A Lapsed Domain Can Destroy Secure Internet Comms, Researchers
MSFT issued Patch Tuesday fixes for at least 79 security vulnerabilities, Facebook admits to wholesale scraping of Australian accounts, Crypto exchange Indodax temporarily shuts down following $22M theft, Golf course and hospitality giant Kemper hit by data breach, much more


A message from Cynthia: Metacurity needs your support to continue providing you with daily summaries of the most critical infosec developments you should know. Please consider signing up for a paid subscription so that I can continue this work.
Benjamin Harris and Aliz Hammond of WatchTowrLab "watched the foundation of secure Internet communication crumble" before their eyes after they spent $20 to achieve remote code execution by purchasing a lapsed domain and accidentally becoming the admins of .MOBI.
They achieved this after starting research to make vulnerabilities in WHOIS clients and how they parse responses from WHOIS servers exploitable in the real world.
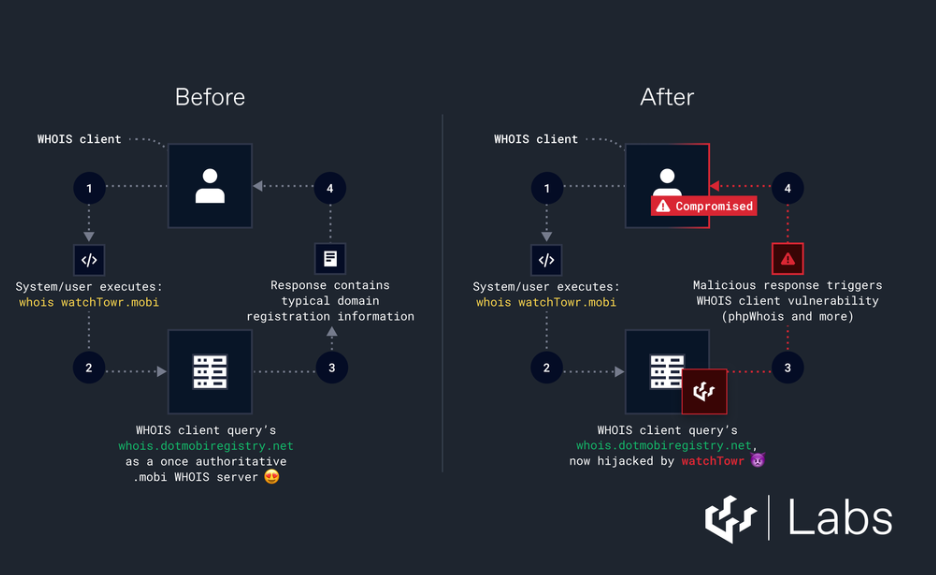
They discovered that a few years ago, the WHOIS server for the .MOBI TLD migrated from whois.dotmobiregistry.net to whois.nic.mobi, and the dotmobiregistry.net domain had been left to expire seemingly in December 2023, so they purchased dotmobiregistry.net.
They deployed a WHOIS server behind the whois.dotmobiregistry.net hostname just to see if anything would speak to it actively, with stunning results. They identified 135,000+ unique systems speaking to them, and as of September 4, 2024, they had 2.5 million queries.
Queries came from various mail servers for GOV and MIL entities using the WHOIS server to presumably query for domains they are receiving email from, as well as from various cyber security tools and companies still using this WHOIS server as authoritative (VirusTotal, URLSCAN, Group-IB, as examples).
More importantly, they realized that numerous Certificate Authorities responsible for issuing TLS/SSL certificates for domains like Google. mobi and Microsoft. mobi, via the 'Domain Email Validation' mechanism for verifying domain ownership, were using their WHOIS server to determine the domain's owners, and where verification details should be sent.
They PoC'd this with GlobalSign and demonstrated that for 'microsoft.mobi', GlobalSign would parse responses provided by our WHOIS server and present 'whois@watchtowr.com' as an authoritative email address.
Effectively, they had inadvertently undermined the CA process for the entire.mobi TLD. Once they controlled the WHOIS server, they were in the position to ‘respond’ to traffic sent by anyone who hadn’t updated their client to use the new address (auto-updates are bad; turn them off).
They no longer required a Man-In-The-Middle attack or an exotic WHOIS referral to exploit a WHOIS client vulnerability. They only needed to wait for queries and theoretically respond with whatever they wanted. (Benjamin Harris and Aliz Hammond / Watchtowr Labs)
Related: The Register, Ycombinator
On Patch Tuesday, Microsoft released updates to fix at least 79 security vulnerabilities in its Windows operating systems and related software, including existing flaws in active attacks.
Microsoft also corrected a critical bug that has caused some Windows 10 PCs to remain dangerously unpatched against actively exploited vulnerabilities for several months this year.
The most interesting security weakness disclosed was CVE-2024-43491. Microsoft says this vulnerability led to the rolling back of fixes for some vulnerabilities affecting “optional components” on certain Windows 10 systems produced in 2015. Those include Windows 10 systems that installed the monthly security update for Windows released in March 2024 or other updates released until August 2024.
“To correct this issue, users need to apply both the September 2024 Servicing Stack Update and the September 2024 Windows Security Updates,” Narang said.
Kev Breen, senior director of threat research at Immersive Labs, said the root cause of CVE-2024-43491 is that on specific versions of Windows 10, the build version numbers checked by the update service were not handled correctly in the code.
The first zero-day fixed for Microsoft this month is CVE-2024-38226. It concerns a weakness in Microsoft Publisher, a standalone application included in some versions of Microsoft Office. This flaw lets attackers bypass Microsoft’s “Mark of the Web,” a Windows security feature that marks files downloaded from the Internet as potentially unsafe.
The second zero-day is CVE-2024-38217, also a Mark of the Web bypass affecting Office. Both zero-day flaws rely on the target opening a booby-trapped Office file.
Adobe also released updates to fix security vulnerabilities in various products, including Reader and Acrobat, After Effects, Premiere Pro, Illustrator, ColdFusion, Adobe Audition, and Photoshop. Adobe says it is unaware of any exploits in the wild for any issues addressed in its updates. (Brian Krebs / Krebs on Security)
Related: Microsoft, SANS Internet Storm Center, Ask Woody, CSO Online, Forbes, Infosecurity Magazine, Security Week, Security Affairs, The Stack, The Cyber Express, Computer Weekly, Techzine, Neowin, Help Net Security, Cyberscoop, Tech Republic, Cyber Daily, Rapid7, Bleeping Computer, Bleeping Computer, Bleeping Computer
Under questioning from Australian Labor senator Tony Sheldon, Facebook admitted that it scrapes the public photos, posts, and other data of Australian adult users to train its AI models and provides no opt-out option, even though it allows people in the European Union to refuse consent.
Meta's global privacy director, Melinda Claybaugh, was pressed at an inquiry into whether the social media giant was hoovering up the data of all Australians to build its generative artificial intelligence tools and initially rejected that claim.
Claybaugh added that accounts of people under 18 were not scraped, but when Senator Sheldon asked whether public photos of his own children on his account would be scraped, Claybaugh acknowledged they would.
In June, Meta notified users in the European Union and the United States that it would use their data to train its generative AI products, such as Meta AI, unless users opted out.
The company provided an opt-out option to EU users in part because of the legal uncertainty surrounding strict privacy laws in those nations.
Ms Claybaugh admitted to the inquiry that those opt-out options were not offered to Australians. (Jake Evans / ABC.net.au)
Related: Information Age, AdNews News, NewsBytes, The Age, Yahoo Finance, The Canberra Times, The Australian, RNZ, The West Australian, The North West Star, Federal Court of Appeal Canada
Indonesian crypto exchange Indodax lost approximately $22 million in various cryptocurrencies and subsequently disabled its mobile and web applications to investigate the breach.
SlowMist’s independent investigation suggested a breach in Indodax’s withdrawal system, which allowed the hacker to withdraw funds from the exchange’s hot wallet. Cyvers, on the other hand, believed other systems were attacked, such as the signature machine.
The hacker stole over $1.42 million in Bitcoin, $2.4 million in Tron blockchain tokens, over $14.6 million in various ERC-20 tokens, $2.58 million in POL, and $0.9 million ETH from the Optimism blockchain.
Cyvers detected over 150 suspicious transactions over multiple networks and reported that the hacker started swapping the tokens for ETH. After converting the stolen funds to ETH, hackers use crypto-mixing services such as Tornado Cash to siphon the loot anonymously.
Yosi Hammer, the head of AI at Cyvers, suspects the involvement of North Korea’s infamous cryptocurrency hackers, the Lazarus group. He said, “The pattern and the characteristics of the (Indodax) attack highly resemble those of North Korea’s Lazarus Group.” (Arijit Sarkar / Cointelegraph)
Related: The Crypto Times, CoinDesk, Coinspeaker, cryptonews, The Crypto Basic, Coinpedia, BeInCrypto, Blockonomi
Golf course management and hospitality company Kemper Sports Management disclosed a data breach impacting the personal information of tens of thousands of individuals.
The firm told the Maine Attorney General’s Office that it became aware of suspicious activity on its network on April 1, 2024. An investigation revealed that a threat actor had gained access to systems storing personal information, including names and Social Security numbers, as part of a cyberattack.
KemperSports told the AG that the data breach impacted more than 62,000 individuals. A notification letter sent out to impacted people indicates that the compromised data was “primarily related to certain current and former employees.”
The company said there is no evidence that the information has been misused or used for identity theft or fraud, but impacted individuals are being offered one year of free credit monitoring and identity restoration services.
No known ransomware group appears to have taken credit for the attack on KemperSports. However, even if this were an attack conducted by a ransomware group, the company would not be listed on leak websites if it paid a ransom. (Eduard Kovacs / Security Week)
The secure cloud access startup P0 Security announced it had raised $15 million in a Series A venture funding round.
SYN Ventures led the round, with Zscaler and Lightspeed Venture Partners also participating. (Duncan Riley / Silicon Angle)
Related: FinTech Global, Business Wire, FinSMEs
Element Security, which has developed an exploit engine that continuously and actively attempts to hack their customers' external-facing assets, identifying high-impact exposures before attackers can exploit them, announced that it has raised $5 million in funding and unveiled its Continuous Threat Exposure Management (CTEM) solution.
The round included the Q Fund VC, Eddy Shalev, Danny Yamin (former CEO of Microsoft Israel), and Kobi Rosengarten (former General Partner at JVP). (CTech)
Related: FinSMEs
Best Thing of the Day: Wiping the Smirk Off the New Technological Face of White Supremacy
Federal prosecutors in California Dallas indicted Erin Humber and Matthew Robert Allison, who led the group known as "Terrorgram," a network of channels, group chats, and users on the app Telegram that functions as "the new technological face of white supremacist violence."
Worst Thing of the Day: We Know Where You're Going and What You're Talking About
Ford Motor Company is seeking a patent for technology that would allow it to tailor in-car advertising by listening to conversations among vehicle occupants and analyzing a car’s historical location and other data.
Closing Thought
,




