Asian gangs are spreading cyber scam compounds globally, UN
Secure by Design architects to leave CISA, Korea's top telco hacked, MSFT's Recall still poses problems, Fog ransomware baits victims by invoking Musk's DOGE, Elusive Comet threat actor stole $100K from NFT platform CEO, Telegram to leave France if backdoors are mandated, much more
Metacurity is a reader-supported publication that requires significant work and non-trivial expenses. We rely on the generous support of our paid readers. Please consider upgrading your subscription to support Metacurity's ongoing work. Thank you.
If you're unable to commit to a subscription today, please consider donating whatever you can. Thank you!
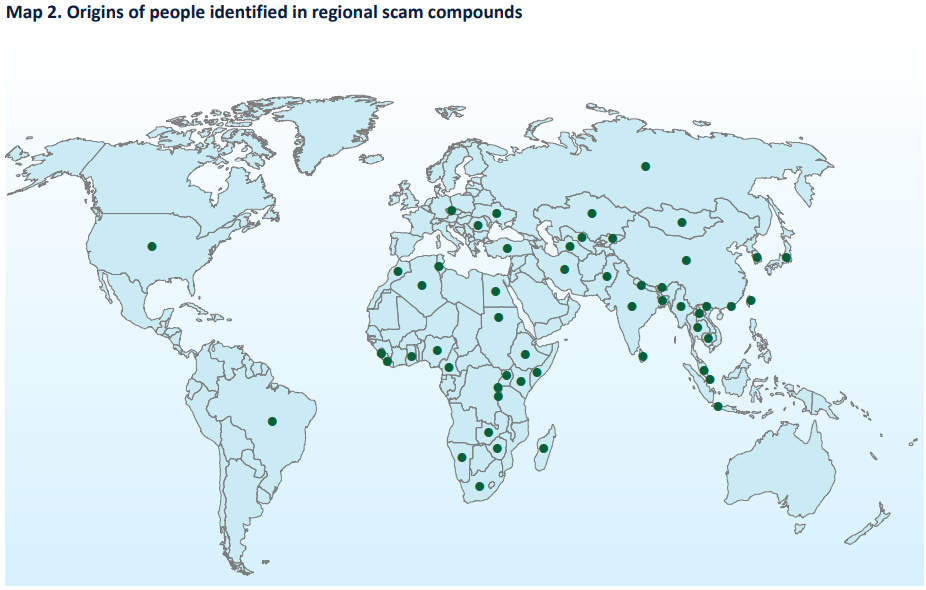
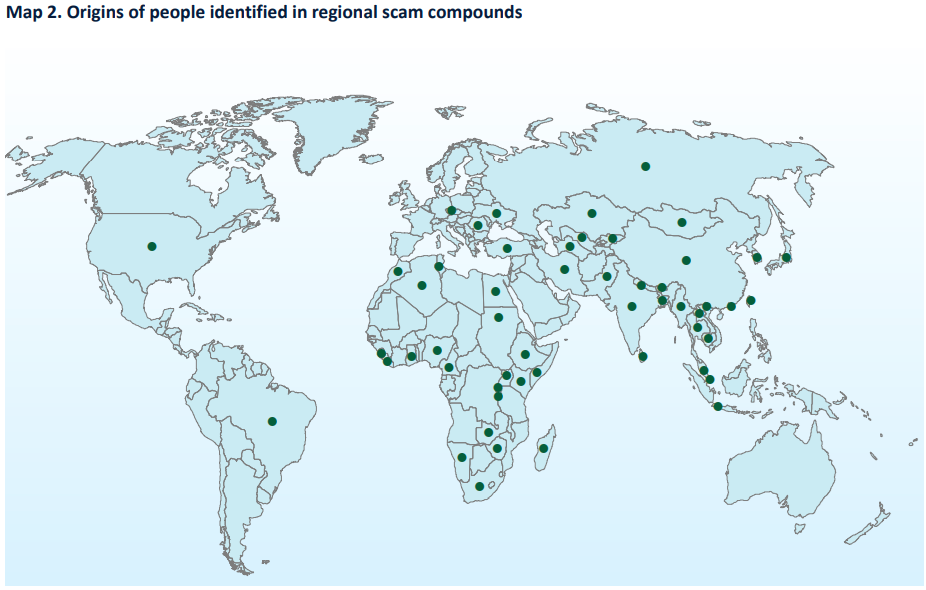
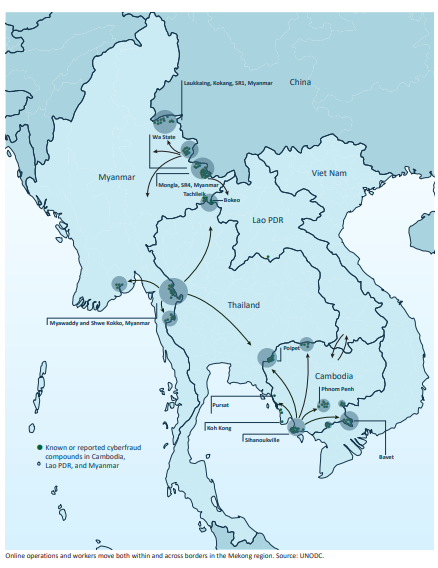
A report from the United Nations Office on Drugs and Crime (UNODC) warns that Asian crime syndicates behind the multibillion-dollar cyber scam industry are expanding globally, including to South America and Africa, as raids in Southeast Asia fail to contain their activities.
The UNODC said criminal networks that emerged in Southeast Asia in recent years, opening sprawling compounds housing tens of thousands of workers, many trafficked and forced to scam victims around the world, have evolved into a sophisticated global industry.
Even as Southeast Asian governments have intensified a crackdown, syndicates have moved within and beyond the region, the agency said, adding that a “potentially irreversible spillover has taken place... leaving criminal groups free to pick, choose, and move... as needed”.
“It spreads like a cancer,” said Benedikt Hofmann, UNODC acting regional representative for Southeast Asia and the Pacific. “Authorities treat it in one area, but the roots never disappear; they simply migrate.”
Conservative estimates suggest that hundreds of large-scale scam farms operate worldwide, generating tens of billions of dollars in annual profits, according to the UNODC. The agency called on countries to work together and intensify efforts to disrupt the gangs' financing. (Poppy McPherson / Reuters)
Related: UNODC, UNODC, DW, The Diplomat, The Record, Fortune, Al Jazeera, News Central, Sky News, UNN
Two of the chief architects behind CISA’s Secure by Design initiative, Bob Lord, senior technical adviser, and Lauren Zabierek, senior advisor at the Cybersecurity and Infrastructure Security Agency (CISA), announced they are leaving the agency.
Lord said he would continue “contributing” to Secure by Design after a short break. Both specifically praised the program in their announcements, with Zabierek arguing it has impacted the way product manufacturers and policymakers approach cybersecurity.
The departures raise questions about the fate of Secure by Design, which was launched under the Biden administration and at a time when the White House was looking to expand CISA’s budget and portfolio. Under the Trump administration, the agency has suffered severe cuts to personnel and resources. Secretary of Homeland Security Kristi Noem stated earlier this year that she intended to transform CISA into a “more nimble” organization with a less expansive mission.
“CISA remains laser-focused on working across the public and private sectors to improve the nation’s cybersecurity, a critical element of which is ensuring that technology companies do their part,” Bridget Bean, acting CISA Director, told CyberScoop in a statement. “This is why we continue to urge companies to develop products that are secure by design, instead of passing the cost of poorly designed products on to consumers." (Derek B. Johnson / CyberScoop)
Related: The Record, Bob Lord on LinkedIn, Lauren Zabierek on LinkedIn
Korea's largest telecommunications company, SK Telecom, stated that its internal systems had been compromised by a hacking attack, potentially leading to a data leak involving USIM cards, or SIM cards designed for 3G networks.
The company stated that it had reported the case to the Korea Internet & Security Agency, noting that there have been no confirmed instances of the leaked information being misused.
The mobile carrier detected suspicious activity around 11 p.m. on Saturday, indicating that hackers had infiltrated its internal systems and installed malware. Upon detection, the company stated that it immediately removed the malware, isolated the affected equipment, and launched a comprehensive investigation across its systems.
As a precautionary measure, the company is also strengthening its defense against unauthorized USIM swaps and suspicious authentication attempts. The company said it will also offer a USIM protection service free of charge to customers upon request. (Jo He-rim / The Korea Herald)
Related: The Chosun Daily, Mobile World Live, Tech in Asia, Bloomberg Law, The Fast Mode, The Korea Times, Yonhap News Agency, Telecom Paper, Chosun Biz, Korea JoongAng Daily
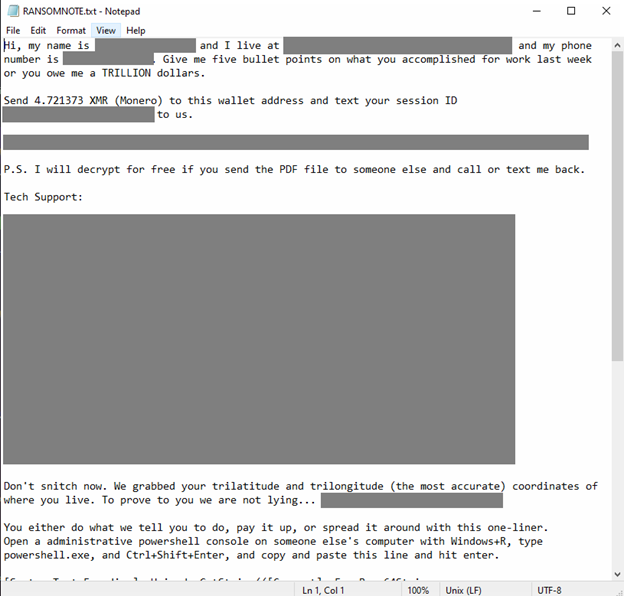
Security researcher Kevin Beaumont has examined the changes in Microsoft's notorious Recall feature between its announcement last year and its current rollout to users on an opt-in basis.
Recall, a feature that takes screenshots of a user's PC every few seconds, OCRs the screenshots, and produces a searchable text database of everything the user has ever viewed or written from their computer.
According to Beaumont, Microsoft has improved Recall by making it opt-in, encrypting its SQLite database, and attempting to filter out sensitive data such as credit card numbers.
According to Beaumont, Microsoft has improved Recall by making it opt-in, encrypting its SQLite database, and attempting to filter out sensitive data such as credit card numbers.
On the downside, Recall allows anyone with just a PIN to search snapshots, scroll through any prior snapshot, and export data. Moreover, the sensitive data filtering isn't great and Recall still captures and stores things after deletion, among other negative features. (Kevin Beaumont / DoublePulsar)
Related: Ars Technica, Techdirt
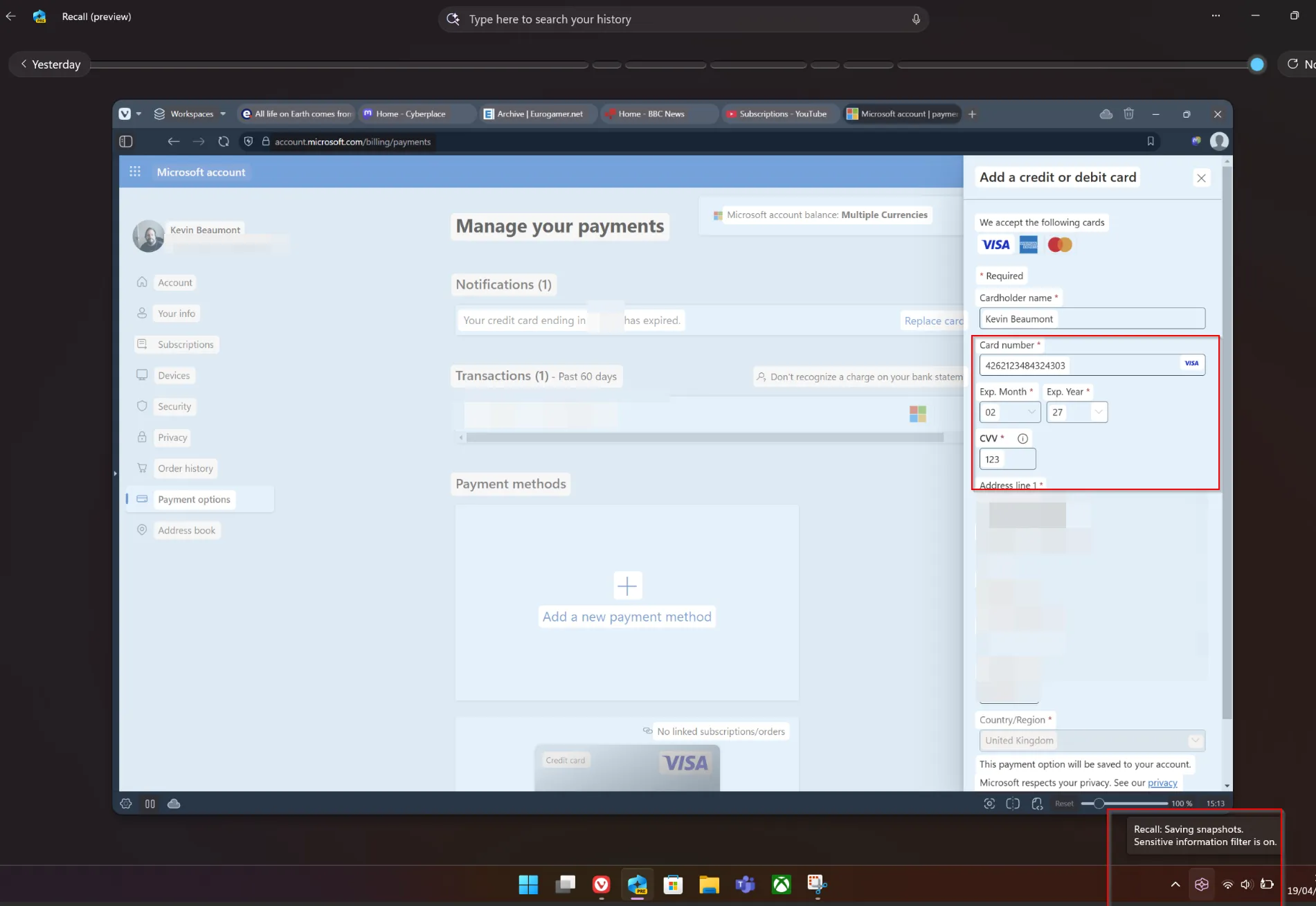
Researchers at Trend Micro report that Fog ransomware attacks over the past month have featured a new ransom note referencing the US Department of Government Efficiency (DOGE) and baiting victims to spread the malware to other machines.
Analyses of the latest samples of Fog ransomware, which were uploaded to VirusTotal between March 27 and April 2, 2025, revealed their spread through the distribution of a ZIP file containing a LNK file disguised as a PDF named “Pay Adjustment," suggesting the attacks were conducted through phishing emails to employees.
While the final ransom note, readme.txt, is the same as seen in previous attacks, the initial ransom note, RANSOMNOTE.txt, makes references to DOGE, including names of specific individuals associated with the department.
The note states, “Give me five bullet points on what you accomplished for work last week,” referencing emails sent to federal employees in February as part of a DOGE initiative. The note also offers to decrypt the user’s data for free if they send the malicious files to another person or directly execute the malicious PowerShell commands on another person’s machine. (Laura French / SC Media)
Related: Trend Micro, Dark Reading, Cybernews, GBHackers
The chief executive of the non-fungible token platform Emblem Vault is warning X users to be wary of the video meeting app Zoom after a nefarious threat actor, known as “ELUSIVE COMET,” recently stole over $100,000 of his personal assets.
On April 11, Jake Gallen, CEO of Emblem Vault, podcaster, and NFT collector, said on X that he had been battling a “complete computer compromise” that resulted in the loss of Bitcoin and Ether assets from various wallets. “Unfortunately, this led to $100k+ in purchased digital assets being lost,” he said.
Days later, Gallen stated that he had been collaborating with cybersecurity firm The Security Alliance (SEAL) to investigate an ongoing campaign targeting crypto users by a threat actor identified as “ELUSIVE COMET.”
Gallen stated that the scam was facilitated through the video conference platform Zoom, resulting in his cryptocurrency wallet being drained.
“We were able to retrieve a malware file that was installed on my computer during a Zoom call with a YouTube personality of over 90k subs,” said Gallen on April 14. (Martin Young / Cointelegraph)
Related: Security Alliance, Dark Reading, Trail of Bits, Dark Reading, Help Net Security, Cryptonews
Telegram CEO Pavel Durov expressed concerns over a growing threat to private messaging in France and other European Union countries, warning that Telegram would rather exit certain markets than implement encryption backdoors that undermine user privacy.
In a post to his “Du Rove’s channel” on Telegram, he shared a message about the EU’s increasing efforts to weaken messaging encryption by introducing backdoors, a method that would enable authorities to bypass encryption and access private user data.
Durov cited initiatives from French and EU lawmakers to require messaging apps like Telegram to implement backdoors for police access and stressed Telegram’s commitment to digital privacy.
“Telegram would rather exit a market than undermine encryption with backdoors and violate basic human rights,” Durov stated, adding: “Unlike some of our competitors, we don’t trade privacy for market share.” (Helen Partz / Cointelegraph)
Related: Telegram, Cryptoslate, CCN, TradingView
The government of Abilene, Texas, shut down some of its systems due to a cyberattack the city became aware of on Friday.
“Out of an abundance of caution, certain systems have been taken offline. However, emergency services are still up and running with the continued ability to assist timely, and no unidentified financial activity has been detected,” the city said on Monday.
Due to the outages, none of the card systems at government offices are working, forcing people to pay with cash or checks. The city pledged not to shut off utilities due to overdue accounts and stated that payments can also be made online using credit cards. (Jonathan Greig / The Record)
Related: City of Abilene, KTXS, Beyond Machines, Security Affairs, KTAB, Abilene Reporter News
Northern District of California Judge Phyllis Hamilton last week placed strict limits on the kind of evidence NSO Group can raise during a trial on damages in the lawsuit WhatsApp brought against the spyware vendor over allegations it hacked 1,400 of the messaging platform’s users.
Under the order, NSO Group is prohibited from presenting evidence about its customers’ identities, implying the targeted WhatsApp users are suspected or actual criminals, or alleging that WhatsApp had insufficient security protections.
NSO Group, too, won some concessions in the ruling. WhatsApp cannot introduce evidence of the identities and occupations of the 1,400 targets, nor evidence about other lawsuits against NSO over the use of Pegasus related to the death of Washington Post journalist Jamal Khashoggi. (Tim Starks / CyberScoop)
Related: Court Listener, The Record
Cybersecurity startup Reco, which offers what it calls “Dynamic SaaS Security,” announced it had raised $25 million in additional venture capital funding.
The funding comes from Insight Partners, Zeev Ventures, boldstart ventures, Angular Ventures, and new investor Redseed. (Meir Orbach / CTech)
Related: Business Insider Africa, Access Newswire
Best Thing of the Day: It's Very Important to Achieve the Right Temperature in Your Living Space
After they moved into an apartment, software developer Videah engaged in a replay attack on the radio protocols that communicated with his landlord's boiler and "puppeteered" the boiler as if they were the thermostat.
Worst Thing of the Day: Maybe This Is a Good Place to Make the US Government More Efficient
The FBI is unable to locate records related to its purchase of a series of hacking tools, despite spending hundreds of thousands of dollars on them and including those purchases in a public US government procurement database before they were quietly removed from the internet.
Closing Thought