning that threat actors stole the personal data of 5.5 million patients in a cyberattack earlier this month.
On March 11, 2025, the organization first reported that it was dealing with a cybersecurity incident that occurred three days earlier. This incident caused IT system disruptions but did not impact patient care.
Yale New Haven Health hired Mandiant to help with system restoration and forensic investigation while federal authorities were notified about the incident. (Bill Toulas / Bleeping Computer)
Related: Modern Healthcare, Teiss, WTNH, Yale News, The Register, Security Week, CT Insider
A critical 10.0 bug in the Commvault Command Center, CVE-2025-34028, could potentially let remote attackers execute arbitrary code without authentication.
The company disclosed in a recent advisory that the vulnerability could lead to a complete compromise of the Command Center, which enterprises use on help desks or to perform common administrative tasks, such as restoring user emails.
The vulnerability has been resolved and impacts only the 11.38 Innovation release, and other installations within the same system are not affected.
Organizations are urged to follow mitigation steps in an immediate and persistent mode, and if they cannot shut down full networks, they should use appliance-based microsegmentation systems that can opt in to critical infrastructure isolation in minutes. (Steve Zurier / SC Media)
Related: Commvault, Dark Reading, Techzine, Help Net Security, The Cyber Express, Infosecurity Magazine, Cybersecurity Agency of Singapore
Researchers at Toshiba and their colleagues reveal that quantum communications are possible across more than 250 kilometers using existing commercial telecommunication infrastructure.
Quantum networks can transmit encrypted messages that are theoretically impossible to eavesdrop on. They rely on the fact that measuring a quantum system—for instance, scanning a light pulse to see what data it might hold—disturbs the signal’s overall properties.
Scientists have often assumed that making quantum networks a reality would likely involve expensive equipment such as cryogenic coolers. Now, the new system “suggests that quantum networks could become much more scalable and practical in the near term,” says Pittaluga, who is currently quantum lead at Wave Photonics in Cambridge, England.
In the new study, the researchers developed a quantum communications network using 254 kilometers of existing commercial optical fiber in Germany. This system linked telecom data centers at Frankfurt and Kehl, with a relay node in Kirchfeld. (Charles Choi / IEEE Spectrum)
Related: Financial Times, The Quantum Insider, Nature, The Brighter Side of News, Phys.org, Slashdot
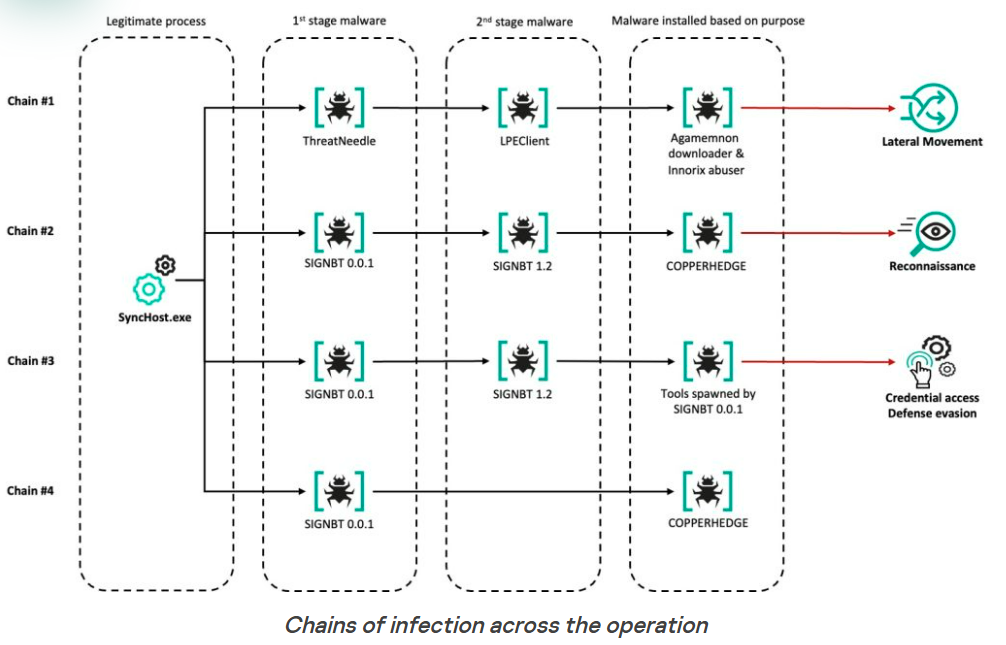
Researchers at Volexity report that Russian threat actors have been abusing legitimate OAuth 2.0 authentication workflows to hijack Microsoft 365 accounts of employees of organizations related to Ukraine and human rights.
The hackers are impersonating officials from European countries and contacting targets through WhatsApp and Signal messaging platforms. The purpose is to convince potential victims to provide Microsoft authorization codes that give access to accounts, or to click on malicious links that collect logins and one-time access codes.
The researchers describe the attack as starting with a message over Signal or WhatsApp. Volexity notes that in one case, the communication came from a compromised Ukrainian government account.
Once the communication channel is established, the attacker sends an OAuth phishing URL under the pretext that it is required for joining the video call.
To protect against such attacks, Volexity advises setting up alerts on logins using the Visual Studio Code client_id, block access to ‘insiders.vscode.dev’ and ‘vscode-redirect.azurewebsites.net’.
The researchers also recommend setting up conditional access policies to limit access to approved devices only. (Bill Toulas / Bleeping Computer)
Related: Volexity, GBHackers, Techzine, Windows Report
More than a year after a cyberattack on the government of Long Beach, California, the city is informing residents that information on nearly half a million people was leaked.
In breach notification documents filed in multiple states, the city said 470,060 people had sensitive data accessed by hackers who breached government systems during a cyberattack in November 2023.
The city said it conducted an “extensive” forensic investigation and “manual document review” that lasted until March 18, 2025. The information stolen includes Social Security numbers, financial account information, credit and debit card numbers, biometric information, medical data, driver’s license numbers, passports, tax data, and more. (Jonathan Greig / The Record)
Related: Long Beach Post, GovTech, Long Beach Local News
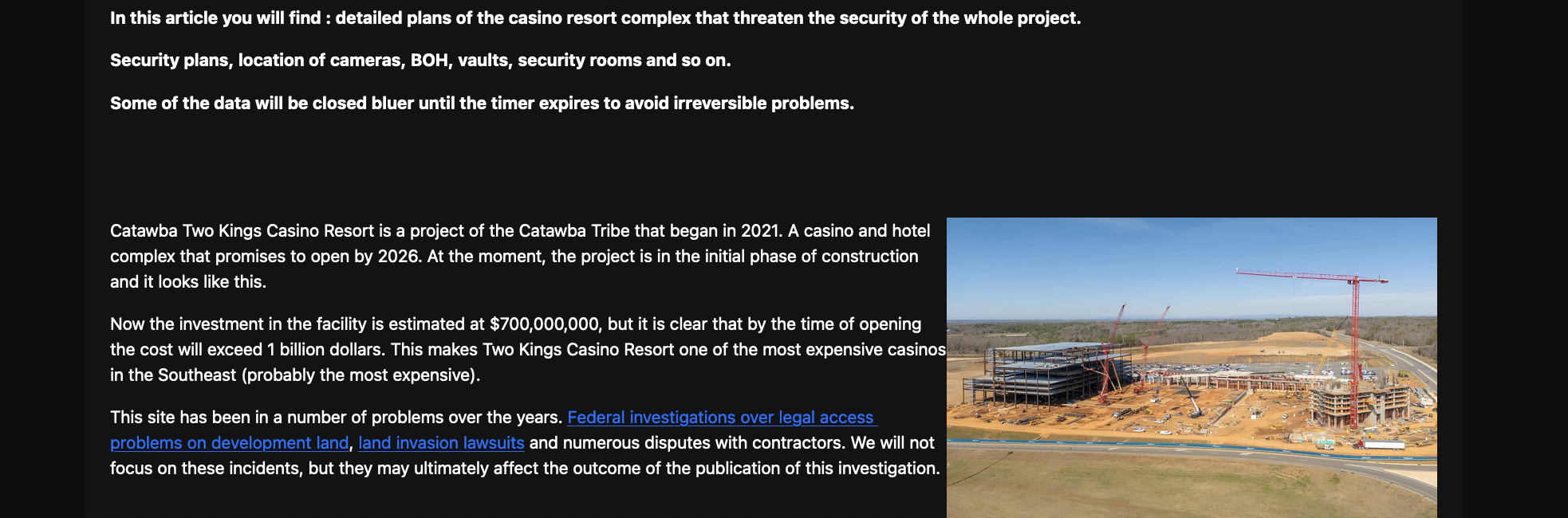
Ransomware gang Anubis claims that it’s holding hostage the blueprints to the Catawba Two Kings Casino Resort, a tribal project being built in Kings Mountain, North Carolina.
If true, they may know more about the vaults, server rooms, and security cameras than the people building it.
The hackers posted a ransom threat on their dark web leak site, claiming they have a “terribly detailed archive” including blueprints of the casino’s main floor, parking, hotel tower, and even restricted back-of-house zones.
The ransom note went live on April 23rd, with the timer on the leak site showing that the company has 19 hours until the data is publicly released. Ransomware gangs often use this tactic to force companies into paying up. Anubis's post on X suggests the gang might have held the data since late February.
If true, the hack is a potential security nightmare. Anubis says they’ve got layouts of server rooms, chip vaults, the locations of doors with restricted access, surveillance camera placements, staff interrogation rooms, and evacuation routes. All in all, the leaked data is a complete casino heist toolkit. (Paulina Okunytė / Cybernews)
Related: The Herald
Some investors' trading accounts have been hacked and used for unauthorised share buying on Bursa Malaysia.
Bursa confirmed that it has, together with the Securities Commission Malaysia, been informed by several brokers about the detection of unauthorised access and trading activities in certain online trading accounts.
“The extent of the incident is being ascertained. Capital market regulators and the brokers are working closely on the matter," Bursa Malaysia said.
According to one source, the hacking primarily originated from overseas, as indicated by the associated internet protocol (IP) addresses.
The compromised accounts were reportedly those without pre-authorised internet trading access, meaning transactions for these accounts typically require execution through their respective brokerage firms.
The source also suggested that the breach predominantly occurred at the brokerage firms' systems, rather than through individual investors' login credentials. (John Lai / The Edge)
Related: SAYS, Lowyat.net, The Edge Malaysia, The Star, Free Malaysia Today, NST Online, Dayak Daily
Sources say Defense Secretary Pete Hegseth had an internet connection that bypassed the Pentagon’s security protocols set up in his office to use the Signal messaging app on a personal computer, raising yet again the possibility that sensitive defense information could have been put at risk of potential hacking or surveillance.
Known as a “dirty” internet line by the IT industry, it connects directly to the public internet, where the user’s information and the websites accessed do not have the same security filters or protocols that the Pentagon’s secured connections maintain.
Other Pentagon offices have used them, particularly if there’s a need to monitor information or websites that would otherwise be blocked. (Tara Copp / Associated Press)
Related: ABC News
Madhu Gottumukkala has been named deputy director of the Cybersecurity and Infrastructure Security Agency from his position in the South Dakota government, working for DHS Secretary Kristi Noem.
Gottumukkala had been commissioner of the Bureau of Information and Telecommunication (BIT) and state chief information officer.
He’ll leave BIT on May 16. A CISA spokesperson confirmed that Gottumukkala would become deputy director of the agency. (Tim Starks / Cyberscoop)
Related: South Dakota Public Broadcasting, South Dakota Searchlight, South Dakota State News
Ballistic Ventures, the venture capital firm focused on funding and incubating entrepreneurs and innovations in cybersecurity, announced that Phil Venables, the renowned cybersecurity leader and former Chief Information Security Officer (CISO) of Google Cloud, has joined the firm as a Venture Partner.
Venables' career spans leadership roles at Google Cloud, Goldman Sachs, and Deutsche Bank. He has played a pivotal role in shaping the cybersecurity landscape.
He also has deep experience in both the private and public sectors, including serving on the President’s Council of Advisors on Science and Technology (PCAST). (Ballistic Ventures)
Related: Wall Street Journal
AI threat detection company Scamnetic announced it had raised $13 million in a Series A venture funding round.
Roo Capital led the round with participation from 1st and Main Growth Partners, SaaS Ventures, and Riptide Ventures. (Duncan Riley / Silicon Angle)
Related: Security Week, The Business Journals, AIThority, FinSMes
Best Thing of the Day: Maybe the Dems Aren't as Inert as They Seem
Over fifty Democratic lawmakers have signed a letter demanding answers from senior US government officials on how Elon Musk's DOGE workers may have removed sensitive labor data and exposed NLRB systems to being compromised.
Worst Thing of the Day: Attackers Scurry to Jump on Vulnerabilities
Researchers at VulnCheck say that attackers exploited nearly a third of vulnerabilities within a day of CVE disclosure in the first quarter of 2025.
Closing Thought