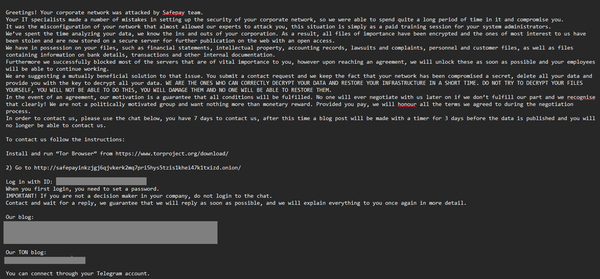
M&S and Qantas leaders remain mum on ransomware payments
M&S chairman says two other British companies' ransomware attacks have gone unreported, 5.7m customers impacted by Qantas attack, US sanctions DPRK man for IT worker scheme, DoJ seeks to bring COVID hacker to US, Rubio impersonated in AI voice effort, MSFT patches 137+ flaws, much more