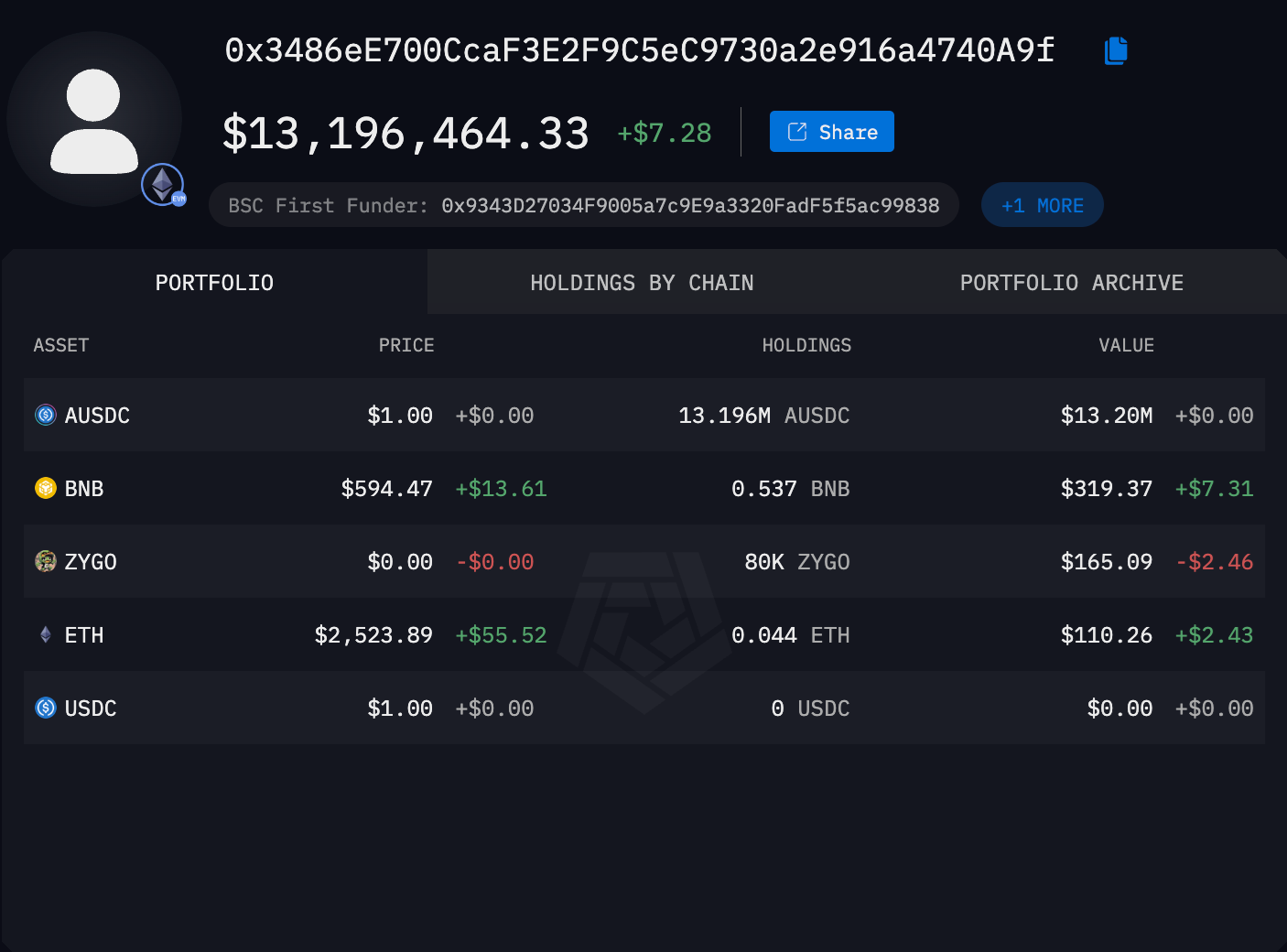
A Hacker Stole $20 Million from a Wallet Likely Controlled by the US Government
Biden issues national security memo on AI, UnitedHealth says 100M people affected by Change Healthcare data theft, Ukraine eyes creating Cyber Forces as armed forces branch, CFPB warns businesses about monitoring employees, Apple opens Private Could Compute materials to researchers, much more