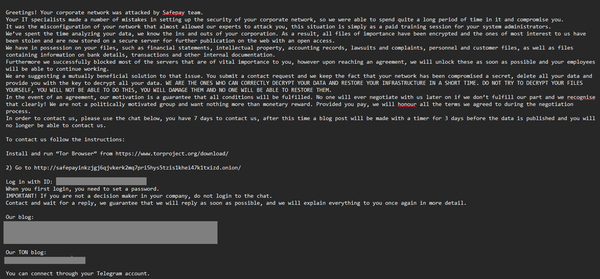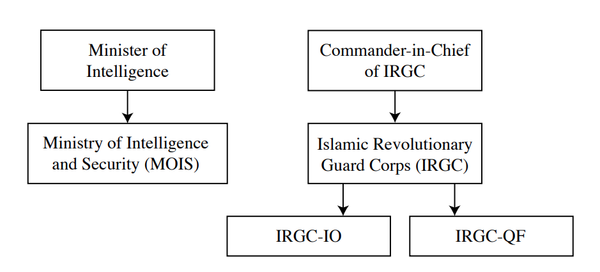
Parliament committee says UK is a hacking priority for Iran
Mexico AG launches probe into alleged NSO Group bribes of former president, Pakistan arrests 150 in cybercrime crackdown, Rowhammer attacks against GPUs are possible, Hackers exploit Wing FTP Server file flaws, Thief returns 90% of $2.2m swiped from Texture Finance, much more