Chinese Hackers Breached US Office That Reviews Foreign Investment Security Risks
TX AG probes social media companies on child data collection, Rogue advertisers harvest sensitive data from Gravy Analytics, Facebook RCE bug nets researchers $100k, States settle with Bayview Asset Management over breach, Winston-Salem struggles with cyberattack, DarkTrace to buy Cado, much more


Please consider supporting Metacurity with an upgraded subscription so that you can continue to receive our daily missives packed with the top infosec developments you should know.
If you can't commit to a subscription today, consider tipping or donating to help keep Metacurity going.
According to sources, in December, Chinese hackers breached the Committee on Foreign Investment in the US (CFIUS), the US government office that reviews foreign investments for national security risks.
This intrusion underscores Beijing’s keen interest in spying on a US government office with broad powers to block Chinese investment in the US.
The breach was part of a broader incursion by the hackers into the Treasury Department’s unclassified system.
As first reported by the Washington Post, the hackers also targeted the Treasury Department’s sanctions office. Just last week, the office sanctioned a Chinese company for its alleged role in cyberattacks.
According to Bloomberg News, Silk Typhoon is the Chinese hacking group that targeted the Treasury Department. (Sean Lyngaas / CNN)
Related: Reuters, The Economic Times, Devdiscourse, The Jerusalem Post
Rumble, Quora, and WeChat are among the 15 companies from which Texas Attorney General Ken Paxton has demanded answers by next week about their collection and use of data of people under 18 years old.
Paxton announced the investigation in a press release last month but named only four of the companies being probed: Character.AI, Reddit, Instagram, and Discord. The names of additional targeted companies through a public records request. They also include Kick, Kik, Pinterest, Telegram, Twitch, Tumblr, WhatsApp, and Whisper.
The variety of companies questioned highlights the sprawling reach of a new Texas law to increase oversight of minors’ use of social media and chat services.
Experts in youth privacy regulations who have been following Paxton’s enforcement efforts say the new investigation should be treated credibly, and they believe it could result in companies agreeing to improve their practices. The alternative could be hundreds of millions of dollars in penalties per company.
Paxton’s interest in Rumble, a YouTube-like website popular among US conservative political commentators, is perhaps unexpected given his track record of partisan views about social media companies. Rumble has touted itself as a haven for free expression, unlike platforms that engage in allegedly heavier content moderation. Paxton is a Republican and has criticized platforms that unfairly silence Texans. (Paresh Dave / Wired)
According to hacked files from location data company Gravy Analytics, some of the world’s most popular apps, including Candy Crush and Tinder, are likely being co-opted by rogue members of the advertising industry to harvest sensitive location data on a massive scale, with that data ending up with a location data company whose subsidiary has previously sold global location data to US law enforcement.
Because much of the collection occurs through the advertising ecosystem, not code developed by the app creators themselves, this data collection is likely happening without the users’ and even app developers’ knowledge.
“For the first time publicly, we seem to have proof that one of the largest data brokers selling to both commercial and government clients appears to be acquiring their data from the online advertising ‘bid stream,’” rather than code embedded into the apps themselves, Zach Edwards, senior threat analyst at cybersecurity firm Silent Push, said after reviewing some of the data.
The hacked Gravy data includes tens of millions of mobile phone coordinates of devices inside the US, Russia, and Europe. Some of those files also reference an app next to each piece of location data.
The list includes dating sites Tinder and Grindr; massive games such as Candy Crush, Temple Run, Subway Surfers, and Harry Potter: Puzzles & Spells; transit app Moovit; My Period Calendar & Tracker, a period tracking app with more than 10 million downloads; popular fitness app MyFitnessPal; social network Tumblr; Yahoo’s email client; Microsoft’s 365 office app; and flight tracker Flightradar24. The list also mentions multiple religious-focused apps such as Muslim prayer and Christian Bible apps, various pregnancy trackers, and many VPN apps, which some users may download, ironically, in an attempt to protect their privacy. (Joseph Cox / 404 Media)
Related: Pixel Envy, Hacker News (ycombinator), Hacker News (ycombinator), Slashdot
Security researcher Ben Sadeghipour and independent researcher Alex Chapman found a security vulnerability that allowed him to run commands on the internal Facebook server housing that platform, essentially giving him control of the server, and were awarded $100,000 in a bug bounty for their work.
According to Sadeghipour, the issue was that one of the servers that Facebook used for creating and delivering ads was vulnerable to a previously fixed flaw found in the Chrome browser, which Facebook uses in its ads system.
Sadeghipour said this unpatched bug allowed him to hijack it using a headless Chrome browser (essentially a browser version that users run from the computer’s terminal) to interact directly with Facebook’s internal servers. (Lorenzo Franceschi-Bicchierai / TechCrunch)
Related: Cyber Security News
In a settlement with fifty-three state-level regulators, mortgage company Bayview Asset Management will pay a $20 million penalty over an October 2021 data breach and its alleged failure to cooperate with regulators in the aftermath.
The Conference of State Bank Supervisors (CSBS) said Bayview, a Coral Gables, Fla.-based investment manager that owns mortgage-servicing firms, had deficient information technology practices and suffered a 2021 data breach that affected 5.8 million customers.
Bayview then failed to cooperate with regulators as they sought information. Agencies in 53 jurisdictions, led by California, Maryland, North Carolina, and Washington state regulators, took coordinated action against Bayview, which entered into a settlement.
Bayview has also agreed to take corrective actions, including improving its cybersecurity programs, undergoing independent assessment, and making reports to state regulators for three years. (Richard Vanderford / Wall Street Journal)
Related: Cleveland.com, Housing Wire, The Business Journals, WYTV, Inman
Winston-Salem, North Carolina, residents cannot pay their utility bills online after a post-Christmas cyberattack knocked the city’s systems offline.
City officials initially announced a cyberattack on December 30, telling residents they discovered issues with their digital platforms one day after Christmas.
Although Winston-Salem was forced to take down all the digital payment systems for water and electricity bills, officials reiterated that no service interruptions or late penalties would be charged to accounts. Residents can still pay in person with cash or checks.
A list of phone numbers was provided to residents who need to contact departments directly with specific issues.
Winston-Salem’s government has not provided an update since December 30. (Jonathan Greig / The Record)
Related: Winston-Salem, WGHP, Spectrum News, WXLV
BayMark Health Services, North America's largest provider of substance use disorder (SUD) treatment and recovery services, is notifying an undisclosed number of patients that attackers stole their personal and health information in a September 2024 breach.
In data breach notification letters mailed to affected individuals, BayMark revealed that it learned of the breach on October 11, 2024, following an IT systems disruption. A follow-up investigation revealed that the attackers accessed BayMark's systems between September 24 and October 14.
Baymark is now offering a year of free Equifax identity monitoring services to patients whose Social Security numbers or driver's license numbers may have been exposed in the incident. (Sergiu Gatlan / Bleeping Computer)
Related: Vermont AG, JD Supra, HIPAA Journal
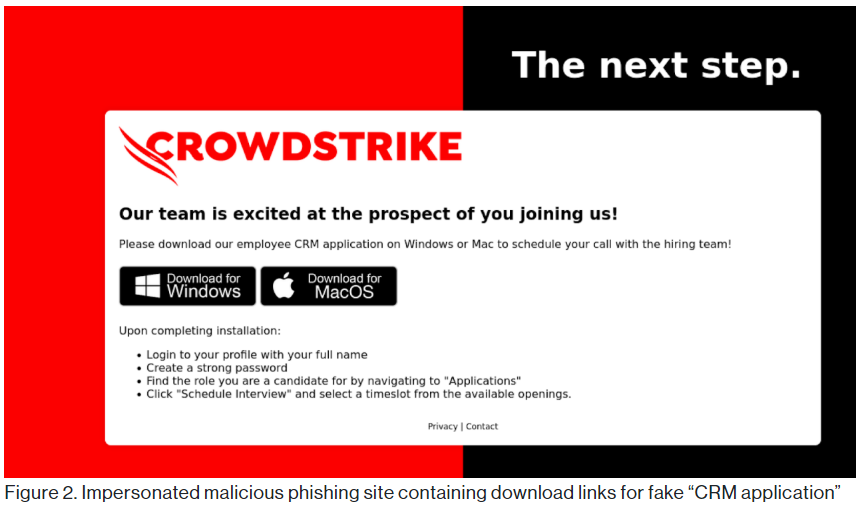
CrowdStrike is warning that a phishing campaign is impersonating the cybersecurity company in fake job offer emails to trick targets into infecting themselves with a Monero cryptocurrency miner (XMRig).
The company discovered the malicious campaign on January 7, 2025, and based on the phishing email's content, it likely didn't start much earlier.
The attack starts with a phishing email sent to job seekers, supposedly from a CrowdStrike employment agent, thanking them for applying for a developer position at the company. The email asks the recipients to download an application, something that employers rarely do, which then delivers the mining malware.
The miner is set to run in the background, consuming minimal processing power (max 10%) to avoid detection. (Bill Toulas / Bleeping Computer)
Related: CrowdStrike, Bitcoin.com
Researchers at Check Point report that a new version of the Banshee info-stealing malware for macOS has been evading detection over the past two months by adopting string encryption from Apple's XProtect.
The encryption method present in Banshee allows it to blend in with normal operations and appear legitimate while collecting sensitive information from infected hosts. Another change is that it no longer avoids systems belonging to Russian users.
The latest Banshee stealer variant is primarily distributed via deceptive GitHub repositories targeting macOS users through software impersonation. The same operators also target Windows users but with Lumma Stealer. (Bill Toulas / Bleeping Computer)
Related: CheckPoint, Dark Reading, HackRead, Help Net Security, SC Media
According to court testimony, Orlin Roussev, a Russian spy who was living in a "typical seaside hotel" on the English coast crammed full of electronic surveillance equipment, boasted to his controller that he was becoming like the James Bond character "Q" as he prepared his spying "toys" for kidnap and surveillance operations across Europe.
Among the gear he hoarded were IMSI catchers, pendant necklaces with hidden cameras, water bottles with mobile phone-linked video surveillance capability, a Pandora car key cloning device, and more traditional surveillance equipment such as night vision binoculars and mobile radios.
Roussev is said to have taken instructions from a handler called Jan Marsalek, who is wanted in connection with a £1.6bn ($1.97 billion) tech fraud linked to a company called Wirecard.
Roussev, a Bulgarian national, has pleaded guilty to running a spy ring on behalf of the Russians, but three other members of the group deny the charges. (Duncan Gardham / Sky News)
Related: Daily Mail, The Telegraph, The Mirror
Cybersecurity company DarkTrace, owned by private equity giant Thoma Bravo, announced the “proposed acquisition” of UK-based incident investigation and response firm Cado Security.
Financial terms have not been disclosed for the deal, which is expected to be completed in February, but the Australian Financial Review (AFR) reported that Darktrace will pay an estimated $50 million to $100 million, subject to regulatory approvals.
Darktrace said the amount reported by AFR is not a number it recognizes and noted that it’s not disclosing the acquisition price.
The British cybersecurity giant plans to continue enhancing Cado’s existing products while combining its investigation technology with its ActiveAI platform. Cado’s founders, James Campbell (CEO), Chris Doman (CTO), and the Cado team, will join Darktrace. (Edward Kovacs / Security Week)
Related: PR Newswire, CRN, The Fast Mode, Silicon Angle, Channel Futures, Techzine, ITPro, Financial Review, Cyber Daily, UKTN, The Times, GovInfoSecurity
Israeli startup Wiz said it had named veteran executive Fazal Merchant as president and chief financial officer to keep driving the cloud security firm's growth and prepare for a U.S. share offering in about a year.
Wiz last July rebuffed a reported $23 billion takeover deal by Google-parent Alphabet that would have made it the U.S. tech giant's largest-ever acquisition.
At the time, Wiz CEO Assaf Rappaport said the company would focus on an initial public offering and its goal of achieving an annual recurring revenue of $1 billion. (Steven Scheer / Reuters)
Related: The Information, Globes Online, Seeking Alpha, Wall Street Journal, CRN, Tech in Asia
Best Thing of the Day: Fighting MAGA Wildfire Misinformation
Watch Duty, created by Santa Rosa-based nonprofit Sherwood Forestry Service, tracks fire risk and firefighting efforts in real-time and has become an oasis of accurate information and a voice against a wave of MAGA-led misinformation during the Los Angeles wildfires.
Worst Thing of the Day: Speaking of MAGA Wildfire Misinformation...
A video going viral this week of the Hollywood sign in Los Angeles with a wildfire raging behind it and letters glowing in the blaze, is AI-generated, as are other images and videos generated by MAGA sympathizers on social media.
Closing Thought





