Prosecutors say 'computer whiz' NFL, Michigan football coach hacked thousands of athletes for intimate photos, videos
N. Korea establishes a new hacking group, Dutch parliament criminalizes foreign influence-related espionage, Sophisticated phishing attack mounted against Mac users, Google sues scammers behind fake Google Maps listings, Signal will leave France if encryption backdoor law is passed, much more


Metacurity is a reader-supported publication that requires a lot of work and relies on the generous support of our paid readers. Please consider supporting Metacurity with an upgraded subscription. Thank you.
If you can't commit to a subscription today, please consider donating whatever you can. Thank you!
Federal prosecutors indicted former NFL and University of Michigan assistant football coach Matt Weiss for hacking into the computer accounts of thousands of college athletes seeking intimate photos and videos.
Weiss, who worked for the Baltimore Ravens before joining Michigan’s staff in 2021, was charged with 14 counts of unauthorized computer access and 10 counts of identity theft.
The indictment states that from 2015 to 2023, Weiss gained access to the databases of more than 100 colleges and universities maintained by a third-party vendor, Keffer Development Services, and downloaded personal information and medical data of more than 150,000 athletes.
Prosecutors portrayed him as a computer whiz, saying Weiss “cracked the encryption protecting the passwords, assisted by research that he did on the internet.”
According to the indictment, he then gained access to the social media, email, and cloud storage accounts of more than 2,000 athletes and over 1,300 students or alums from schools nationwide.
“Weiss primarily targeted female college athletes,” the indictment said. “He researched and targeted these women based on their school affiliation, athletic history, and physical characteristics. He aimed to obtain private photographs and videos that were never intended to be shared beyond intimate partners.”
Weiss kept notes on photos and videos that he downloaded, commenting on the bodies and sexual preferences and sometimes returning years later to look for new images, the indictment said. (Ed White / Associated Press)
Related: Justice Department, TMZ, Baltimore Sun, ESPN, ABC7, Mlive, The Record, CBS News, Detroit Free Press, The Athletic, People, Detroit News, NBC News
Daily NK, a news outlet that focuses on North Korea, reported that the North Korean government is reportedly establishing a new hacking group within the intelligence agency Reconnaissance General Bureau (RGB) called Research Center 227, which will focus on research to develop “offensive hacking technologies and programs,” citing a source inside the regime.
According to a source, Research Center 227 will research Western cybersecurity systems and computer networks, strengthening the regime’s capabilities to steal digital assets, develop AI-based techniques for information theft, and work to respond to information from North Korean overseas hacking units. (Lorenzo Franceschi-Bicchierai / TechCrunch)
The Dutch parliament approved a law criminalizing digital espionage and diaspora espionage, which refers to foreign powers attempting to influence communities in the Netherlands with ties to those countries.
The new law expands on existing legislation, criminalizing actions such as leaking information or working for foreign governments that harm Dutch interests.
Offenders can face up to eight years in prison, with a maximum of 12 years for severe cases, such as espionage leading to death. (Charlotte Van Campenhout / Reuters)
Related: Netherlands Central Government, EuroWeekly News
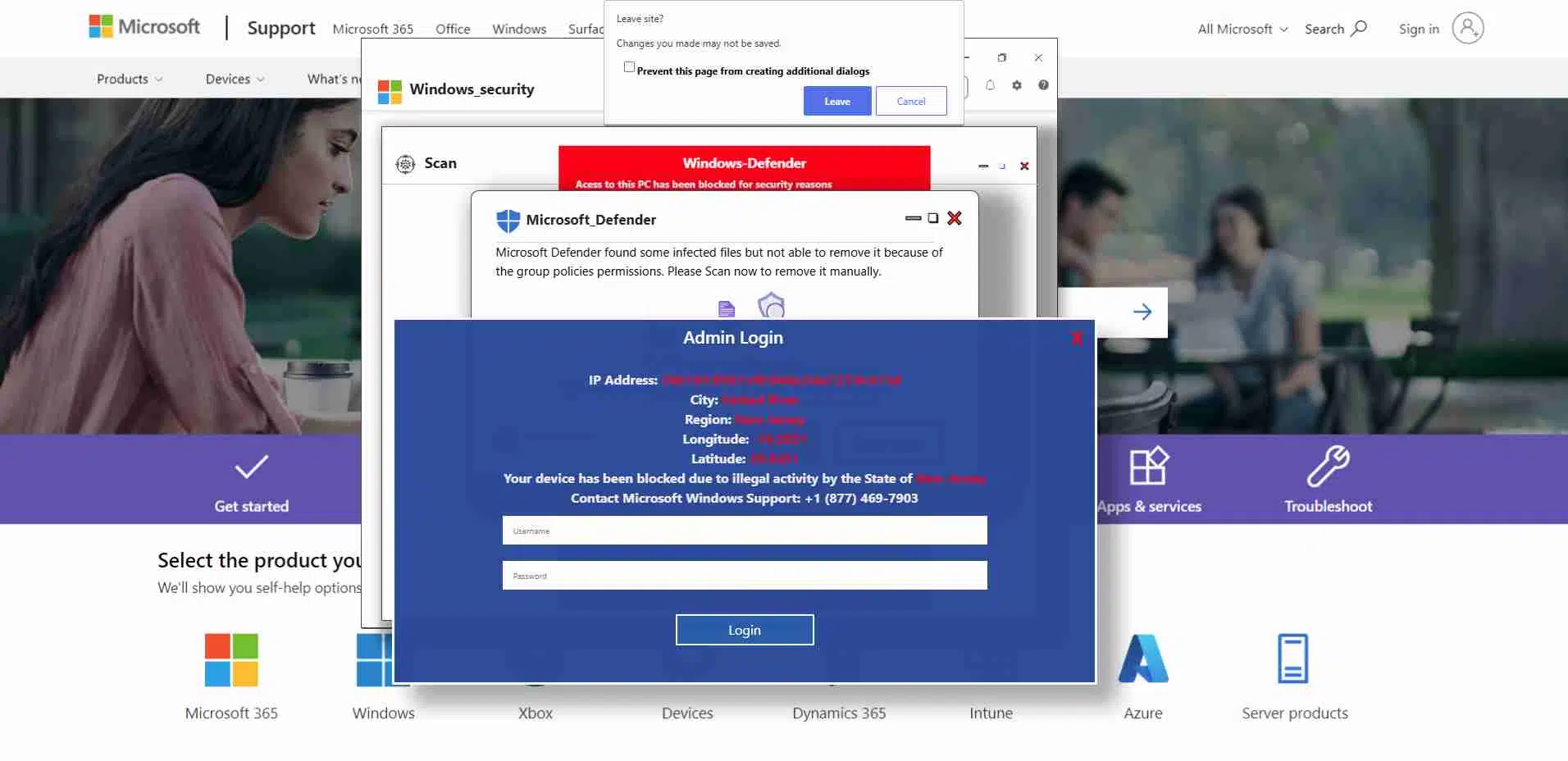
Security researchers at LayerX report that the criminals behind a phishing attack aimed at Windows users are now targeting Mac users instead in what they call one of the most sophisticated attacks ever mounted against Mac users.
The campaign initially targeted Windows users by masquerading as Microsoft security alerts. The campaign aimed to steal user credentials by employing deceptive tactics that made victims believe their computers were compromised.
LayerX says with new security features rolled out by Microsoft, Chrome, and Firefox, the attackers have shifted their focus to Mac users.
The mechanism behind the attack is a website popup window masquerading as a security alert. What enables this particular attack to fool so many people is that it uses malicious code to cause the webpage to freeze, lending credibility to the popup's claim that the computer has been locked.
Last month, Microsoft introduced an anti-scareware feature in its Edge browser, with similar protections implemented in Chrome and Firefox. That stopped 90% of the attacks on Windows PCs, so the attackers turned their focus to Macs running Safari. (Ben Lovejoy / 9to5Mac)
Related: LayerX, xda, Cybernews, MacDailyNews, MacTech, Dataconomy
Google says it uncovered thousands of illegitimate listings, including for fake businesses, on Google Maps and has announced a lawsuit against the alleged scammers behind the fraud.
The lawsuit claims a man working within a broader network created and sold fake business profiles on Google Maps.
An initial alert came from a Texas business that flagged an unlicensed locksmith impersonating them on Google Maps. That was just the tip of the iceberg.
The company said the claim sparked an investigation that led Google to uncover and eliminate over 10,000 illegitimate listings. The scams ranged from outright fake businesses to legitimate accounts that had been hacked or hijacked.
Google found that many of the scams were concentrated in what they call "duress verticals"—services people need in urgent or stressful situations, like locksmiths or towing companies.
Google said it plans to donate any damages it wins in this case to organizations working to fight scams. (Kara Fellows, Cait Bladt / CBS News)
Related: r/googler, r/technology, Forbes
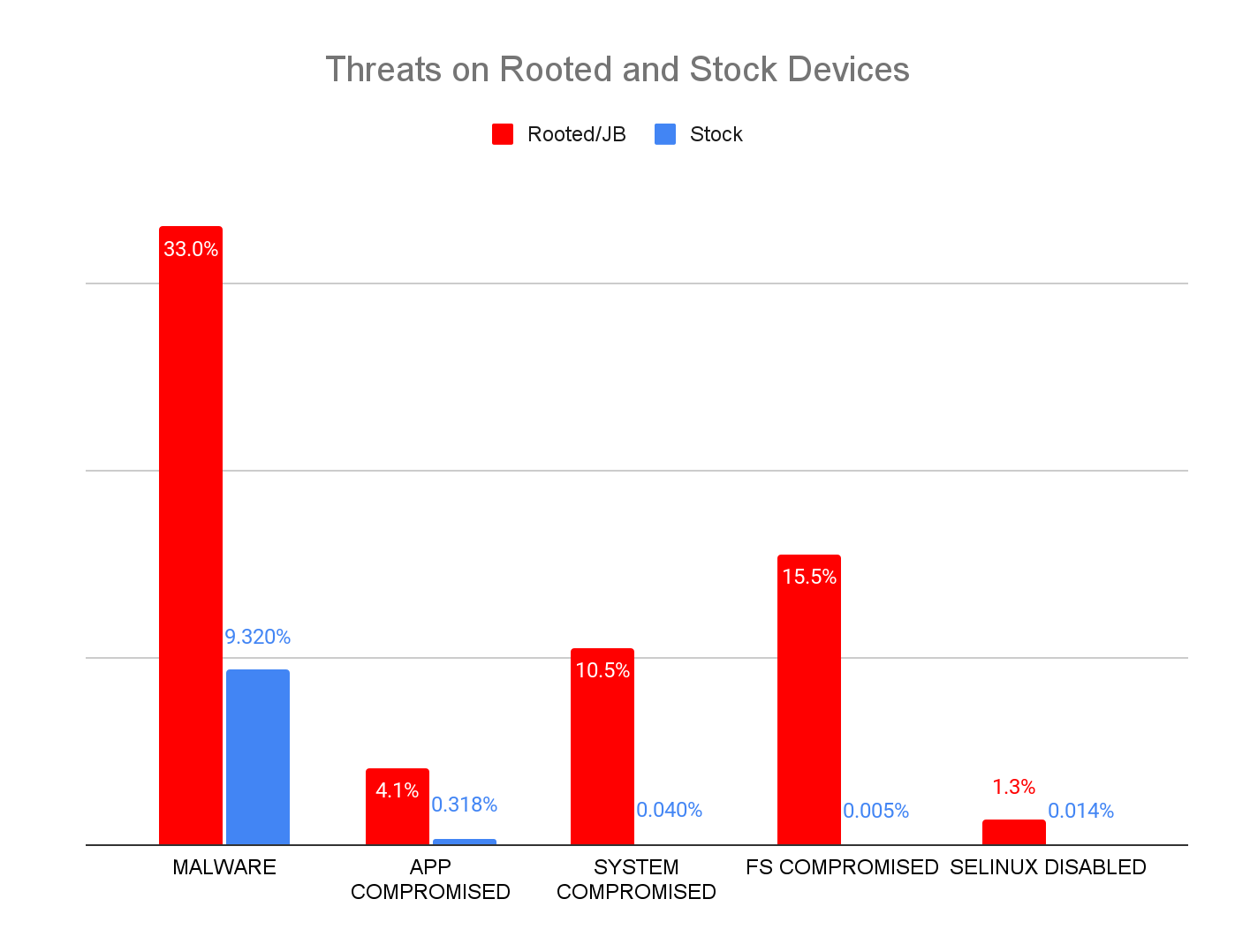
Researchers at Zimperium report that many mobile devices, one out of every one thousand, have been covertly modified to pose a security risk to organizations.
The result is millions of devices that, when scaled to a global level, could potentially be a significant network security risk.
“Despite a reduction in the number of rooted and jailbroken devices overall, they still represent a very serious security threat, not just to the user, but to enterprises who enable employees to access sensitive corporate apps and data from their devices,” wrote Zimperium.
Though the terminology differs by platform, the process is essentially the same. An automated script uses an unpatched code execution vulnerability to modify the device at the root level and disable protections against unauthorized apps.
The procedure is far more common on Android devices, with 1 in 400 devices being rooted, as opposed to around 1 in 2,500 iOS devices. (Shaun Nichols / SC Media)
Related: Zimperium
The US Cybersecurity and Infrastructure Security Agency (CISA) warned federal agencies to secure their networks against attacks exploiting a high-severity vulnerability in NAKIVO's Backup & Replication software.
Tracked as CVE-2024-48248, this absolute path traversal flaw can be exploited by unauthenticated attackers to read arbitrary files on vulnerable devices.
The US-based backup and ransomware recovery software vendor silently patched the security flaw with the release of Backup & Replication v11.0.0.88174 in November, almost two months after being notified of the issue by cybersecurity company watchTowr, who discovered the vulnerability.
In February, watchTowr also released a CVE-2024-48248 proof-of-concept described as a "detection artifact generator" that can also serve as "an unofficial NAKIVO customer support tool."
While NAKIVO did not mark the vulnerability as actively exploited in a security advisory last updated on March 6th, the company still advises customers to check the system logs for signs of "unauthorized access attempts" and "unexpected file access activities." (Sergiu Gatlan / Bleeping Computer)
Related: CISA, Nakivo, Help Net Security, Security Week
Meredith Whittaker, president of US messaging app Signal, has threatened to pull it out of France over a proposed law where the government has demanded the ability to look into private chats.
In Article 8 of the proposed “Narcotraffic” law, Sortir la France du piège du narcotrafic [Getting France out of the drug trafficking trap], France said it wanted encrypted messaging applications such as Signal and WhatsApp and encrypted email services such as Proton Mail to provide authorities with decrypted data of its users within 72 hours of request.
The French Senate passed the provision on March 4, and it was scheduled for further consideration in the National Assembly. On March 17, the Assembly’s legislative committee reviewed it, setting off significant pushback.
Whittaker put a lengthy post on X on March 19, sounding the alarm over the soon-to-be-voted-on French law.
She condemned it as a “callow, dishonest attack,” contradicting expert consensus and threatening both global cybersecurity and the fundamental human right to privacy. (Carl Deconinck / Brussels Signal)
Related: Computerworld
Attackers have started targeting Cisco Smart Licensing Utility (CSLU) instances that have not been patched against a vulnerability exposing a built-in backdoor admin account.
The CSLU Windows application allows admins to manage licenses and linked products on-premises without connecting them to Cisco's cloud-based Smart Software Manager solution.
Cisco patched this security flaw (tracked as CVE-2024-20439) in September, describing it as "an undocumented static user credential for an administrative account" that can let unauthenticated attackers log into unpatched systems remotely with admin privileges over the API of the CSLU app.
The company also addressed a second critical CLSU information disclosure vulnerability (CVE-2024-20440) that unauthenticated attackers can use to access log files containing sensitive data (including API credentials) by sending crafted HTTP requests to vulnerable devices.
These two vulnerabilities only impact systems running vulnerable Cisco Smart Licensing Utility releases. They are only exploitable if the user starts the CSLU app—which isn't designed to run in the background by default.
Aruba threat researcher Nicholas Starke reverse-engineered the vulnerability and published a write-up with technical details (including the decoded hardcoded static password) roughly two weeks after Cisco released security patches.
SANS Technology Institute's Dean of Research Johannes Ullrich reported that threat actors are now chaining the two security flaws in exploitation attempts targeting CSLU instances exposed on the Internet. (Sergiu Gatlan / Bleeping Computer)
Related: Security Affairs, Security Week, Starke Blog, SANS Internet Storm Center
Menlo Security’s analysis of 750,000 browser-based phishing attacks targeting more than 800 entities detected over the last 12 months reveals a 140% increase in browser phishing, including a 130% increase in zero-hour phishing attacks (effectively, a zero-day attack applied to phishing).
One significant factor is the growth of genAI by threat actors. The firm detected nearly 600 incidents with imposter sites passing themselves off as gen-AI sites offering fake AI services.
Most gen-AI fraud was not for credential theft (the traditional first purpose of phishing). Harding notes that fake gen-AI sites trick people into entering personal data to generate a resume. (Kevin Townsend / Security Week)
Related: Menlo Security, Security Magazine, Techzine
Russian internet users this week faced widespread outages that regulators attributed to issues with “foreign server infrastructure" that local experts said stemmed from Russia’s blocking of Cloudflare.
According to data from several internet monitoring websites, the outages were observed Thursday across multiple Russian regions, particularly in the Urals and Siberia. They affected platforms such as TikTok, Steam, Twitch, Epic Games, Duolingo, and major Russian mobile operators.
The disruption also impacted banking and government services, with users reporting difficulties accessing apps for Sberbank, Gazprombank, and Alfa-Bank, as well as the Russian government’s portal. Messaging apps, including Telegram and WhatsApp, also faced interruptions.
Russian internet regulator Roskomnadzor said the disruptions affected services that rely on foreign server infrastructure and recommended that local organizations switch to Russian hosting providers.
Roskomnadzor announced plans to inspect Russian services and telecom operators for using foreign servers, stating that these measures are necessary to improve the resilience and security of Russia’s internet infrastructure.
“This blocking is a kind of ‘trial shot’ — both to see how much disruption it causes and to push Russian-based resources away from Cloudflare, signaling that it won’t work reliably and will only create problems for them,” said Roskomsvoboda’s technical director, Stanislav Shakirov.
Shakirov suggested that Roskomnadzor will eventually block Cloudflare entirely. (Daryna Antoniuk / The Record)
Newly unsealed court records show federal law enforcement agencies have turned to a variety of techniques and surveillance capabilities to identify people who have allegedly set fire to Tesla vehicles and property, including automatic license plate readers and social media crawling.
The documents come from cases that Attorney General Pamela Bondi announced on Thursday. The charges also come as sentiment towards Tesla and Elon Musk is at an all-time low. People have participated in regular and largely non-violent “Tesla Takedown” protests, and there have been multiple acts of vandalism around the country. This has captured the attention of Musk, Bondi, and Donald Trump, who are now all claiming that vandalizing Teslas will be treated as an act of domestic terrorism.
Details about the surveillance techniques used to identify the alleged vandals show that police used a combination of automatic license plate readers and social media monitoring to investigate two of the crimes. In the third, the suspect was identified based on a combination of license plate records and fingerprints left on a Molotov cocktail bottle. (Jason Koebler / 404 Media)
Related: Justice.gov, Reuters, NBC News, CBS News
Best Thing of the Day: Give Us More Rulings Like This, But Make Them Permanent
US District Judge Ellen Hollander in Maryland temporarily blocked billionaire Elon Musk’s Department of Government Efficiency from Social Security systems that hold personal data on millions of Americans, calling their work there a “fishing expedition.”
Bonus Best Thing of the Day: I'm having trouble printing a music video from YouTube
American Twitch streamer and YouTuber Kitboga built a bot army of various personas in an AI call center that scams the scammers at scale, most often for hours and frequently for days, and it's marvelous to behold.
Closing Thought