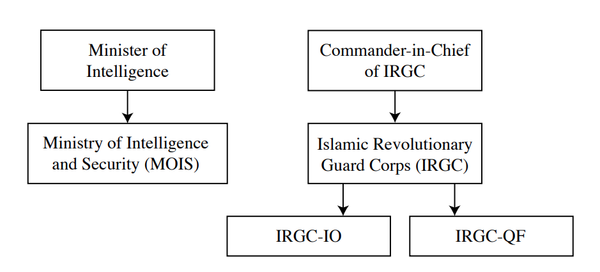
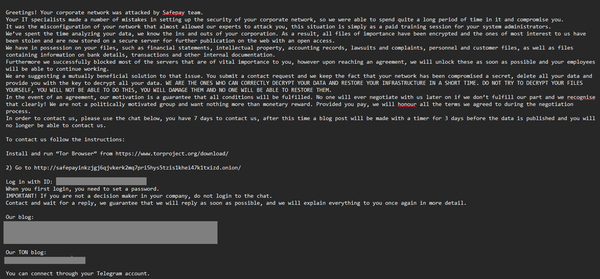
Data on UK SAS forces and MI6 officers exposed in massive Afghan leak
Google sues BadBox 2.0 ops, Salt Typhoon continues telco targeting, Paradox.ai developer used password of 123456 for Fortune 500 customers, EU sanctions Russians for disinformation campaigns, Qantas gains order blocking release of stolen data, FCC to bar Chinese kit from undersea cables, much more